Product: AGAT Software Solutions’ ActiveSync Shield
Product Homepage: Click here
Free Trial: Click here
Introduction
The proliferation of consumer devices accessing corporate network resources represents a significant security risk, because most consumer devices lack the necessary security controls (device encryption, remote wipe, etc.) that enterprise security administrators require to provide adequate data protection. The easy way to mitigate this risk would simply be to ban these devices altogether, but increasingly that is becoming difficult. Allowing users to access corporate resources using their own device can reduce costs and increase productivity, something most businesses will be hard pressed to pass on. Faced with the challenge of providing access while at the same time maintaining the highest level of security, security administrators are looking for solutions that enable secure remote access for consumer devices, yet provide a simple and effective way to protect the data and information that is accessed with these devices.
Exchange and ActiveSync
One particularly troublesome issue for security administrators is providing secure remote access for mobile devices to their Exchange environment. ActiveSync does have some built-in security functions, but the implementation of these features is not ubiquitous among the mobile device makers. In addition, ActiveSync lacks the granular controls that are required to provide the highest level of protection required by many organizations. For example, once a user has connected their device successfully with ActiveSync, they can upload and download attachments as they wish. This may not be an issue if the user connects with a corporate-issued device that supports remote wipe, but if the user connects with another device that doesn’t, sensitive data can be stored on that device and can potentially fall in to the wrong hands.
AGAT ActiveSync Protector Suite
ActiveSync Protector Suite by AGAT Software Solutions is designed to provide fine-grained access control to mobile devices using ActiveSync. ActiveSync Protector consists of three components – ActiveSync Protector Filter, Access Portal, and Mobile Access Control filter – and integrates with Microsoft ISA/TMG as well as IAG/UAG. With ActiveSync Shield installed security administrators can enforce data protection by:
- Filtering content – Configured by user, user agent, or device type
- Controlling synchronization – Allow or deny synchronizing messages, contacts, tasks, and calendar events
- Controlling attachments – Allow or deny synchronizing attachments included in messages or calendar events
- Filtering on keywords – Prevent synchronizing messages or calendar events that contain specific keywords
- Restricting communication – Block sending of all attachments from the device, and allow meeting requests to be published when mail is blocked
In addition, the ActiveSync Shield provides granular access control by using:
- Device verification – Verify that the user ID and device ID match
- White lists – Manage a list of allowed users
- Device types – Allow or deny specific mobile devices
- User identification – Control access based on the user’s Active Directory ID or group membership information
Best of all, the ActiveSync Shield provides all of this protection without requiring any software to be installed on the mobile device.
Installing ActiveSync Protector Filter
ActiveSync protector can be installed on any IAG/UAG server or ISA/TMG firewall. In this article I’ll demonstrate how the product integrates with TMG. Before installing ActiveSync Protector on a TMG firewall, you must first install the Microsoft .NET Framework 4.0. Once the .NET framework is installed successfully, launch the ActiveSync Protector installer and select your integration. You may also select the installation folder, if required. Be advised that the firewall service will be restarted during the installation process. It is recommended that you install this software during a scheduled maintenance window to avoid any unnecessary service interruption for your clients.

Figure 1
Once the installation is complete, click on Start | All Programs | Agat ActiveSync Shield | ActiveSync Protector or simply double-click the shortcut to ActiveSync Protector on the Windows desktop to launch the ActiveSync Protector management console.
Content Rules
Once ActiveSync Protector is installed, any access to Exchange must be explicitly defined. All other communication will be denied. To configure a content rule, select the Content Rules tab and click Add. Here you can give the rule a name and apply the rule to specific device types, user agents, Active Directory groups, or device owners as required.

Figure 2
Select the Action tab to define the synchronization policy for this content rule. Here you can specify all mail, only calendar-related mail, and on-mail related items such as calendar events, contacts, and tasks. You can also explicitly define an attachment policy, allowing the upload or download of any/all attachments or specific attachment file types.

Figure 3
The administrator can also configure blocked content based on domain, keywords, or specific mail headers.
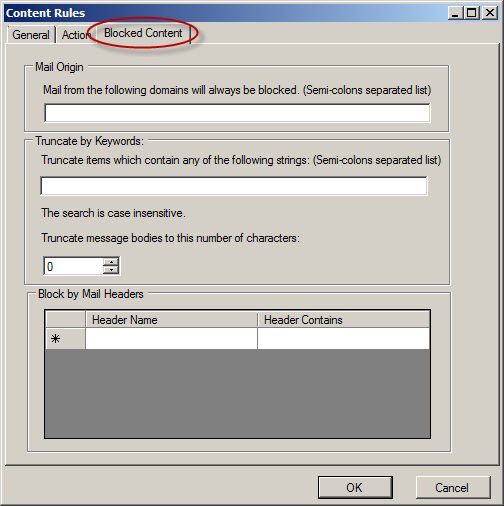
Figure 4
The administrator can configure multiple content rules with varying levels of access. It is important to remember that content rules are processed in order, and once a request matches a rule, no further rule processing takes place. Be sure to plan your content rules carefully to avoid preventing legitimate access or worse, allowing too much access.

Figure 5
Access Control
In addition to providing highly granular control of mail, calendar, and attachment synchronization, ActiveSync Protector enables the administrator to restrict devices that individual users can synchronize with. This ensures that users may only synchronize with administrator approved devices. This is enforced by selecting the Access Control tab and selecting the option Each user can synchronize their data with only specific devices.

Figure 6
By default, users are defined via text file. Select the Basic registration option and click Users File Settings. Here you can define where the users file is located in addition to the rejected users/device file. The administrator also has the option to enable training mode, which does not reject requests for synchronization, but rather records the device ID and the user name in the specified text file. This is useful for gathering device ID information and correlating that information to individual users. The device ID is contained in the ActiveSync communication and is not easily discoverable, so this greatly simplifies the process of collecting device IDs.

Figure 7
Using a text file is obviously a very simplistic way in which to authenticate and authorize users. Thankfully the ActiveSync Shield includes additional features that provide more accurate and granular control over users and devices. The Access Portal and Mobile Access Control filter provide a much more elegant solution and will be discussed later in this article.
Servers
In order to support Active Directory user and group authentication, the ActiveSync Protector software must be configured to use an LDAP server. Select the Servers tab and specify the name of an LDAP server along with credentials with a minimum or read access to the directory. Optionally you can specify the use of a Global Catalog (GC) server. In addition, ActiveSync Protector can be configured to interface with any anti-virus solution that supports ICAP.

Figure 8
Content Types
By selecting the Content Types tab the administrator can configure specific content types for use when applying content rules.

Figure 9
Device Types
Choosing the Device Types tab allows the administrator to define specific mobile devices based data contained within the ActiveSync communication. Devices can be identified by searching for known signatures or strings that are unique to each device platform. The administrator can define exact pattern matches, strings that begin with a specific sequence, or use regular expressions to identify devices.

Figure 10
Web Publishing
After the administrator has configured content rules, defined access control policies, configured LDAP servers required for user/group authentication, and defined any required mobile device types, the last step in the process is to define which web publishing rules to apply the filter to. By selecting the Web Publishing tab there will appear a list of web publishing rules configured on the TMG firewall. Select the applicable rules, and then choose Save to save the configuration.

Figure 11
ActiveSync Access Portal
The Access Portal is an administrative web site designed to ease the burden on administrators and to provide a more robust administration experience. Mobile Access Control provides advanced user provisioning features such as automatic self-enrollment, self-enrollment registration, smart card enrollment, and administrator initiated manual enrollment. Installing the Access Portal module requires an IIS sever and SQL database, and it is recommended that you install these components on a separate server. Once installed and configured, an ActiveSync users will log in to the Access Portal page, enter their login credentials. Once complete, the user initiates synchronization on their mobile device to lock the device to the user account.

Figure 12
ActiveSync Mobile Access Control
Accessing the corporate network from a smartphone on an untrusted network presents significant security risk. With corporate credentials stored and used on the mobile device, this information can potentially be compromised and used to access other applications and data. The Mobile Access Control filter is a solution that avoids the use and storage of AD credentials on the device itself. In addition, the same implementation can offer a solution for organizations that use smart card login rather than AD credentials and for organizations seeking to avoid AD password lockout resulting from login failure attempts from improperly configured mobile devices or by an attacker attempting a brute force attack.
In this scenario, once the user logs onto the Access Portal, they create a new username and password. From the time they click the “Create” button, they must perform an ActiveSync operation within the defined time frame. During the first operation the device ID is registered and linked to the user.
During routine authentication, the user enters the credentials created on site. The Mobile Access Control filter then verifies the credentials and confirms that the device ID matches the user.
Summary
The AGAT Software Solutions ActiveSync Shield addresses a critical need for security administrators tasked with providing the highest level of data protection for devices that use the ActiveSync protocol to synchronize with on-premises Exchange servers. As the proliferation of consumer devices continues, and more organizations move to adopt Bring Your Own Device (BYOD) strategies, providing granular control to both managed and non-managed mobile devices will become vitally important. For IAG/UAG and ISA/TMG administrators, ActiveSync Shield provides the essential controls required to enforce data protection across a wide range of mobile devices. In addition, the ActiveSync Shield gives administrators more granular control over authentication and authorization, along with the advanced option of creating custom login as opposed to using ActiveDirectory credentials. The solution also provides administrators with a tool they can leverage to restrict ActiveSync access to a single authorized mobile device, and a robust self-registration experience that simplifies the process of provisioning new clients.
In addition, ActiveSync Shield offers an interesting product road map for their next release which includes two important features:
- ActiveSync Strong authentication – This module will further enhance two factor authentication by adding another factor from the device in addition to the device ID. The module will place a unique file on the phone during the registration process in order to enhance 2FA and will block requests from compromised credentials and prevent them from receiving corporate data via ActiveSync.
- ActiveSync Web mail – This module approaches the problem of protecting mail information on a stolen or stolen device in a very unique way. Performing remote wipe requires the device to perform a sync operation, which is potentially problematic. The best approach from a security perspective is to avoid storing data on the device in the first place. The ActiveSync Web mail does this by changing the mail body to an online web page and leaving the mail header as expected by the device mail client. The results in mail sender and subject being the only data stored on the device. Displaying the message body is done after opening the message and viewing an online web page published by the ActiveSync Web mail. If a device is lost or stolen, the user is blocked on the server side and data cannot be retrieved.
Overall I’d recommend evaluating the software if you are using IAG/UAG or ISA/TMG to provide secure remote access to mobile devices using ActiveSync. I give the product 3.5 out of 5 points for the Silver Award.
ISAserver.org Rating: 3.5/5
Get more information about AGAT Software Solutions’ ActiveSync Shield



