Like most technologies, applications will be vulnerable in the future or are vulnerable right now. If hackers discover these vulnerabilities first, your IT systems will be subject to attack, causing reputational damage and loss of business. As applications become the backbone of an organization’s infrastructure, any hacking of your apps has the potential to cause extensive damage to your business. Hence, the relevance of vulnerability testing.
What is vulnerability testing?
Vulnerability testing is a process by which security loopholes in the infrastructure are detected and classified. This is what Marty Bishop and his team did in the movie “Sneakers,” though our technological capabilities now are further along than they were in the early 1990s, but this is another topic. As far as applications go, they first need testing against a standard set of risks as defined by organizations like the Web Application Security Consortium (WASC) and the Open Web Application Security Project (OWASP).
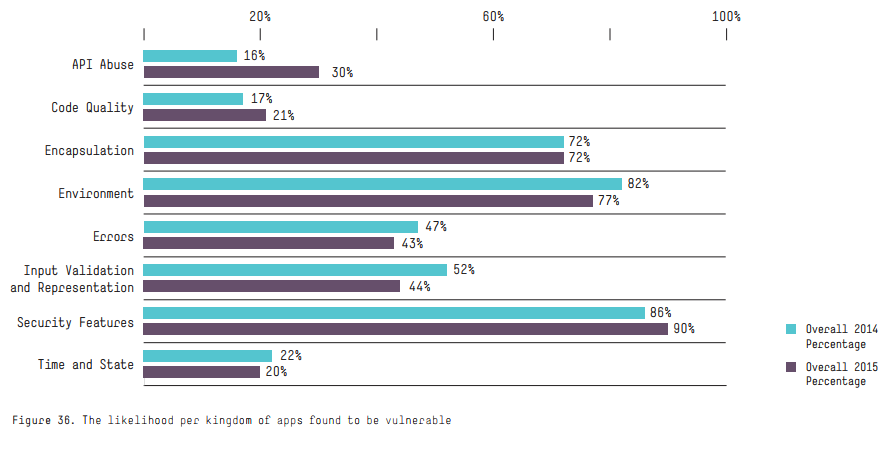
Vulnerability testing vendors also propose measures to eliminate these vulnerabilities and execute validation testing to confirm that the related security problems have actually been resolved. As per the HPE Cyber Risk Report 2016, a significant percentage of applications have struggled with well-documented security issues for years now, as seen in the figure below.
What are the steps in vulnerability testing?
Vulnerability testing encompasses several steps:
- Definition of the objectives or goals of the process: Depending on the client’s requirements, the vendor sets the boundaries for the assessment and also lists the resource requirements for the testing.
- Gathering of all required information on the application or application suite including business logic, special requirements, etc.
- The assessment vendor uses tools to bring to the surface deep-rooted weaknesses. Complicated flaws would require manual penetration testing to be performed.
- Analysis, documentation, and reporting of the vulnerabilities discovered.
- Other tools provide guidelines to fix the vulnerabilities found and also perform validation testing to ensure that issue resolution has happened.
- If the vulnerability cannot be resolved quickly (as is often encountered), other tools can help you fix it with a policy change in the WAF (Web Application Firewall) layer.
The advantage of this approach to fix it is that this provides a platform to monitor the source of any attacks and deflect or block any future attempts by attackers to take advantage of the vulnerabilities in the application. It does not matter if another country (China, North Korea, for example), company, or even an individual is trying to gain entry into your system.
Why does vulnerability testing matter to you?
It is commonly believed that if projects follow the standard software development life cycle (SDLC), the vulnerability aspect is also taken care of. However, this is not the truth. Vulnerability testing demands a separate focus and approach. This falls under the bucket of security testing. So, what are the risks of not performing vulnerability testing?
Loss of reputation and customers

Reputational risk is one of the biggest problems that gets exposed as a result of incomplete vulnerability testing. With reputational loss comes loss of customers. Customers don’t take kindly to data breaches. This leads to a situation where even long-standing customers can terminate business relationships.
According to a survey by OnePoll, more than 80 percent of the surveyed sample mentioned that they would in all likelihood not do any business with any organization where a data leak has happened. All it takes is one successful attack to bring down your reputation built painstakingly over many years.
Financial damage
Cases of hack attacks that exploit loopholes can be extremely painful in terms of financial damage. Courts are very harsh when it comes to awarding financial settlements to victims of data theft. In one particular case, Anthem ended up paying more than $100 million in one of the largest settlements ever for a data breach — and this is nothing to smile about when considering the mandatory costs of doing business such as R&D, high taxes, employee costs, and other factors that all businesses must deal with. While terrible settlements like this take a bite out of your checking account, there are financial losses in other forms, too. Stock prices go down, sales can take a hit, and user activity can decline.
And you may even be ridiculed on late night goofy TV, which some people still watch, but that is another subject. Regardless, you do not want your business to go through this experience.
How to tap vulnerability testing effectively
While most business owners do understand the risks that arise from compromised applications, not everyone understands the importance of comprehensive testing.
Automated testing tools can help, but most complex applications require a comprehensive approach beyond this. To detect all the security loopholes, you need to include manual penetration testing as part of your approach. Testing OWASP standard vulnerabilities is only a starting point. It’s only manual penetration testing that can uncover intricate and complex flaws.
Let’s look at a few scenarios that would be missed by automated tools:
- A typical e-commerce site permits users to add items to the cart, look at a summary page, and then complete the transaction. How would it be if a hacker could browse back to the summary page, and while maintaining the same session, use an injection to update a lower cost for one of the items and then complete the transaction?
- How would it be if a user could keep a unique item in a shopping cart forever and prevent others from purchasing it?
- Is it possible for a user to keep an item in a shopping cart at a currently discounted price and then complete the actual purchase after many months?
- How would it be if a user could purchase an item via a loyalty account and have the loyalty points credited, but then cancel the transaction before it could be completed?
These are just some of the scenarios that automated security testing tools would not be able to pick up on. There lies the importance of manual penetration testing done by security experts.
Web application testing along with manual penetration testing
And finally, here’s our 12-step program for manual penetration testing your web applications.
- Target reconnaissance: Here, the application is analyzed at the surface level for a first level check.
- Business process and application logic mapping: This is the process in which the business process and application logic associated with the application are analyzed thoroughly.
- Configure testing tool.
- Automated website crawling.
- Manual website crawling.
- Automated unauthenticated scanning using tool.
- Automated authenticated scanning using tool.
- Manual web vulnerability testing.
- Exploitation of the web vulnerabilities.
- Review of results and false positives.
- Assessment of business risks.
- Create documentation and publish results.
Photo credit: Shutterstock



