When it comes to apps for mobile devices, InfoSec experts will always recommend downloading from official vendors like the Google Play Store or the Apple App Store. While these sites are much more stringent in their standards for malicious app prevention, there are always exceptions (which require the consumer to use common sense). What is unusual, however, is for a massive amount of malicious applications to not only bypass the Play Store’s Bouncer automated antivirus system, but to all result from one singular company.
Such is the case, however, with the malware dubbed “Judy.” Discovered and reported on by security researchers at Check Point, Judy is an auto-clicking adware exclusively found on 41 apps created by the Korean company Kiniwini (ENSTUDIO in the Play Store). The way Judy works is by, in the words of the researchers, utilizing “infected devices to generate large amounts of fraudulent clicks on advertisements, generating revenues for the perpetrators behind it.” This revenue was likely massive as Check Point estimated a minimum of 36.5 million total downloads of Judy-infected apps.
The actual process of attack was as follows.
- User downloads app.
- Judy registers receivers and creates a connection with a C&C (command and control) server.
- The server responds with the malicious payload.
The JavaScript portion of the payload is seen below:
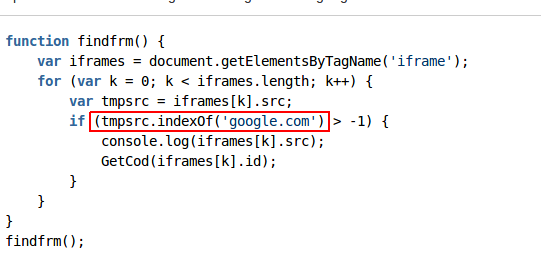
The company in question was rather dedicated to their scam, as many of the applications (as seen below) received high ratings and had a professional presentation.

Upon receiving the reports from Check Point, Google immediately began purging any trace of the applications from the Play Store. One may ask how these apps even found their way onto the Play Store in the first place? As I stated earlier, the vetting process of official app marketplaces is not foolproof. The blocking process may be able to recognize malicious code in the application’s core processes, but as with Judy, the app does not become malicious until the user establishes connection via allowed permissions.
Let this be a lesson. While you are certainly better off downloading apps from the Play Store and App Store, you should be aware of how much access an app is requesting. If it seems too intrusive, don’t download the application (you can probably live without it). Similarly once you’ve downloaded the app and it seems inundated with suspicious ads, delete that sucker as quickly as possible and perform a malware scan.
Photo credit: Flickr / Jan Persiel



