The Windows operating system contains numerous built-in, command line networking utilities. These tools range from the obscure to the commonplace. However, there are 11 built-in networking tools that Windows networking administrators should be familiar with.
Ping
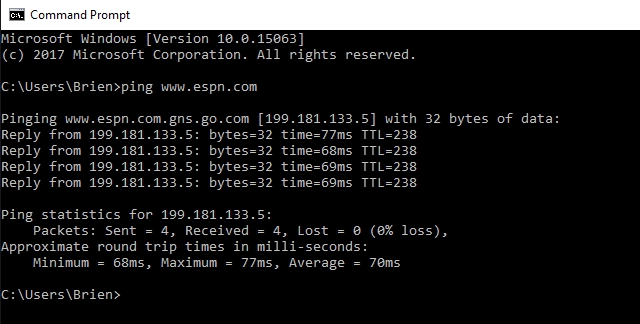
I am guessing that the ping command is probably the most familiar, and most widely used of the utilities being discussed in this article, but that does not make it any less essential.
Ping is used to test the ability of one network host to communicate with another. Simply enter the Ping command, followed by the name or the IP address of the destination host. Assuming that there are no network problems or firewalls preventing the ping from completing, the remote host will respond to the ping with four packets. Receiving these packets confirms that a valid and functional network path exists between the two hosts.
NetStat
If you are experiencing problems with network communications, then network statistics can sometimes help point you toward the root cause of the problem. That’s where the aptly named NetStat command comes into play. This command has a number of different functions, but the most useful of these is to display network summary information for the device. To see this type of summary information, just type NetStat -e.
ARP
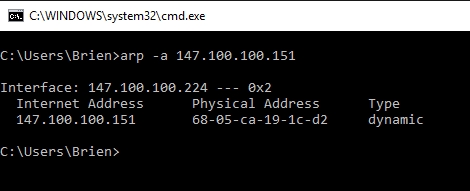
The ARP command corresponds to the Address Resolution Protocol. Although it is easy to think of network communications in terms of IP addressing, packet delivery is ultimately dependent on the Media Access Control (MAC) address of the device’s network adapter. This is where the Address Resolution Protocol comes into play. Its job is to map IP addresses to MAC addresses.
Windows devices maintain an ARP cache, which contains the results of recent ARP queries. You can see the contents of this cache by using the ARP -A command. If you are having problems communicating with one specific host, you can append the remote host’s IP address to the ARP -A command.
NbtStat
As I am sure you probably know, computers that are running a Windows operating system are assigned a computer name. Oftentimes, there is a domain name or a workgroup name that is also assigned to the computer. The computer name is sometimes referred to as the NetBIOS name.
Windows uses several different methods to map NetBIOS names to IP addresses, such as broadcast, LMHost lookup, or even using the nearly extinct method of querying a WINS server.
Of course, NetBIOS over TCP/IP can occasionally break down. The NbtStat command can help you to diagnose and correct such problems. The NbtStat -n command for example, shows the NetBIOS names that are in use by a device. The NbtStat -r command shows how many NetBIOS names the device has been able to resolve recently.
Hostname
The previously discussed NbtStat command can provide you with the host name that has been assigned to a Windows device, if you know which switch to use with the command. However, if you’re just looking for a fast and easy way of verifying a computer’s name, then try using the Hostname command. Typing Hostname at the command prompt returns the local computer name.
Tracert
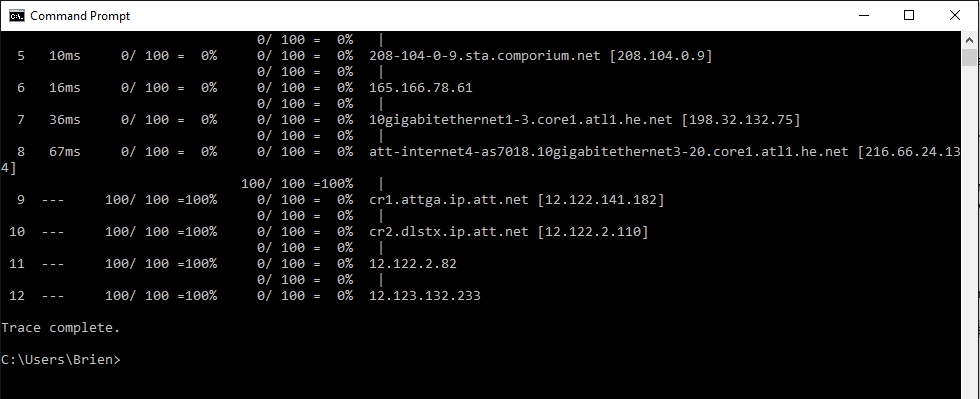
Contrary to what a rather infamous YouTube video might lead you to believe, Tracert isn’t pronounced “Tracer T,” nor can it show you how many people are using Google right this second. Instead, Tracert, or “Trace Route,” is a utility for examining the path to a remote host.
Functionally, Tracert works similarly to Ping. The major difference is that Tracert sends a series of ICMP echo requests, and the request’s TTL increased by 1 each time. This allows the utility to display the routers through which packets are passing to be identified. When possible, Windows displays the duration and IP address or fully qualified domain name of each hop.
IpConfig
One utility that I find myself using constantly is IPConfig. At its simplest, the IPConfig command will display basic IP address configuration information for the device. Simply type IPConfig at the Windows command prompt, and you will be presented with the IP address, subnet mask, and default gateway that the device is currently using.

If you would like to see more detailed information, then type IPConfig /all. Doing so causes Windows to display IP address configuration that is much more verbose. This is also the command that you will have to use if you want to see which DNS server the Windows device is configured to use.
The IPConfig command can do much more than just display IP address configuration information. It also contains options that can help you to troubleshoot problems related to DNS and DHCP. For example, entering the IPConfig /FlushDNS command purges the contents of the computer’s DNS resolver cache.
NSLookup
NSLookup is a great utility for diagnosing DNS name resolution problems. Just type the NSLookup command, and Windows will display the name and IP address of the device’s default DNS server. From there, you can type host names in an effort to see if the DNS server is able to resolve the specified host name.
Route
IP networks use routing tables to direct packets from one subnet to another. The Windows Route utility allows you to view the device’s routing tables. To do so, simply type Route Print.
The cool thing about the Route command is that it not only shows you the routing table, it lets you make changes. Commands such as Route Add, Route Delete, and Route Change allow you to make routing table modifications on an as needed basis. The changes that you make can be persistent or nonpersistent, depending on whether you use the -P switch.
PathPing
Earlier, I talked about the Ping utility and the Tracert utility, and the similarities between them. As you might have guessed, the PathPing tool is a utility that combines the best aspects of Tracert and Ping.
Entering the PathPing command followed by a host name initiates what looks like a somewhat standard Tracert process. Once this process completes however, the tool takes 300 seconds (five minutes) to gather statistics, and then reports latency and packet loss statistics that are more detailed than those provided by Ping or Tracert.
NetDiag
Perhaps the most useful of the network utilities that are built into Windows is NetDiag. The NetDiag command is designed to run a battery of tests on the computer in order to help the technician figure out why the computer is experiencing networking problems.
One of the things that I really like about this tool is that although there are a number of optional switches that you can use, you don’t have to use any of them unless you want to. Entering the NetDiag command by itself will cause all of the available tests to be run.
In some cases, NetDiag can not only identify problems, but can also fix those problems. Obviously, NetDiag cannot automatically correct every problem that it finds, but appending the /Fix parameter to the command will tell NetDiag to attempt to fix the problem automatically.
The Windows operating system is jam packed with command line utilities. Many of these utilities are left over from operating systems that were introduced decades ago. Even so, the utilities that I have discussed in this article are every bit as useful today as they were when they were first introduced.
Photo credit: Shutterstock




NetDiag is listed and this article is dated 9/1/2017? NetDiag hasn’t been included with Windows since XP.
I’m running xp now, and it’s not recognizing NetDiag.
Can you explain ARP and RARP difference?
nothing is there in difference
Search Results
Featured snippet from the web
In Address Resolution Protocol (ARP), Receiver’s MAC address is fetched. Through ARP, (32-bit) IP address mapped into (48-bit) MAC address. Whereas, In Reverse Address Resolution Protocol (RARP), IP address is fetched through server. Through RARP, (48-bit) MAC address of 48 bits mapped into (32-bit) IP address.
ARP requests Layer 2 MAC address when the Layer 3 IP is known.
RARP requests Layer 3 IP address when the Layer 2 MAC is known.
Both are limited to the local LAN and can not resolve addresses on other networks.
The goal of what is now called Intrusion Detection Systems (IDS) was to detect a malicious attacker before an anti-virus, Trojan horse, or worm was used to strike. If the attacker was able to strike the network, security professionals would dissect the code. Once the code was dissected, a response or “fix” was applied to the infected machine(s).
how to check network port status
netstat -e can be helpful but it’s like the “Dummy Lights” on cars. It only gives you a small glimpse into what can be happening. The real work horse of the Netstat commands is netstat -bao. It tells you all your connections and the Port and Program that they belong to.
Netstat has lots of great options. -BAO certainly has its place, but -E is nice for getting a really quick overview.
OK, you didn’t mention telnet, which is used to get some info from another computer which you connected to. It is very good for hackers to use and exploit. You did didn’t also mention netsh, it can be used to find some connected networks, depending on how you use it. Netsh can be used to hack Wi-Fi networks depending on how you use it.
how to access router statistics like mode , download speed,upload speed,name of the router,firmware version, date time,dns server as in the status page of any router. Is there any software free that would give those details
I don’t know of a good free tool that works universally on all routers
What’s a Windows equivalent to “smbutil statshares -a” that can tell me how my Windows client is connecting to the Windows server? (i.e. SMB 1, 2 or 3)
Some of the paragraphs on this are so useless:
I am guessing that the ping command is probably the most familiar, and most widely used of the utilities being discussed in this article, but that does not make it any less essential.
How does that provide any meaningful information? B-grade writing at best.
Finally, explanations can’t decide between advanced and beginner-level. You need to flesh out each on simpler terms if they’re to be understood. Admins who can understand things like these don’t need to even read the article:
‘Tracert sends a series of ICMP echo requests, and the request’s TTL increased by 1 each time’.
Yes, I agree with both points. Some of the descriptions were not uniformly useful.
Still, a good article in many ways.
i still can’t use cmd as i want
run cmd as admin from the start menu by right clicking on cmd and choosing run as admin.
Open an elevated cmd
Winkey + R
Enter cmd
Ctrl + Shift + Enter
Maybe you can help me, Brian. I’m looking for a utility that I can setup in a TASk to check what IP my ISP has assigned my connection and email that info to a friend sho remotes in to diagnose and do maintenance on my system. Since most ISP assign dynamic IP’s, without know what it is currently they can’t remote in via RealVNC or other remote access programs without my being present to supply the correct address to us to connect. Is there anything available or controllable klede to achieve this? We both use Outlook, so the msg generated with my currently assigned IP would need to be send as a mgs and it needs to be able to be setup as a TASK so it’s kept current.
Thanks in Advance!
@Pre, NoIP does that for free. You just need to register and check-in once a month to renew the connection
hi how to test netdiag command
Pre… Set up a static IP through your router web interface page. The IP address from a ISP is actually a static address that allows for x many subnet IP addresses. Its your SOHO router that has a built in DHCP server that assigns the seemingly random dynamic IP addresses. Though you can set up a static IP for a device and then manually config that device with the static IP. It sounds like a lot, but you can do it with ease with a youtube video tutorial. Basically run ipconfig and take a picture of that info and then reassign that info when you set up a static(non changing) IP address.
I was trying to find out the port number as well as the IP address to a old Brother laser printer that has wifi on it for ad-hoc direct printing.
The firmware upgrade program I downloaded asked for both the iPad address and the port number.
I tried for hours trying to search for it.
The router admin GUI, though handling the DHCP (Dynamic Host Configuration Protocol) only revealed the iPad address it assigned, the device name, and the MacID in the connected devices screen (Still no port information).
I tried all the 11 commands here and none of them revealed the port information. I believe the format is 192.168.0.103:xxxx. Where xxxx is the port number.
Any light you can shed on this.
nmap is a free download. Need to be careful with it though…
lots of switches you can throw to get different kinds of output.
C:\WINDOWS\system32>nmap 192.168.1.*
Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-25 22:40 Eastern Daylight Time
Nmap scan report for 192.168.1.1
Host is up (0.0036s latency).
Not shown: 993 closed ports
PORT STATE SERVICE
23/tcp open telnet
80/tcp open http
443/tcp open https
992/tcp open telnets
4567/tcp open tram
8080/tcp open http-proxy
8443/tcp open https-alt
MAC Address: F8:E4:…….
You might try going to download.com and looking for port scanning utilities (be careful on the site, as it has historically contained a lot of deceptive links). I found a really good, free port scan tool out there once, but I can’t remember the name of it.
Thank you Brien. Saverino.
I’m a first year IT student, and I just want to say a big THANKS to you, Brien. You’ve simplified what it’s taken more than 30 pages of a text book to spit out. And your explanations were far more easy to understand. I’m grateful you posted this article!
Thanks Carol, I really appreciate it!
Thanks, some very useful tools, shortcuts that will save me some time. Will be visiting this page more often.
Much appreciated!
In Address Resolution Protocol (ARP), Receiver’s MAC address is fetched. Through ARP, (32-bit) IP address mapped into (48-bit) MAC address. Whereas, In Reverse Address Resolution Protocol (RARP), IP address is fetched through server. Through RARP, (48-bit) MAC address of 48 bits mapped into (32-bit) IP address.
Thanks for the awesome article. Very insightful! In extension, one can also refer “Network Tools for Windows ” for additional information
I’m glad you liked it.
how to check network status port