The Dridex Trojan, a banking Trojan, has caused a significant amount of damage in recent history. Sent via mass email (in the hundreds of millions), Dridex primarily targeted Europeans with the intention of stealing personal information via HTML injections. Until recently, however, the Dridex bank Trojan has been more or less dormant since a botnet affiliated with Dridex was disrupted in June. This has since changed, as security researchers are reporting a sudden resurgence in cases involving the Dridex Trojan.
According to a Proofpoint report, researchers observed “on August 15 and 16, the largest observed campaign since the middle of June delivered tens of thousands of messages, primarily targeting financial services and manufacturing organizations.” The report pointed out that this was obviously not close to “the multimillion-message campaigns of May 2016,” but nevertheless the spike is a major cause for concern.
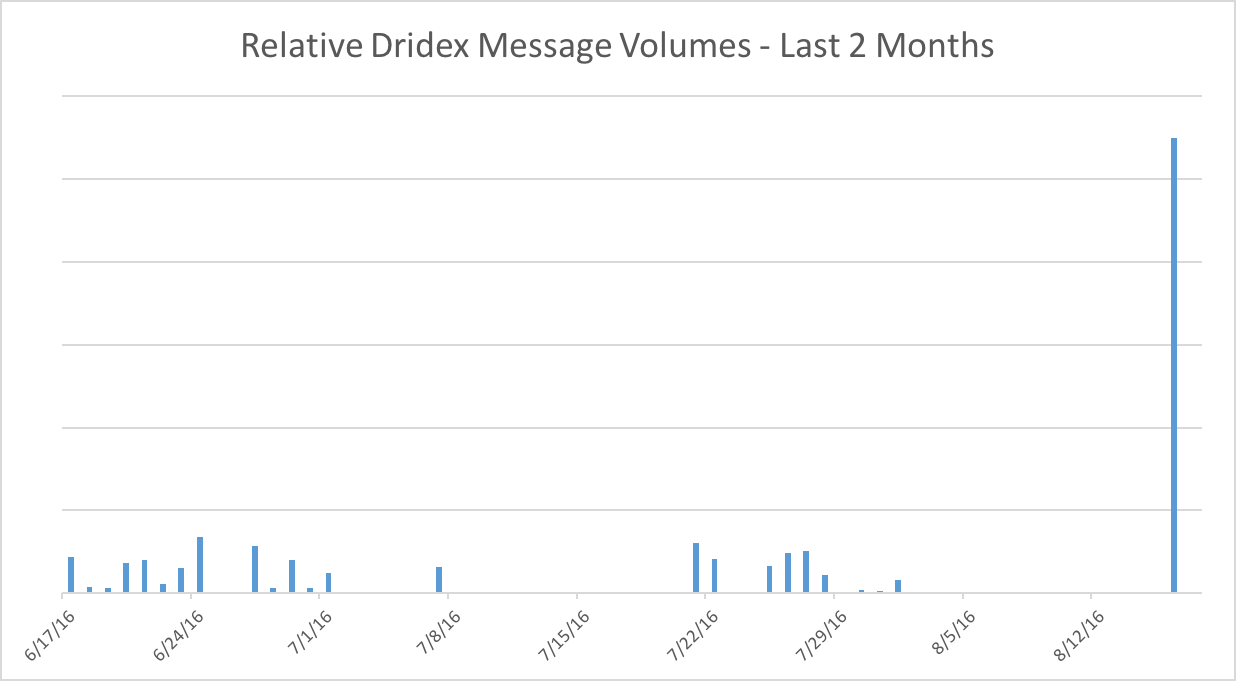
The attacks yet again were focused on countries (currently or formerly) in the European Union including Switzerland, France and post-Brexit U.K., but also focused on Australia and the United States. The emails in question used a baiting subject line that said “order confirmation,” “Lieferung” (German for delivery), and also random company names. The emails came with attachments for Word documents as well as .zip files.
Proofpoint researchers draw the conclusion that “these large campaigns may have saturated many target countries, Dridex actors are still looking to monetize the malware by targeting a smaller number of large organizations, many in financial services.” The question remains, however, as to who is utilizing this banking Trojan. One would think the botnet disruption might have given at least a sliver of knowledge regarding the threat actors’ identities. It is possible that the number of actors is insurmountable, but at least finding a few of these cyber-criminals would pinpoint a source.
New banking Trojans are coming into play quite often these days, but with Dridex’s popularity and longevity in terms of use, it is imperitive that security researchers keep digging for answers. Blocking the malware is only half of the battle, as people are still being duped into believing malicious emails.
Potentially millions of dollars and countless amounts of personal data are up for grabs if we fail.
Photo credit: Proofpoint



