
Source: Pexels
GoTo, LastPass’s owner, has updated that attackers may have stolen encrypted keys and backups during the Nov. 30 attack. GoTo’s investigation has also revealed that Central, Pro, join.me, Hamachi, and RemotelyAnywhere are among the products from its suite that were affected by the attack.
Immediately after the attack, LastPass’s CEO Karim Toubba stated: “Our customers’ passwords remain safely encrypted due to LastPass’s zero-knowledge architecture”. But now it seems that the timing of that statement may have been a little premature. Although LastPass — the credentials management company — is owned by GoTo, the company enjoys a standalone status.
Despite this, they share the same third-party cloud storage provider — which the investigation has found to be the real point of the breach. However, this hasn’t prompted GoTo to disclose the provider’s name. Regarding the stolen information, GoTo’s update said that it “include(s) account usernames, salted and hashed passwords, a portion of Multi-Factor Authentication (MFA) settings, as well as some product settings and licensing information.”
GoTo Attack Details

Source: GoTo
GoTo hasn’t divulged the encryption it used for the stored backups. But this is vital information, as encryption mechanisms make a difference. For example, if the company used symmetrical encryption, such as AES, it would be possible to decrypt the backups using the stolen keys. The information contained within the encrypted backups includes:
- Central and Pro account usernames
- Central and Pro account passwords
- Deployment and provisioning information
- One-to-Many scripts
- Multi-factor authentication (MFA) details
- Licensing and purchasing data (emails, phone numbers, billing address, and last four digits of credit card numbers)
In response, GoTo reset all passwords and migrated affected customers to an enhanced identity management platform. This has become a standard procedure in cases of sensitive customer information breaches. Identity management platforms allow for enhanced controls, stronger passwords, and single sign-on (SSO) options.
GoTo is still working with the same security firm (Mandiant) that it hired immediately after the attack for the investigation. The firm now claims the attackers didn’t gain access to any of GoTo’s internal systems. Offering GoTo’s customers some reassurance, the firm revealed that the company secures all business communication in transit. For instance, it’s secured with end-to-end encryption (E2EE), peer-to-peer (P2P) technology and transport layer security (TLS) encryption. These are important communication-securing technologies that prove useful in mitigating the fallout from such breaches.
Password Management and User Credentials
Source: MyWot
GoTo offers a range of communications tools for business owners, from VOIP and video conferencing to remote support. While GoTo hasn’t disclosed the number of affected accounts in its update, its customers exceed 800,000. LastPass, bought by GoTo and later given a standalone status, has 30 million people and 85,000 businesses worldwide using its credential management services.
Breaches like this have dire consequences and paint a bleak picture of the online security landscape. In the aftermath of the attack, cybersecurity researchers lambasted LastPass for its tall claims and handling of the situation. LastPass’s CEO went on claim that it would take “a million years to crack a master password using password-cracking technology.”
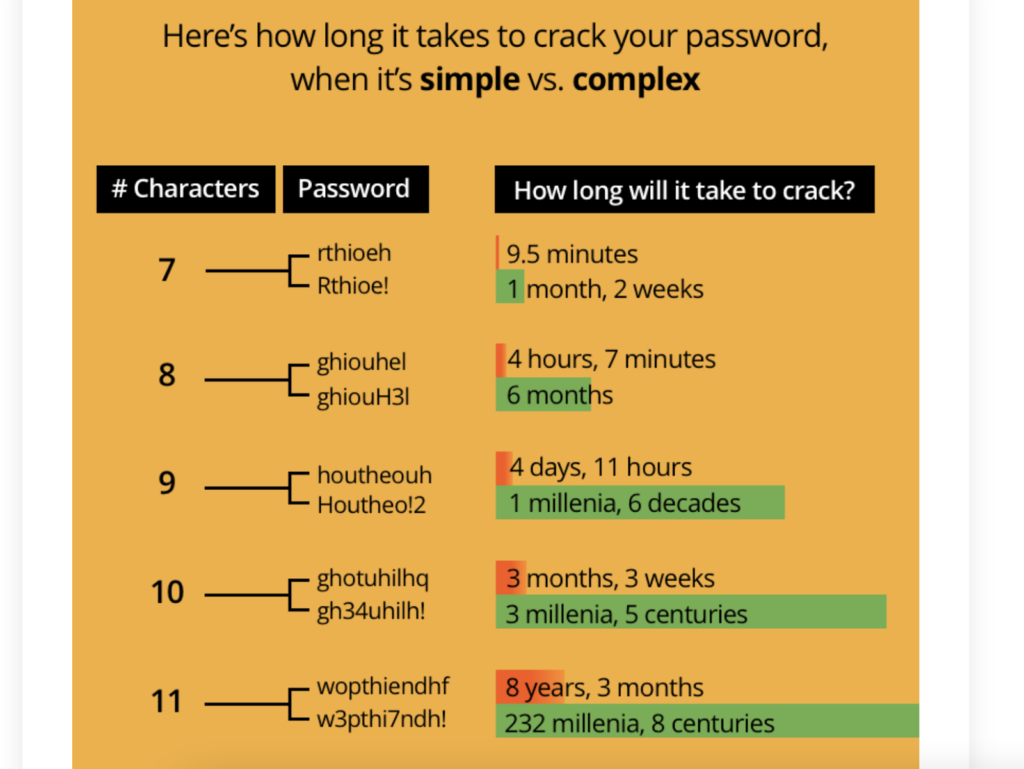
Though that claim has some truth, it applies more specifically to 12-character passwords — not 8-character ones that LastPass uses. Moreover, master passwords would contain random characters strung together instead of made up of words, which are easily guessed. A US watchdog recently demonstrated how easy it was to crack such passwords using password-cracking rigs.
GoTo salts and hashes its stored passwords. This is useful because even though a cybercriminal can use a password-cracking rig to decrypt these passwords, the user can quickly change them in response to an intrusion. Most people don’t take their password complexity seriously as an important feature of online security. Consider that it might take 0.29 milliseconds to crack a 7-character password consisting of all lowercase letters. But, it could take nearly 200 years to crack a 12-character password of mixed lowercase letters. An additional character adds exponential complexity to the password.
The Zero-Knowledge Question
Source: LastPass
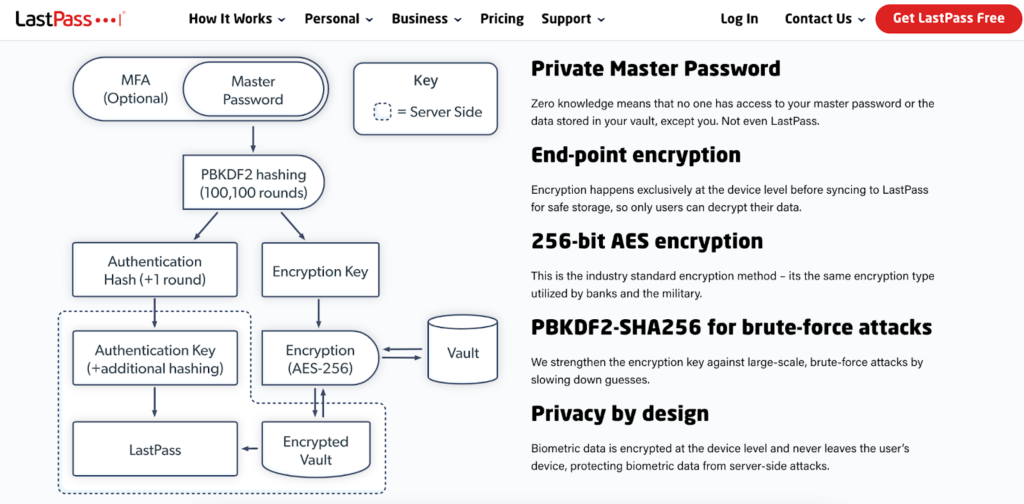
Despite cybersecurity researchers leveling harsh criticism of LastPass, its zero-knowledge architecture seems quite robust. And adding MFA would make it ironclad. A strong, private master password encrypted at the device level, in conjunction with MFA, is practically impervious by modern cybersecurity standards. LastPass doesn’t mandate MFA or strong passwords to its users, leaving them open to user error.
Though it’s worth mentioning that GoTo and LastPass weren’t compromised in the breach — it was their third-party cloud provider. LastPass was one of the first to implement zero-knowledge password managers. Using these, passwords are stored on local devices and encrypted before being sent to LastPass for login. The passwords are dynamically hashed locally and compared to hashes associated with the login process and are never stored.
Fortunately, while the perpetrators stole encrypted vaults, GoTo and LastPass don’t store personal information like bank details, home addresses, social security numbers, or dates of birth. Given the onslaught of cybercrime penetrations, it’s becoming clear that data stored by companies in centralized servers is at risk, even if encrypted.
The Future of Credentials Management
The future of credentials management seems to hang in the balance. Passwords stored in centralized databases are becoming a risk. Even if encrypted, they can be decrypted by cybercriminals with password-cracking rigs. And these rigs will only improve as computer power and innovation increase. Companies need to store passwords locally and should never transmit them to a web service except in a hashed format.
In this regard, passkeys are set to replace passwords, though it might take years before we see wide-scale implementation. Combined with MFA of some kind, the pickings for cybercriminals will become very, very slim when passkeys replace passwords. MFA is mandatory because even if an individual is socially engineered to divulge a complex password, or if it’s forced out of them, it’ll still prevent entry.




The password cracking time illustration is 5 years old, i guess it will be a lot shorter now.