Using ISA 2004 Firewalls to Protect Against Sasser (v1.01)
by Thomas W Shinder MD, MVP
Got questions? Discuss this article over at
http://forums.isaserver.org/ultimatebb.cgi?ubb=get_topic;f=25;t=000104
The table below lists ports used by Sasser and Sasser variants. These Sasser exploits attempt to compromise a system based on the issues described in MS04-011. You should deny access to all ports known to be used by Sasser.
This data is current as of 12:00 P.M. on August 21, 2003; visit the PSS Security Response Team Alert-New Worm: W32.Sasser.worm (http://go.microsoft.com/fwlink/?LinkID=28658) page for the latest information.
| Port Number | Transport Protocol | Used by Sasser |
| 445 | TCP | Yes |
| 5556 | TCP | Yes |
| 9996 | TCP | Yes |
By default, inbound connections through the ISA 2004 firewall are blocked for these ports. However, if you create server publishing rules for these ports, the published server could be at risk. This can be problematic if you have a front-end Exchange Server in a DMZ segment, because this port must be open between the DMZ segment and the Internal network. However, you do not need to open this port between the External network and the DMZ segment, so your risks are mitigated to a certain extent.
The default firewall policy for the ISA 2004 firewall prevents the spread of Sasser to external networks because Sasser requires outbound FTP to spread. However, if your ISA firewall is configured with an “All Open” outbound Access Rule, then you must create Access Rules to block Sasser on its known ports.
To help prevent outbound Sasser attacks:
- Create an Access Rule blocking traffic on ports listed in the above table. Blocking TCP port 445 in the outbound direction prevents outbound CIFS traffic and blocking TCP ports 5556 and 9996 in the outbound direction will prevent an infected host from acting as an FTP server and spreading the worm.
- Configure the Firewall Client to block malicious Sasser processes. You will have to install the Firewall client on the client operating systems for this method to work. Note that all Windows client operating systems should have the Firewall client software installed (do not install the Firewall client on network servers, unless you have specific and compelling reasons to do so). If all outbound access is authenticated, this will prevent the worm from acting as a Firewall Client through ISA firewall.
The ISA firewall machine is also potentially vulnerable to internal attack by the Sasser worm. In order to protect the ISA firewall itself from a Sasser attack, do not create Access Rules allowing traffic to the Local Host network on the ports listed in the table above.
To block outbound traffic on the known Sasser ports listed the above table:
- Open the Microsoft Internet Security and Acceleration Server 2004 management console and expand the server name. Click on the Firewall Policy node.
- Click on the Tasks tab in the Task Pane. Click the Create a New Access Rule link.
- On the Welcome to the New Access Rule Wizard page, enter Block Sasser Outbound in the Access Rule name text box. Click Next.
- On the Rule Action page, select the Deny option and click Next.
- On the Protocols page, select the Selected protocols option from the This rule applies to list. Click the Add button.
- In the Add Protocols dialog box, click the New menu, then click the Protocol command.
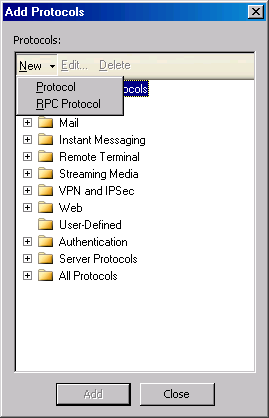
- On the Welcome to the New Protocol Definition Wizard page, enter Sasser Outbound in the Protocol Definition name text box and click Next.
- On the Primary Connection Information page, click the New button.
- In the New/Edit Protocol Definition dialog box, select the Protocol type as TCP. The Direction is Outbound. The From port is 445 and the To port is 445. Click OK.
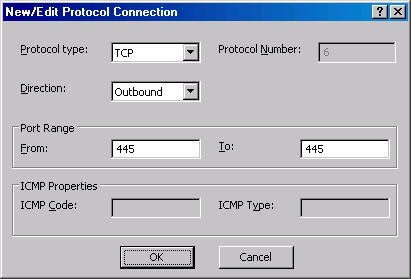
- On the Primary Connection Information Page click the New button.
- In the New/Edit Protocol Definition dialog box, select the Protocol type as TCP. The Direction is Outbound. The From port is 5556 and the To port is 5556. Click OK.
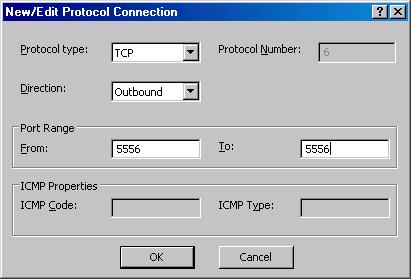
- On the Primary Connection Information Page click the New button.
- In the New/Edit Protocol Definition dialog box, select the Protocol type as TCP. The Direction is Outbound. The From port is 9996 and the To port is 9996. Click OK.

- Click Next on the Primary Connection Information page.
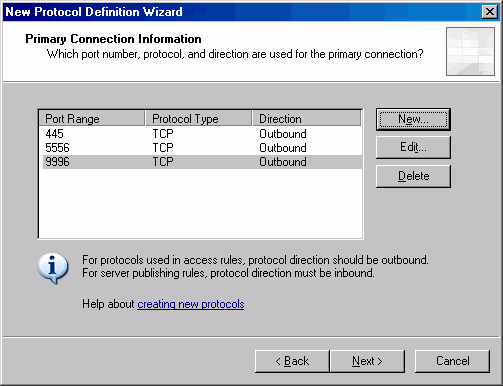
- Select the No option on the Secondary Connections page. Click Next.
- Click Finish on the Completing the New Protocol Definition Wizard page.
- In the Add Protocols dialog box, click the User-defined folder and then double click the Sasser Outbound entry. Click Close.
- Click Next on the Protocols page.
- On the Access Rule Sources page, click the Add button.
- In the Add Network Entities dialog box, click the Network Sets folder and then double click the All Protected Networks entry. Click Close.
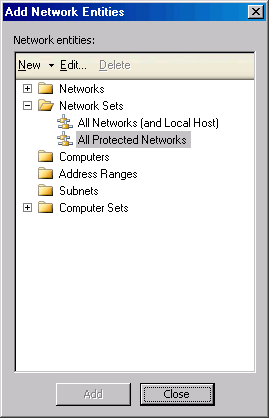
- Click Next on the Access Rule Sources page.
- On the Access Rule Destinations page, click the Add button.
- In the Add Network Entities dialog box, click the Networks folder and then double click on the External entry. Click Close.
- On the User Sets page, accept the default entry, All Users, and click Next.
- Click Finish on the Completing the New Access Rule Wizard page.
- Move the Block Sasser Outbound rule to the top of the list of rules.
- Click Apply to save the changes and update the firewall policy.
- Click OK in the Apply New Configuration dialog box.
The malicious Sasser processes known at this time are avserve and avserve2.
Since the Sasser worm variants also execute as randomly-named processes, the following process is not 100% effective. It will block connection attempts from avserve and avserve2.
To configure the Firewall Client to block malicious Sasser processes:
- In Microsoft Internet Security and Acceleration Server 2004 management console, expand the server name and then expand the Configuration node.
- Click the General node.
- On the General node, click the Define Firewall Client Settings link in the Details pane.
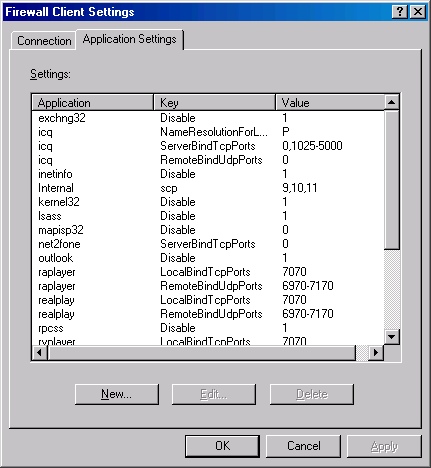
- In the Firewall Client Settings dialog box, click the Application Settings tab.
- On the Application Settings tab, click the New button.
- In the Application Entry Setting dialog box, enter avserve in the Application text box. Select disable from the Key drop down list. Select 1 from the Value drop down list. Click OK.
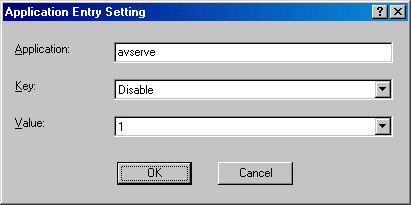
- Repeat steps 5 and 6, but this time enter avserve2 in the Application text box.
- Click OK in the Firewall Client Settings dialog box.
- Click Apply to save the changes and update the firewall policy.
- Click OK in the Apply New Configuration dialog box.
Configuring the Firewall Client for Avserve.exe and Avserve2.exe only prevents the malicious processes on an infected host from acting as a Firewall Client. If the host is also configured as a SecureNAT client, then this setting may have no effect. (To prevent SecureNAT client access across ISA Server, make sure that there are no anonymous Access Rules allowing outbound access to these applications.)
You can test the functionality of the Block Sasser Outbound rule by using Telnet on a client located on an ISA 2004 firewall protected network.
- Open the Microsoft Internet Security and Acceleration Server 2004 management console, expand the server name and then click the Monitoring node in the left pane of the console.
- On the Monitoring node, click the Logging tab in the Details pane.
- On the Tasks tab of the Task Pane, click the Start Query link.
- On a client system located on a protected network, click Start and then click Run. In the Open text box, enter cmd and click OK.
- At the command prompt enter telnet 131.107.1.1 5556 and press ENTER.
- Return to the Microsoft Internet Security and Acceleration Server 2004 management console and view the real time log monitor. You will see entries indicating that the Block Sasser Outbound Access Rule prevented the connection.

You can use a script to block the Sasser ports. Jim Harrison has on his
www.isatools.org site a script that automates the above configuration. Download it at http://isatools.org/block_sasser.vbs
For More Information
- What You Should Know About the Sasser Worm (http://go.microsoft.com/fwlink/?LinkID=28659)
- Microsoft Security Bulletin MS04-011 (http://go.microsoft.com/fwlink/?LinkID=28661)
- ISA Server Product Documentation (http://go.microsoft.com/fwlink/?LinkID=28663)
I hope you enjoyed this article and found something in it that you can apply to your own network. If you have any questions on anything I discussed in this article, head on over to http://forums.isaserver.org/ultimatebb.cgi?ubb=get_topic;f=25;t=000104 and post a message. I’ll be informed of your post and will answer your questions ASAP. Thanks! –Tom
If you would like us to email you when Tom Shinder releases another article on ISAserver.org, subscribe to our ‘Real-Time Article Update’ by clicking here. Please note that we do NOT sell or rent the email addresses belonging to our subscribers; we respect your privacy




