In 2007, Microsoft Windows Vista introduced a new security feature called User Account Control (UAC). Upon its release, people had many things to say. This important Windows security component creates an abstraction layer. That protects your PC from malware. It also reduces unauthorized changes to the operating system. In all, it adds an extra security layer to your device.
That said, many users choose to disable UAC for varied reasons. This exposes their device to security risks. UAC notifications may also be intrusive. That’s why, many people consider UAC as a nuisance, not a security feature. To clear the air on UAC, we’ll take a detailed dive into what UAC virtualization is. Then, we’ll see how it protects your devices, and finally, its potential downsides.
As always, let’s start with the fundamentals. I’ll start with explaining the terms “UAC” and “virtualization”. After that, I’ll move on to UAC virtualization.
What Is User Account Control (UAC)?
UAC is short for “User Account Control”. It prevents unauthorized access or changes to the Windows operating system’s core components. In Windows Vista and higher versions, UAC is automatically an administrator privilege. That means only the accounts with the highest privileges can allow changes to Windows’ core components.
As a user, you’ll encounter UAC in these 3 scenarios:
1. Installing New Programs
Have you seen Windows pop-up notifications while installing software? Typically, these notifications warn you that a new program is trying to make changes to your Windows system. You have to explicitly approve this installation for the new software to install and work on your device.
2. Accessing Restricted Directories
You’ll also see UAC when you’re accessing restricted directories like %ProgramFiles%, %Windir%, %Windir%\system32, etc. Here, you have to enter your admin password or PIN to access.
3. Changing Registry Variables
Changing the value of any registry variable impacts your Windows environment. That’s why Windows sends a notification and requests explicit permission from you before continuing.
In all these UAC scenarios, you’ll get notifications requesting explicit confirmation. While that seems intrusive, the point is to protect your device and the Windows components.
If you’re the administrator, you have to explicitly approve the action. To do that, you’ll often have to click the “Yes” button. Other users have to enter the administrator’s four-digit PIN or password to continue.
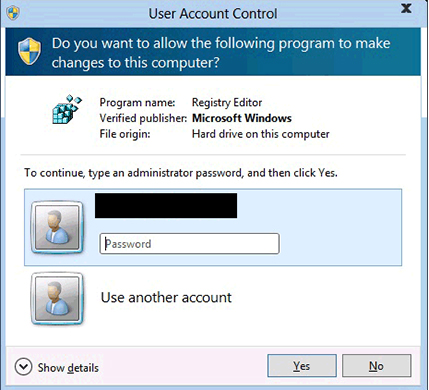
What Is Virtualization
Virtualization is the process of creating an abstraction layer to protect critical resources. That also helps the platform use the existing resources more efficiently. We commonly see virtualization when a computer’s hardware elements are divided into many virtual units. These units are Virtual Machines (VMs). Each VM has a portion of the computer’s hardware elements. It also runs independently of other VMs. Besides efficient resource utilization, virtualization also reduces downtime, improves provisioning, and eases management.
Now you know what UAC and virtualization are, let’s put them together.
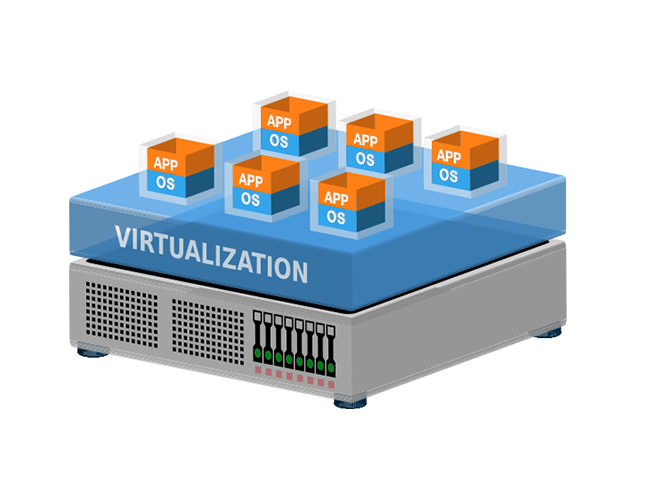
What Is UAC Virtualization?
UAC was all the hype when Microsoft released the Windows Vista operating system. It was a new security component for that OS. That means computers with older operating systems don’t have built-in UAC. The apps developed for older systems also don’t have this feature. So, what happens if you have an older device? What about the apps written before Vista’s release? How will UAC work?
The answer is UAC virtualization. Here, a VM runs on top of the original Windows operating system. That provides all the required resources for software to run on Windows. This virtualization also ensures that the software doesn’t rewrite or change the Windows operating system’s core components. This means, the changes a software makes reflect only on the VM. They don’t reflect on the physical operating system itself. For example, an application may think it’s writing to C:\Program Files\. Yet, the app is only writing to %LOCALAPPDATA%\Files\. So, this change applies only to this user account. It isn’t a global change. If you’re wondering why it has this mapping between folders, it’s to allow older software or operating systems to work.
The role of UAC virtualization is very specific, so it’s only applicable in these 3 cases:
- New software is installed or used from a user account only. Also, this account must have write access to the Program File directory.
- The UAC virtualization is enabled on the host device.
- The device runs on a 32-bit operating system as 64-bit computers don’t need UAC virtualization.
In all these situations, a host device needs to have UAC enabled. How can you achieve that, then?
Turning on UAC Virtualization in Windows 10
Follow these 4 steps to see if UAC virtualization is on in Windows 10:
- Go to Run (Windows + R) and type secpol.msc
- Click OK. That opens the Local Security Policy window
- Expand Local Policies on the left-hand pane and click Security Options
- Navigate to User Account Control: Virtualize file and registry write failures to per-user locations on the center pane
If this option is enabled, UAC virtualization is set up on your device. If it isn’t, you can follow these 3 steps to enable UAC virtualization:
- Double-click User Account Control: Virtualize file and registry write failures to per-user locations. That opens a pop-up window
- Select the Enabled radio button
- Click OK to close the popup window. That enables UAC virtualization on your device
After setting up UAC virtualization, you can also manage its behavior and customize it to meet your preferences. Read on to find out how you can do that!
Managing User Account Control
To change your UAC settings and preferences, go to Windows Start menu > Settings. In the search box, type User Account Control and choose the option that comes up.
The UAC control settings open and you’ll see a slider on the left. Move up and down the slider to pick one of the 4 setting options.
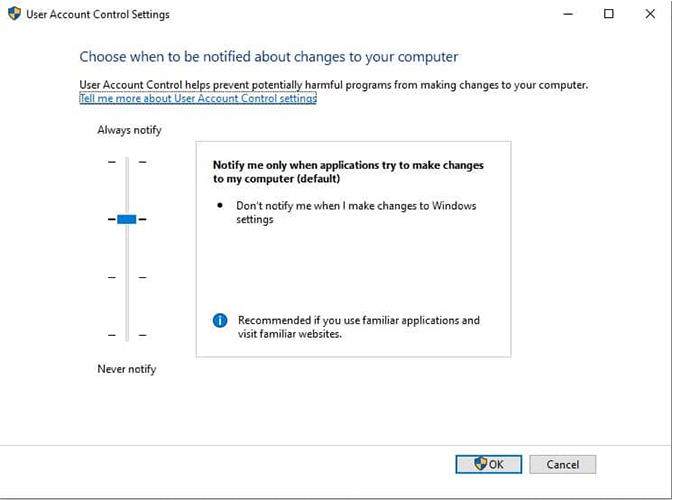
Let’s take a more detailed look at the 4 options:
1. Always Notify
This is the strictest setting. You have to provide explicit permission when you or software tries to install, update, or change Windows settings. All the other tasks on the system will freeze until you respond through the notification pop-up. This setting is ideal for devices that frequently install software for testing.
2. Notify Me Only When Programs Try to Make Changes to My Computer
This is the second strictest option. It’s also the default UAC setting. Here, the computer will notify when a program tries to install or change Windows settings. Like the earlier option, it freezes all tasks until you respond. Yet, this option won’t generate notifications when you manually change any setting.
3. Notify Me Only When Programs Try to Make Changes to My Computer (Do Not Dim my Desktop)
As the name suggests, this option is non-intrusive and doesn’t freeze other tasks. It’ll also notify you when you manually make changes to the Windows system. Needless to say, this is a lower security option when compared to the previous two. Ideally, choose this option only when you’re the only user and the notifications process is slow enough to disrupt your productivity.
4. Never Notify
This option disables UAC virtualization, which can create a serious security risk for your device. We recommend never using this option, even if it seems convenient. All these options relate to software installing and changing the Windows system, especially the restricted directories. That said, what happens when you or a program tries to change the registry variables? How is the abstraction created?
Registry Virtualization
Registry virtualization is when you apply UAC virtualization to the system registry. This virtualization creates an abstraction layer. That way, it can block access to global registry variables without impacting the software that uses them. Like UAC virtualization, it also redirects write actions to the user account’s registry keys. That way, the global keys remain unchanged. Thus, this is what a UAC/registry virtualization is all about. But like every software, it has its downsides too.
Downside of Virtualization
- Works only on 32-bit apps. That’s because all AMD64 compatible programs came after the UAC was implemented
- Ineffective if you don’t have write permission to the file path or registry variable. This scenario can throw errors, and the software may even crash at times
- Works only on non-admin user accounts
- Disabled by default. You have to turn it on yourself
Overall, UAC virtualization is a handy security feature, especially if you’re using an older computer. Still, its usage is likely to come down in the next few years. That’s because most apps today are designed for 64-bit systems.
Final Thoughts
UAC virtualization is necessary to enable software applications to work on pre-Windows Vista operating systems. Essentially, UAC virtualization creates an abstraction layer to prevent unauthorized software and users from making changes to the core Windows components. This layer writes to the user accounts instead of the core components and global registry variables. That reduces the impact of malware. It also prevents the effects of other unauthorized changes.
That said, UAC virtualization’s efficiency and need will diminish in the coming years as the number of older systems come down. It also has many downsides that’ll make it non-existent by the end of this decade. To name a few, it needs write permissions and non-admin accounts. It’ll also become obsolete because it can only work on 32-bit apps.
FAQ
Should I enable UAC virtualization?
Yes, you should. UAC virtualization protects your computer from malware and other malicious programs. That’s critical because these programs tamper with your operating system’s core security components. When you enable UAC virtualization, it creates an abstraction layer. That prevents any software from making changes to the core components. It also allows programs to execute.
What are the side effects of disabling my UAC virtualization?
Disabling UAC virtualization has many side effects. When you disable your UAC virtualization, you’re making your PC more vulnerable to malicious programs like malware. That’s why disabling UAC virtualization is a serious security threat. We also strongly discourage you from disabling UAC virtualization.
Does UAC virtualization impact my system’s performance?
No, UAC virtualization doesn’t impact your system’s performance. That’s because it doesn’t consume additional resources. That said, the notifications can freeze all your tasks until you respond to them. Please note that this intrusion is necessary for your computer’s safety.
Is UAC virtualization still relevant?
At this point, yes. That’s because many systems still run on operating systems introduced before Windows Vista. As time goes by, these systems’ use becomes less and less. That means UAC virtualization’s benefits also go down. That means UAC will become irrelevant when pre-Vista operating systems disappear.
Does UAC virtualization have any benefits?
Yes, many benefits come with UAC virtualization. They help to prevent unauthorized programs from harming your PC, restrict access to sensitive directories, and disallow changing the value of registry variables. In all, it’s another security layer for your PC.
Resources
TechGenix.com: Making Windows Passwords Highly Secure
Learn how to secure your Windows passwords here.
TechGenix.com: Exposing Windows 7 UAC
Know more about how UAC works in Windows Vista and Windows 7 here.
TechGenix.com: Privilege Access Management for an Increasingly Dangerous World
Discover how you can manage privileged access in a dangerous world in this article.
TechGenix.com: Improving Security Through Least Privileged Practices
Understand the ways and means to improve security through least privileged practices in this article.
TechGenix.com: Network Access Control
Read about Network Access Control here.
TechGenix.com: Emerging Authentication Practices
Discover how authentication is changing here.




The author of the article mixes two independent concepts, making the article disinforming.