I have heard for 7 years now: “I wish Microsoft would have allowed for multiple domain password policies in a single domain.” The wait is over! Microsoft’s next generation of server, codenamed Longhorn, will provide this very feature. It has been long awaited and one of the most requested features for Windows Active Directory. I hope you are not thinking that Windows 2000 or 2003 provides this feature? If you do, this article will clarify that misconception and dive into Longhorn’s capabilities in this area.
Implementing Domain Password Policies with Windows 2000/2003 Active Directory
During the installation of a Windows Active Directory domain controller, two Group Policy Objects (GPOs) are created. These GPOs are named Default Domain Controllers Policy and Default Domain Policy. The first, targeting domain controllers of course, is linked to the Domain Controllers organizational unit (OU), which is the only OU in a fresh installation of Active Directory. This GPO is primarily responsible for establishing user rights for the domain controllers, as well as some other miscellaneous security settings.
The Default Domain Policy, linked to the domain node during installation, has one responsibility by default. Yes, you guessed it, this GPO is responsible for establishing the Password Policies for all domain user accounts. The Password Policy section is only one of three different sections located under the master Account Policies section. There is also an Account Lockout Policies and Kerberos Policies section adjacent to the Password Policies section.
Within the Default Domain Policy, the settings that control domain user account passwords and lockout restrictions are set, as shown in Figures 1 and 2.
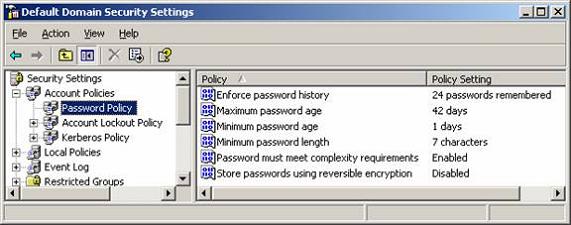
Figure 1: Password Policies settings
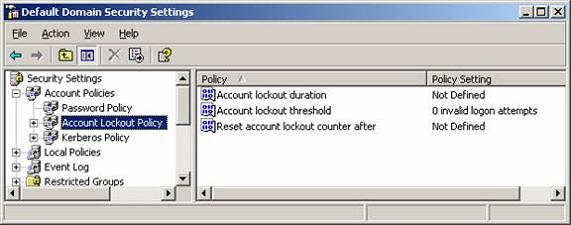
Figure 2: Account Lockout Policies settings
If the default values are not desired, they can be modified. One school of thought is that the Default Domain Policy can be updated to contain the desired Password Policies settings. The other school of thought is that the default GPO should never be altered. Instead, a new GPO should be created, linked to the domain, configured with the desired Password Policies (and other two sections) settings, then moved to have higher priority than the Default Domain Policy, as shown in Figure 3.
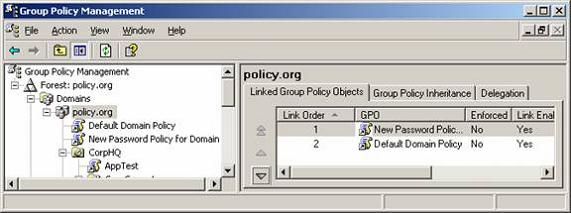
Figure 3: New GPO with higher priority is created to house Password Policies for all domain user accounts
Establishing Local Security Accounts Manager (SAM) Password Policies
If you are reading along thinking that Password Policies can also be set in a GPO that is linked to an new OU that you create, you would be correct. If you are thinking that these Password Policies settings in this new GPO would affect the user accounts that reside in that OU, you would be incorrect. This is a very common misconception on how Password Policies work in Windows 2000/2003 Active Directory domains.
The settings that are established in these GPOs don’t affect user accounts, but they affect computer accounts. This is clearly shown in Figure 1 above, where you can see that the Account Policies section is clearly under the Computer Configuration node in the GPO.
The confusion typically arises due to the fact that computer accounts don’t have passwords, but user accounts do. In this case, the GPO is configuring the SAM on the computer, which in turn controls the password restrictions for the local user accounts stored there.
I also need to clarify that the Password Policies settings established in a GPO linked to an OU DOES have higher precedence over the Default Domain Policy by default. Therefore, any settings that are made in the GPO linked to the OU will take affect over those at the domain level. This can be modified by setting the Enforced option for the GPO linked to the domain containing the desired Password Policies settings, as shown in Figure 4.
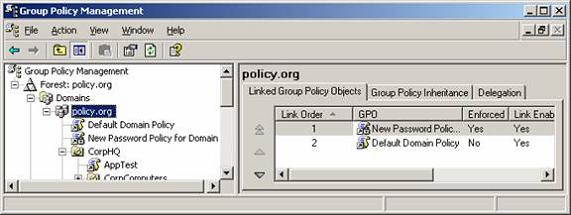
Figure 4: GPO linked to the domain with the Enforced option configured
Longhorn Domain Password Policies
In Longhorn, the concepts and actions of establishing password policies for the domain user accounts will be turned upside down. Multiple domain password policies are now possible for the same domain. Of course, this is a feature that has been desired for a long, long time… back to the Windows NT 4.0 days. I have heard for years: “I want to have the administrators have more complex passwords than the standard users in my domain.”
Now, you will be able to create custom password policies for any type of user in your environment. This might include users in HR, finance, executives, IT admins, help desk, etc.
The settings that you will have at your disposal are the same as within the Group Policy Objects today, it is just that you won’t be using Group Policy to configure them. With Longhorn, there is a new object in Active Directory that you will configure. This new object, the Password Settings Object, will contain all of the properties that the current Password Policies and Account Lockout Policies contain.
For implementation, you will create a new LDAP object named msDS-PasswordSettings under the new Password Settings container, which will have the LDAP path of “cn=Password Settings,cn=System,dc=domainname,dc=com.” Under this new object, you will fill out the information for the following attributes:
msDS-PasswordSettingsPrecedence – This is an important attribute which can handle the situation where a user has membership in multiple groups which have different password policies established.
msDS-PasswordReversibleEncryptionEnabled – Toggles whether or not reversible encryption is enabled.
msDS-PasswordHistoryLength – Determines how many passwords must be unique before it can be reused again.
msDS-PasswordComplexityEnabled – This establishes whether the password requires 6 characters, 3 of 4 types of characters, and denies having the password being the logon name.
msDS-MinimumPasswordLength – Establishes the minimum length of the password.
msDS-MinimumPasswordAge – Determines how long the user must use the password before changing it.
msDS-MaximumPasswordAge – Determines how long the user can use the password before they are required to change it.
msDS-LockoutThreshold – Determines how many failed password attempts will be allowed before locking out user account.
msDS-LockoutObservationWindow – Determines the time after which the bad password counter will be reset.
msDS-LockoutDuration – Determines how long the account will be locked out after too many failed password attempts.
Once all of the attributes are configured, you will link this new object to an Active Directory global group. This process of linking is accomplished by adding the LDAP name of the group to the msDS-PSOAppliesTo attribute.
Summary
Longhorn will come with some new features, technologies, and methods for controlling and managing objects within your enterprise. By far one of the most impressive and soon-to-be-popular features of Longhorn will be the ability to establish multiple password policies for a single domain. You might want to start thinking about how this will affect your current environment, and begin planning for what you have wanted for a long time.



