
Source: Unsplash
Security researchers at HUMAN’s Satori Threat Intelligence and Research Team have removed the lid from and taken down a malvertising operation, dubbed VASTFLUX, that affected 11 million devices and spoofed 1,700 applications and 120 publishers. The team initially detected suspiciously high traffic on a particular iOS application, and as they dug deeper, the ad-fraud operation came into full view.
According to the investigation, VASTFLUX ad-fraud operation accounted for, at one stage, a staggering 12 billion bid requests per day. The threat operators—identified as “particularly sophisticated” in the digital advertising ecosystem—inserted malicious javascript code into digital ads, stacked invisible ads over legitimate ones, and raked in the revenue.
HUMAN is a private cybersecurity organization that specializes in bot detection. It referred to the campaign as “VASTFLUX” in its report. The name is a derivation of “fast flux” (a cybercrime evasion technique) and “VAST” (a digital ad template abused in the operation).
VASTFLUX Ad Fraud: Steps One and Two
Source: HUMAN
VASTFLUX was a four-staged operation:
- Javascript Injections
- Manipulation of C2 Instructions
- Repeating Ad Playlists
- Evasion of Detection
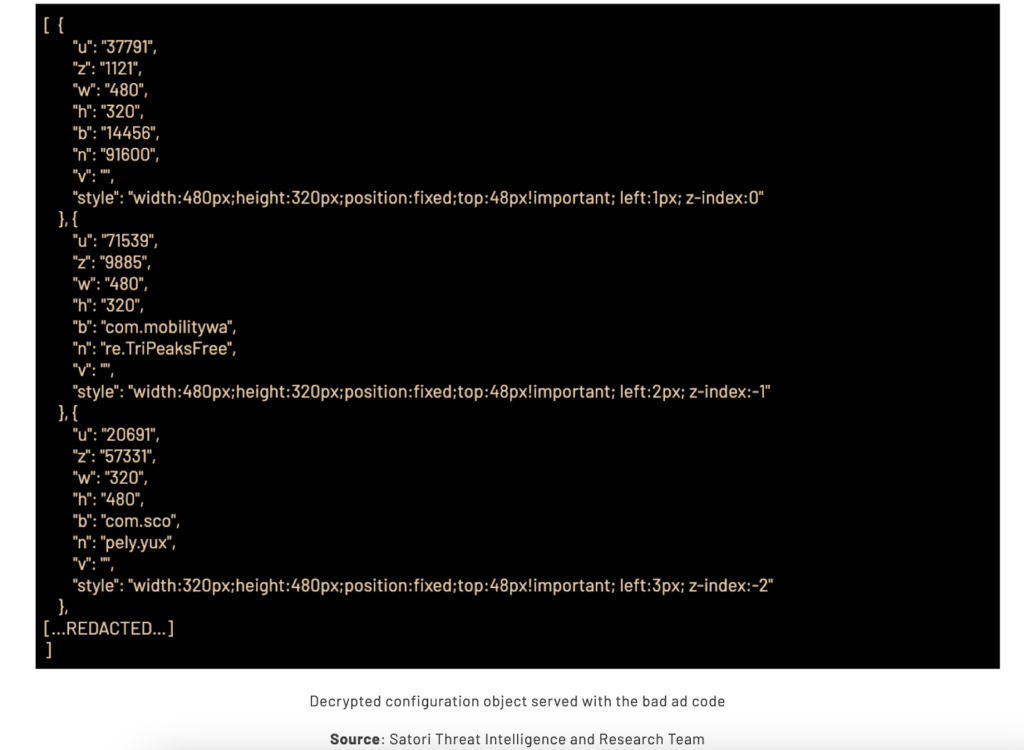
In the first step of VASTFLUX, a targeted app reaches out to its primary supply-side partner (SSP) network for a banner ad to be displayed within the app. Following this request, several demand-side partners start bidding for the ad slot, including those from VASTFLUX fraudsters. Upon winning the ad slot, VASTFLUX’s ad server would place a static banner image in it and inject it with several scripts.
In step two of the operation, the injected scripts decrypt the ad configurations, including a static banner image for the ad slot, a single video ad player hidden behind the banner image, and a series of additional parameters for stacking more video players. After this, the script requested further information from the command-and-control (C2) server on what to place behind that static banner.
These two steps constituted the most ingenious yet subtle parts of the operation. It was a spoofing operation crafted to consider ad size, the publisher, and the application. The fact that VASTFLUX took apart the ad configuration in a way that let it stack 25 ads on top of one another, and got paid for all of them without the ads displaying to users, was a testament to its advanced encryption mechanism.
VASTFLUX Ad Fraud: Steps Three and Four
Source: HUMAN
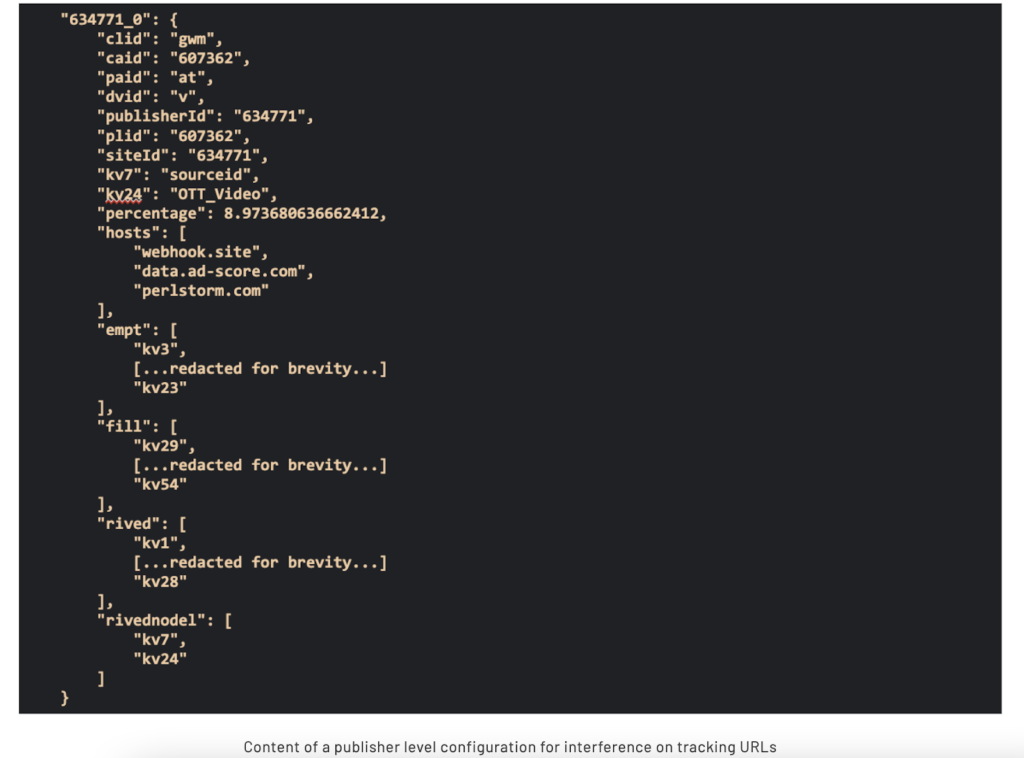
Step three of the VASTFLUX operation used bots to keep reloading ads until the ad slot was closed. Each VAST player ran through its own fraudulent ads playlist, hidden under a legitimate banner ad.
The final step was detection or ad verification tag evasion, which clearly demonstrated the fraudsters’ prowess at exploiting the digital advertising ecosystem. To do this, they relied on the configuration instructions received from the C2 servers. These frequently included publisher-related pointers, adjusting VAST players’ tracking URLs to suit the operation.
This campaign indicates how cybercriminals are now using ad slots to make money from illicit ads and getting away with it. However, this isn’t the first time that cybercriminals have successfully used fraud ads to such an effect. Three months before VASTFLUX’s takedown, researchers at HUMAN uncovered Scylla, a fraud operation targeting advertising SDKs in 80 Android and nine iOS applications, which were available on the official app stores.
Containment Measures from HUMAN
Source: HUMAN
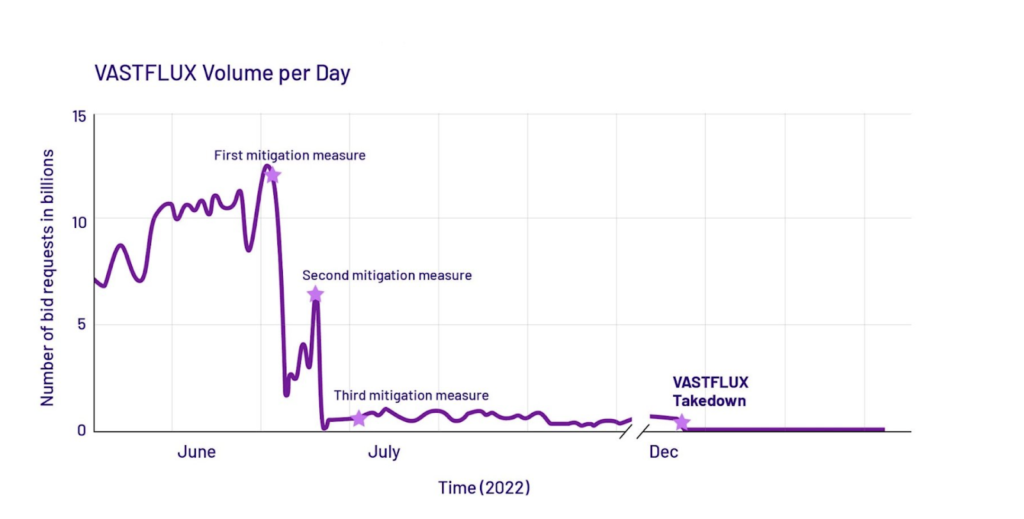
HUMAN was aware of the campaign for some time and investigated the way it operated before taking it down. With support from the affected organizations, HUMAN, from June to July 2022, initiated defensive measures against VASTFLUX. These measures greatly reduced its traffic to nearly 95% by July 2022. By Dec. 6, VASTFLUX’s ad fraud campaign was completely gutted, with zero bid requests coming from it.
Though experts at HUMAN have successfully thwarted the threat, it’s only a matter of time before cybercriminals come up with a new fraud ad campaign to target other applications at another time. To avoid facing such a situation again, HUMAN’s cyber experts have laid down some protective mechanisms.
First, ad platforms must prioritize ad tag verification and other detection procedures with help from fraud detection partners. Second, software supply chain transparency standards, like checking seller identities (sellers.json) and authorization (SupplyChainObject), must be enforced. Lastly, app developers must ensure including software development kits (SDKs) in the applications they develop. These have in-built ad verification.
On the other hand, businesses must be aware of the tell-tale signs of when cybercriminals may be targeting users. These include significantly drained batteries, serious lag in application performance, and higher data consumption. Fraud ad campaigns make money off of legitimate ads. So businesses must protect their advertising campaigns. No platform is off-limits. For instance, Google Ads was recently targeted in a massive ad fraud operation.
Besides the advice from HUMAN, it’s always better to prepare yourself. In this regard, make sure you have automatic patch management in place. This stands for software firms and regular business owners who must protect their networks. Automated patching prevents attackers from using known exploits, which they tend to rely on in indirect spoofing operations.
VASTFLUX Ad Fraud — a Sophisticated Fraud
These ads took advantage of the cover applications provide—it’s harder to detect them on applications than on web pages. That’s because applications have fewer authentication procedures. In this case, the fraudsters targeted iOS applications because of their closed environment. This also debunks the long-held belief that closed environments are generally more sheltered from cybercrime attacks.
It’s important to remember that mobile malware doesn’t just contain itself to mobile devices but spreads to fixed networks. Recently, the Mantis Mobile Malware has been observed by Kaspersky to infiltrate Wi-Fi routers through DNS hijacking.
VASTFLUX was an adaptation of another ad fraud campaign first reported in 2020. This is typical within the cybercrime industry, where an effective penetration technique resurfaces, with some modifications, in other attacks. This allows criminals to build on the previous successful campaigns instead of returning to the drawing board for an entirely new strategy.



