In a previous article, we covered the /etc/passwd and /etc/shadow files used in user and group management in Linux. (And knowing the information that was in that article and this article will also help you when you take the Linux Foundation Certified System Administrator (LFCS) certification exam.) In this article, we will be going over some tasks that a Linux administrator may need to perform daily related to user management. Before starting to check the commands that we need to add to our toolbox, we need to learn to use the –help or -h switches to explore the options available. Using any of those switches, the administrator can see examples and a brief description of the command that we are looking to get more information. The first command that we will check out is useradd -h or useradd –help. We can use the same logic can be applied to any of the commands that we will explore later on in this article.
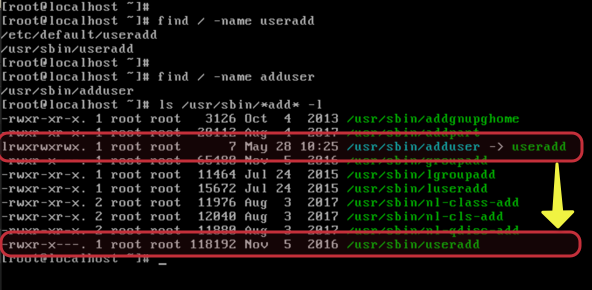
Not sure if you have tested this, but in Red Hat OS-based systems you can try useradd or adduser and both work. (The real command is useradd.) However, there is a link on the file system for the adduser. In case you want to check out on your Linux, just run find / -name <file> and that will trigger a recursive search for that file. Both files are on the same location (/usr/sbin), We have listed them using ls /usr/sbin/*add* -l. One of them has an l in the first, which means a symbolic link (it is created using ln command).
The useradd command creates users and automatically creates an entry in the /etc/passwd file. However, it does not manage the password for the users, which is managed separately with another command that we are going to explore in a little bit.
To create a new user, we can run the commands listed below. The result of each command will be a new entry in the /etc/passwd file.
useradd anderson useradd walter
When a user is created a UID (user ID), and GID (group id) is automatically created, and they are associated with the new user. This new group that is labeled with the new user name and it contains only the new user is called primary or private group. We can check the UID and GID in the /etc/passwd file (as depicted in the image below).

Using the id command, we can retrieve that information from any given user. The result will be the UID, GID and any group that the user belongs to, and we can use the following syntax in conjunction with the image below to see in action the id command.
id <username>

To reset the password of any given user logged on as root, the following command can be used to reset/initiate the password for both users created in the previous step. The password itself will be stored in the /etc/shadow file.
passwd Anderson passwd walter
Important: A security best practice in Linux (well, in any operating system) is to avoid running commands as root/administrator. In Linux, we can take advantage of sudo to delegate some privileged tasks to be executed by a regular user. In this tutorial, we are going to focus on the command required to manage users as root, however, in a production/more professional environment, make sure to use a regular account with proper sudo permissions.
Some daily activities with user management
In this section, we will cover several tasks that an administrator will perform several times when managing users in a Linux system.
A common task for any administrator is to lock and unlock accounts. We can use the first command lock any given account (the result will be an exclamation mark (!) in the /etc/shadow file). Using the second command, we can unlock the account.
usermod -L <username> usermod -U <username>
Another task is to change the primary group of a user. A primary group is a key concept because all files created by such user will have its primary group associated with the initial permissions. The following sequence of commands helps to understand the process.
id anderson usermod anderson -g srv-admin id anderson

In some circumstances, we need to define an expiry date for a user, and that can be accomplished with usermod command as well. We are using chage command, which also can be used to configure all features displayed by the chage -l <username> command.
Note: The chage command requires the use of /etc/shadow file. If you are using just /etc/passwd, then it wouldn’t work.
chage -l aurelio usermod aurelio -e YYYY-MM-DD chage -l aurelio

Switching between /etc/password and /etc/shadow
It is straightforward to switch back and forth between password and shadow files. If you are using a Red Hat-based OS, and you are using shadow, to go back to /etc/password, just run this following command. The result will be the removal of /etc/shadow file, and all passwords that were once in this file will be transitioned to /etc/passwd.
pwunconv
If you want to revert what we have just done or configured shadow in a system that has only /etc/passwd, then, you should be using this command.
pwconv
Managing templates and default values
By default, any new user will receive the configuration defined in the definition file. Some of the default configurations are related to where the home directory of that given user will be created, shell to be used, and so forth.
We can manage that initial configuration for any new users by editing the file /etc/default/useradd.
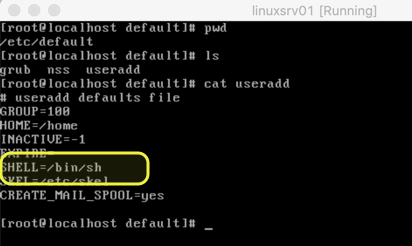
After changing the file, we can create new users (in our case users Anderson and Aurelio)

Another important file is the /etc/login.defs, which is available when using /etc/shadow file. In that file, we can configure the limits that will be applied to all new accounts on the system.
Checking your shadow and password files
We can take advantage of pwck command to validate the integrity of the users and authentication for either /etc/passwd and /etc/shadow files. I recommend using the -r switch, which is read-only and only displays errors and warnings found on the specified files.
pwck -r /etc/passwd pwck -r /etc/shadow

Featured image: Shutterstock / Wikipedia



