Introduction
Ever since Microsoft has released the latest versions of their Windows Firewall, there has been confusion as to “which network” should I configure and when? To make things worse, Microsoft changed the names of these configurations, but not the definitions. I felt it was necessary to clarify when you would configure each setting and what each setting actually does. After this article, I hope that you will be able to configure Windows Firewall settings for your servers and desktops, knowing that they will all function properly no matter what “network” they are apparently connected to.
Where You Will Find These Settings
There are multiple locations where you can find the “network” settings associated with Windows Firewall. From the same location of Windows Firewall configuration, you can find the “network” settings for which you need to configure how the computer is connecting to “a network”.
Control Panel – Windows Firewall Applet
Generally, you will find these settings within the Windows Firewall applet via the Control Panel. Of course, with the changes in the names and overall GUI for Windows Firewall over the past operating systems, each operating system will look a bit different. Since most organizations are moving to Windows Server 2008 and Server 2008 R2, as well as Windows 7 for the desktop, we are going to focus on these three operating systems.
Windows Server 2008: Control Panel – Windows Firewall applet
Windows Server 2008 is relatively new, but it still has some older interfaces which are just not fully developed and this is especially true for the “network” configurations. When you open up the Windows Firewall applet on Windows Server 2008, you will see an interface similar to that in Figure 1.
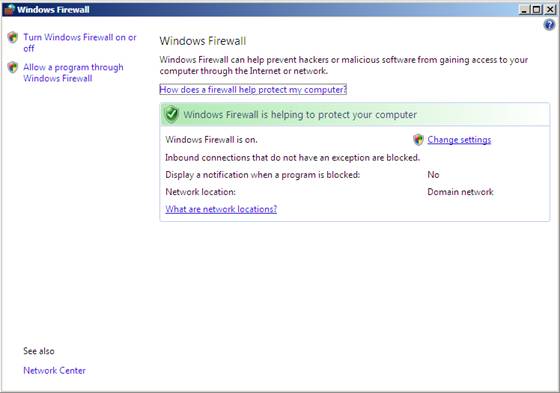
Figure 1: Windows Server 2008 Windows Firewall applet.
Notice in Figure 1 that you can see the network location (it is stated as “Domain Network”), but you don’t see the configurations for the other network options. You do have a link labeled “What are network locations?” which will take you to a page describing each type. We will cover these options in the next section.
Windows Server 2008 R2 and Windows 7: Control Panel – Windows Firewall applet
Microsoft made some dramatic changes to the Windows Firewall interface with Windows Server 2008 R2 and Windows 7. Now, all three of the network location settings are displayed within the Windows Firewall applet through the Control Panel, as shown in Figure 2.
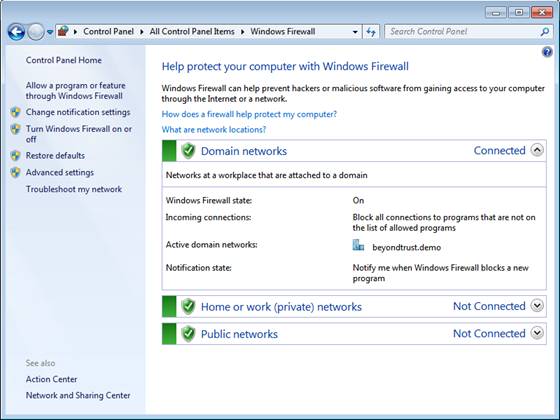
Figure 2: Windows Firewall applet for Windows Server 2008 R2 and Windows 7.
Windows Firewall with Advanced Security
Another location you will find the network location settings for your Windows Firewall is via an Administrative Tool named “Windows Firewall with Advanced Security”. This tool is new, and is consistent from Windows Server 2008 up to the newest operating systems. Therefore, this might be the best location to go to look for how the three settings are configured. When you launch the Windows Firewall with Advanced Security option through the Administrative Tools menu option, the resulting Window will look like the one shown in Figure 3.
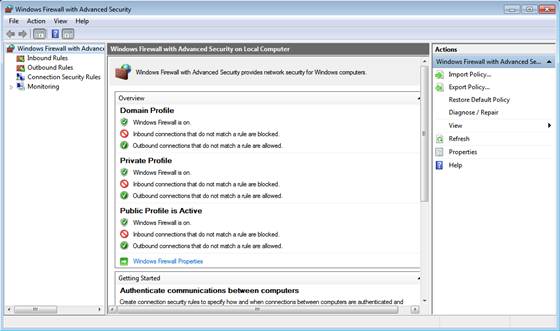
Figure 3: Windows Firewall with Advanced Security Interface
You can configure the network location options by clicking on the link at the bottom of the Overview section labeled Windows Firewall Properties, which will open up the Window shown in Figure 4.
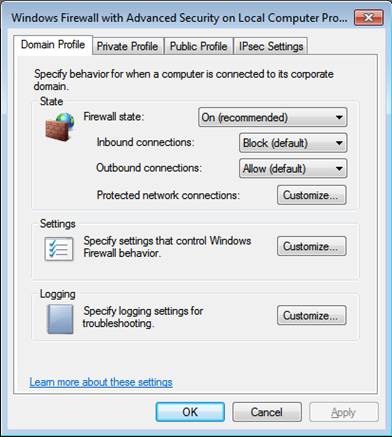
Figure 4: Windows Firewall Properties page.
Windows Firewall Network Location Definitions
There are currently three network location options: Domain networks, Home or work (private) networks, and Public networks. These are relatively obvious, but the confusion is still there, so let’s look at each of the definitions and details around each option.
Domain Networks – This setting is applied when the computer is connected to a domain controller, which is controlling a Windows domain.
Private Networks – This setting is applied when a connection to a network for which the computer’s account is not associated with. This can be a different domain or home network. A computer can only be joined to one domain at a time, so if the computer is not joined to the Domain network, it can only be joined to a Private or Public network. It is suggested that the Private network profile of settings be more restrictive than the Domain network profile of settings.
Public Networks – This setting is applied when a connection to a domain is made through a public network, such as at an airport, hotel, or coffee shop. Since the security of these networks is unknown and not really controlled by the user running the computer, it is suggested that the Public network profile of settings be more restrictive than either the Domain network or Private network.
Benefits of different “Networks”
The reason for having these three network options is the fact that you can configure network and firewall rules for each network individually. So, as a computer moves from one environment to another, or a domain is available or disconnected, the computer security and network behavior will change automatically.
The firewall settings for each “network” type can be configured either locally using the Windows Firewall with Advanced Security interface or by using Group Policy via Active Directory. Either method will result in a computer increasing security when the “network” they are connected to changes. You can see the Group Policy interface for configuring the three network settings in Figure 5.
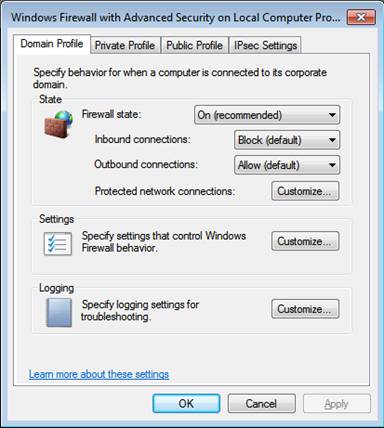
Figure 5: Network profile settings via Group Policy.
Since there is the ability to control each profile, firewall rules, and connection security rules locally or via Group Policy, there are settings that give admins control when there might be a dispute between the two. Each profile has customization options which allow for merging of the firewall rules and connection security rules. You can find this by clicking on the Customize button under the Settings section of the interface shown on Figure 5. The resultant interface is shown in Figure 6.
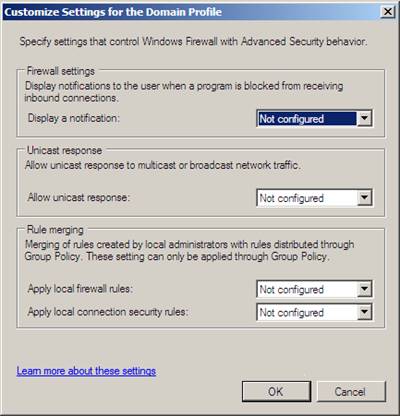
Figure 6: Controlling local and Active Directory based network settings.
Summary
Computers are mobile and ever changing from one environment to another. The ability to have control over security settings and network connections depending on the computer’s current network affiliate is extremely powerful. Microsoft did a great job providing the three different and appropriate network profiles: Domain, Private, and Public. Each network profile is dynamic, in that it recognizes how the computer is connecting to the network and changes automatically. Since each profile is associated with its own set of configurations, each profile can be tweaked to harden or soften security. Primarily, the security is controlled by configurations of the Windows Firewall, which is fully integrated with the three network profiles. By using these network profiles a corporation can help ensure that computers are more secure when the computers are not connected to the corporate domain.





Hello,
Your attempt at clarifying things is commendable, but it only works if you write clearly and proofread what you write.
“This setting is applied when a connection to a network for which the computer’s account is not associated with.”
makes no sense whatsoever.
It’s agood topic , my question is that :
from the mentioned windows screens , can I let the windows firewalls for all connected servers ON staus or OFF enven if some one change them manullay.
waiting for urgent answer.
best regards
Khater