
Cybersecurity was on everyone’s lips throughout 2022, and for a good reason. The US Cybersecurity and Infrastructure Security Agency (CISA) reported a whopping 62% yearly increase in cybercrime cases between February 2021 and February 2022.
Surprisingly, the types of cybercrime cases committed have become more basic. Today, simpler hacks, scams, and attacks are more prevalent than sophisticated cracks and breaches.
Overall, 3 novelties exist when it comes to cybercrime in 2022 compared to previous years:
- Huge focus on crypto
- More distributed attacks on smaller companies
- Increased diversity in identity theft scams
The new dangers aren’t really new. Good cybersecurity strategies would deal with almost all of them with ease.
However, the opportunity for cybercriminals to find and exploit soft targets has increased with the switch to working online. Now, the industry must get up to speed and improve cybersecurity overall.
I’ll start by looking at why cybersecurity is important and why you should always consider it.
Why Is Cybersecurity Important?
Many people can’t imagine someone using their data to steal from them. And that’s what cybercrime is in essence—theft.
For instance, financial cybercrimes can steal money directly from you. Your personal and business information can also be used to siphon funds. Cybercrimes can also include industrial espionage, where cyber criminals steal ideas, patents, and even customers.
Cybersecurity protects you from malicious entities online. Good cybersecurity measures secure your information. They could also make it costly for cybercriminals to access your information.
Thankfully, it’s easy to establish a good cybersecurity system, whether you’re tech-savvy or not. Many human-based solutions, user-friendly tools, and options are accessible to anyone.
First, I’ll go through the most common types of cybercrime in 2022. Then, I’ll showcase the top 5 cybercrime cases.
Most Common Types of Hacks and Malware
The following hacks and malware types made up most attacks in 2022. And, as you might notice, some are very simple.

1. Phishing Attacks
Phishing involves using trustworthy emails or web pages to scam people into clicking the link or providing their personal information. Successful phishing attacks allow cybercriminals to steal your money or identity.
With current security software and knowledge, the success rate of phishing attacks is incredibly low. But with 100+ million attacks daily, it’s no wonder some attackers manage to reach their target. Even large companies such as IKEA can get affected.
2. Vishing Attacks
Vishing is phishing attacks over the phone. With many e-commerce companies emerging, some of the oldest tricks in the books are returning in cybercrime fashion. This kind of attack was popular against banks roughly two decades ago when e-banking had just started. Now, it is experiencing a comeback in e-commerce.
In most cases, the attack starts with identity theft. A cybercriminal will know the name and email address of the target but little else. They’ll use social media and what the target has been shopping for and call the vendor to give out more information or change the delivery address and email.
In turn, this can lead to further identity theft, or the criminals can switch the delivery location to steal the package.
3. Distributed Denial of Service Attacks
Distributed denial of service (DDoS) attacks are fairly simple. That’s why many cyber criminals use them. DDoS attacks use thousands of bot accounts to access the web page at the same time, thus denying access to others and even bringing the website down.
While these attacks don’t steal your data or breach your network, they affect a company’s entire online database. They also can be a smokescreen for a data breach or ransomware attack.
The development of new processors and increased interconnectivity on the dark web (non-indexed internet) has made DDoS attacks much easier to initiate. A high-end processor can start thousands of self-executable apps (bots).
Roughly three-quarters of companies reported DDoS attacks in 2020. And, in 2022, it looks like the number isn’t going to decrease. Thankfully, most attacks were stopped because virtually all new server operating systems have preventative measures.
4. Identity Theft
Cybercriminals steal your identity to use your private information and good name to access various services or goods. A person with your credit card information can use it to buy things or send money abroad.
Identity theft most commonly occurs when victims share their information through social media or phishing attacks. If a company that stores your information becomes a victim of cyberattack, your identity can also be stolen.
Organizations, like the Canadian Bankers Association, have published a guide on how to spot identity theft scams. Unfortunately, increasing awareness is the only way to stay safe from identity theft.
5. Ransomware Attacks
Ransomware attacks happen when you’ve already fallen victim to phishing, vishing, or email scams. The criminals take your sensitive data and hold it until you pay.
Cyberattacks often use a few methods together. Once you click on a phishing link, it may start downloading an executable file. Alternatively, the link may trick you into disclosing your private information. Then, with that information, cybercriminals can gain access to your system and download your personal and business files.
Cybercriminals may also keep your information for ransom or change the passwords and hold your entire system at ransom.
In 2021, the average cost of a ransomware attack was roughly USD170,000, according to some reports. And, the targets are no longer huge corporations that have an easier time paying. Now, small enterprises and even individuals are attacked as well.
I’ll now go through the top attacks of 2022. These attacks are a reminder that not even the biggest companies are safe from attacks.
Biggest Cybercrimes of 2022

The list of successful cybercrimes in 2022 is large. Even scarier is that most companies wouldn’t disclose that they suffered an attack if they could hide it.
We can divide big attacks in 2022 into two types: financial and vanity attacks. In financial attacks, the criminals managed to get away with a lot of money and even more personal information. In vanity attacks, the cybercriminal targets a tech giant to prove a point, even though they may steal nothing
Crypto.com
Starting the year with a bang, Crypto.com, an online app and platform meant for trading cryptocurrency, was hacked on January 17.
As reported by Forbes, almost 500 crypto wallets were targeted by going around the 2-factor-authentication (2FA) and removing USD30+ million in cryptocurrency.
Initially, the platform reported the event as an incident. But once it was found out that criminals stole USD18+ million in Bitcoin and USD15+ million in Ethereum, the company was forced to reimburse the attacked accounts.
The perpetrators weren’t found, and no group has ever claimed responsibility for the attack.
Ronin
Late last year, Ronin’s Axie Infinity game that allows earning digital currency rolled back some cybersecurity measures to accommodate the rapidly growing player base. Cybercriminals took advantage of that and stole USD600+ million in cryptocurrency.
This cyberattack lasted almost five months and was found only in March 2022. It’s considered the biggest cyberattack of this year. Some reports say the hack was conducted through a false LinkedIn job offer.
Thankfully, the funds have been found and recovered. The discovered vulnerability left a sour taste for many Ronin players, though.
Microsoft
The attack on Microsoft was a vanity attack. The focus wasn’t on stealing personal information or money. Rather, the attackers wanted to damage the company’s reputation.
The international cybercrime group, Lapsus$, breached the Azure DevOps server. They also downloaded 37 GB of source code from the cloud computing software.
Lapsus$ also claimed to have downloaded 90% of the Bing search engine source code and shared it with 50+ thousand people following their account on Telegram. Microsoft reported no major damage and said that the vulnerabilities have been amended.
Red Cross
The Red Cross is a huge global employer and holds sensitive medical data in its records. In January, the organization was under attack, and 500+ thousand records were compromised.
As stated by the organization, the criminals stole information from “highly vulnerable people,” frequently victims of war and possible witnesses. This information can be sold to international crime rings, which frequently target these people.
Authorities couldn’t identify the assailant, and the organization placed its servers offline for some time to prevent further attacks and remove the vulnerability.
Cash App
The attack on Cash App, a popular payment tool, didn’t come from a previously unknown digital vulnerability or a cybercrime campaign. Rather, a disgruntled former employee accessed the company’s servers and shared the users’ personal information.
The breach didn’t include any credentials. It only had a limited impact before it was discovered. Still, the attack compromised the names, trading information, and stock portfolios of 8+ million users.
This information could allow digital crime organizations to access user bank accounts, conduct identity theft, and gain entry to social media accounts.
Now that we know the types of crime to expect and that even the biggest companies can be an issue, I’ll go through some solutions to help you protect your company from attacks.
Top Tech to Prevent Cybercrime

It’s virtually impossible to be 100% certain that you’re safe from every possible attack. Vulnerability to cybercrime exists on three levels. The attack can focus on your hardware, software, and, most importantly, on the people using the devices.
Hardware attacks introduce a vulnerability to your firmware. On the other hand, software attacks aim to compromise an app or system. Cybercriminals also target people, because these people often don’t have the training to identify scams.
Thankfully, you can test how your system is doing and check if you’ve covered as many angles as possible by using a software tool.
GFI LanGuard Patch Management
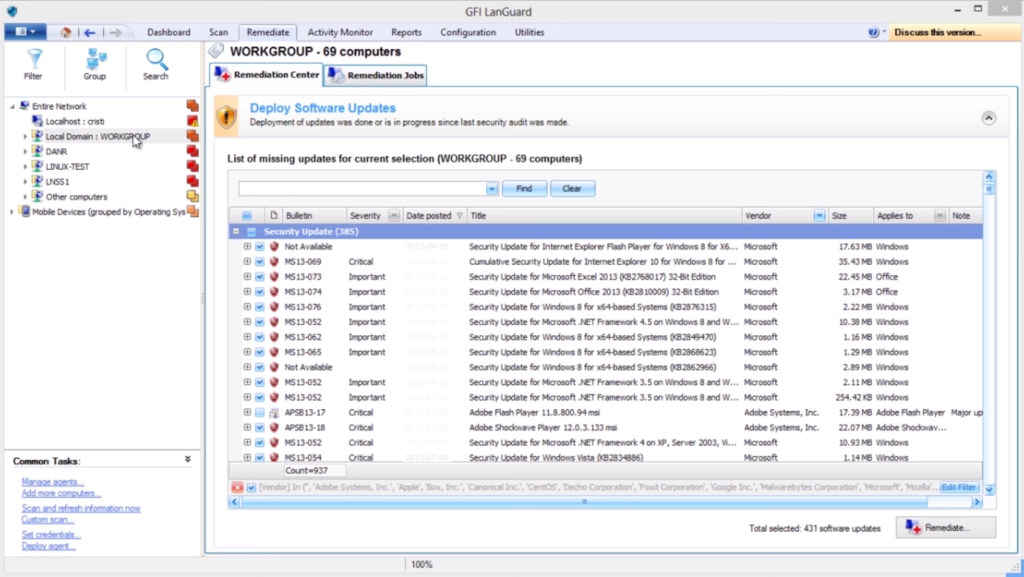
GFI LanGuard has limited scope for solving the issues with your system. That said, it’s unsurpassed when it comes to finding out the issues and testing the solutions. Currently, it tracks 60,000+ possible vulnerabilities and a long list of compliances.
The app scans your system and detects issues. These issues include possible and known vulnerabilities, missing updates, issues with network devices, security audits, and compliance with standards such as PCI, HIPAA, and others.
Additionally, the app gives a detailed report about all the issues it has found and possible pre-determined solutions, such as updates. It’ll also work with a vast array of third-party software to solve any persistent issues.
Finally, you can run virtual environments such as VMware or Citrix through LanGuard and test solutions and problems without affecting the regular workflow.
Cloudflare
Cloudflare has been around for a while and is popular with many businesses. It’s fairly easy to use, especially for small businesses, and it can secure websites, APIs, and internet apps with tested solutions.
The app itself won’t test for vulnerabilities and provides a limited set of solutions. But, when it comes to e-commerce websites, all that is needed is present inside Cloudflare.
Additionally, the app can write and deploy code where necessary. This means you can implement customized solutions on the website.
The list of options might seem short for established businesses. But for small e-commerce enterprises, it’s a quick and easy solution to virtually all their problems.
Checkpoint

Checkpoint might seem inferior to the other two solutions because it isn’t a single comprehensive software. Rather, it offers solutions separately. Regardless, everything most SMBs would need is here.
Checkpoint offers solid cloud security options, including developed solutions for AWS, Azure, and Google Cloud. Checkpoint also has advanced network solutions and specialized defenses against phishing and ransomware.
For those who require it, the company also offers industry-specific solutions. This includes HIPAA compliance and other compliances for the financial, education, and telecommunication sectors.
See the table below for a quick summary of the 3 top solutions to prevent cybercrime and how they compare.
| GFI LanGuard | Cloudflare | Checkpoint | |
| Features | ⭐⭐⭐⭐⭐ | ⭐⭐⭐ | ⭐⭐⭐⭐⭐ |
| UI | ⭐⭐⭐⭐⭐ | ⭐⭐⭐⭐ | ⭐⭐⭐⭐ |
| Compatibility | ⭐⭐⭐⭐ | ⭐⭐⭐⭐ | ⭐⭐⭐ |
| Price/Value | ⭐⭐⭐⭐ | ⭐⭐⭐⭐ | ⭐⭐⭐ |
Final Words
In 2022, cybercrime is on the rise. The number of cases has risen significantly, and multi-million dollar cyber thefts have been occurring from the beginning of the year.
Since we rely on digital goods and services in today’s modern economy, the need for cybersecurity has become even more apparent. According to experts, more and more people need cybersecurity, but the number of cybersecurity experts isn’t growing.
The good thing is that cybersecurity software can help any company prevent cyberattacks on their devices, employees, and servers. Picking out a good set of cybersecurity solutions would always be a good thing. It doesn’t matter how long you’ve been in business or how big your company is.
Do you have more questions about cybercrimes in 2022? Check out the FAQ and Resources below.
FAQ
What are the biggest cybercrime threats in 2022?
The biggest cybercrime threats for individuals and businesses in 2022 are phishing attacks and email scams. Some phishing operations, such as the Facebook phishing attack, affected millions of people at once. These cybercrimes affect the most people and do so frequently.
What is the biggest cybersecurity threat today?
Although phishing attacks and email scams are the biggest external cybersecurity threat, most cyberattacks are successful due to the human element, which is still the biggest issue for most companies and individuals.
What was the biggest cybercrime attack in 2022?
So far, the most expensive cyberattack in 2022 was the Ronin hack, costing over $600 million in cryptocurrency. But, the Spring4Shell type vulnerabilities affecting zero-day cybersecurity might be even more important in the long run. That’s because they focus on the infrastructure and can stay dormant for years.
What do cyberattacks most frequently target?
Most cybercriminals would focus on financial targets directly if they’re within their reach. Financial targets can generally garner more cybersecurity, making an attack more expensive.The most common target is personal information, such as medical information, financial information, and other discerning data. This information can be used for either commercial purposes or identity theft, making it very valuable for cybercriminals.
Can you steal an identity from a business?
Yes, it’s possible. It also happens quite frequently. Similar to attacks on individuals, business information can be misused to access financial records and steal money. Alternatively, the information can be used to target affiliated entities such as customers and clients, which can be even more destructive.
Resources
TechGenix: Newsletters
Subscribe to our newsletters for more quality content.
TechGenix: News
Explore the latest news from the tech world.
TechGenix: Article on Governance, Risk, and Compliance
Learn more about governance, risk, and compliance and their role in securing organizations.
TechGenix: Article on Data Privacy Regulations
Discover more about different data privacy regulations and how you can safely navigate them.
TechGenix: Article on Artificial Intelligence in Cyber Security
Learn more about the benefits and drawbacks of AI in cybersecurity.




This is one of the best website in order to learn about cybersecurity. But, I want more detailed cases and cyberattacks that happens on individuals and company so that I can be able to understand different malwares which use to detect attacker and softwares which help us to keep us safe from compromising our personal data.