
PowerShell scripts are often used as a tool for performing administrative tasks in bulk. If you’re running a script interactively, then the script can simply operate under your security context. Similarly, the script can simply prompt you for a set of credentials.
However, some PowerShell scripts are specifically designed to run in an automated fashion without administrative intervention. Such scripts usually receive the required permissions by extracting credentials from an encrypted file. The question is- can you decrypt this type of password file, revealing the administrative password in clear text?
In this article, I’ll show you how such a decryption might work. Let’s start with understanding how to create an encrypted password file.
Creating an Encrypted Password File
If you’re authorizing a PowerShell script that you want to run in an unattended mode, then you’re going to need a password file from which the script can retrieve a set of administrative credentials. The trick, however, is that this file doesn’t exist by default. It’s up to you to create the file. Fortunately, it’s relatively easy to do. You can use the following commands to create a password file:
- $Password = Read-Host “Enter Your Password” -AsSecureString | ConvertFrom-SecureString
- $Password | Out-File “C:\Data\Password.txt”
See how simple it is?
The first command creates a variable named $Password. That line will also display the prompt “Enter Your Password.” Whatever you enter gets written to the $Password variable.
Also, you’ll notice that I’m using the -AsSecureString parameter. This causes your input to get masked with asterisks. Finally, I’m using the ConvertFrom-SecureString variable to force the password to get stored within the variable in a usable format.
To show you what this looks like in practice, take a look at the screenshot below. I entered the first line of code and was then prompted for a password. The password that I entered (which is masked in the screenshot) was P@ssw0rd. For the sake of demonstration, I then typed $Password to show you what it contains.
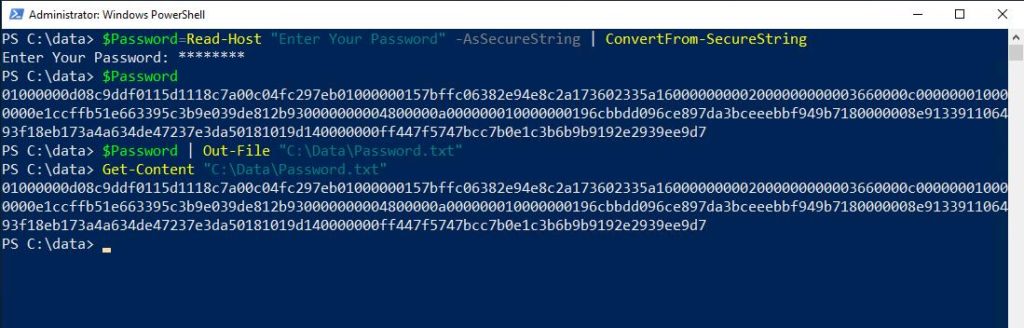
To clarify, the second line of code listed above uses the Out-File cmdlet to take the contents of the $Password variable (the encrypted password) and write it to a text file. In this case, the text file is C:\Data\Password.txt. The screenshot shows how I used the Get-Content cmdlet to display the contents of this file. In turn, you’re able to see that it matches the $Password variable.
Next, I’ll move on to talking about decrypting a password file using PowerShell.
Decrypting a Password File
Now that I’ve shown you how to create an encrypted password file, let’s see if we can decrypt it. Remember, the clear text password is equal to P@ssw0rd in this case.
The first thing that you have to do is to read the password file into a variable by using the Get-Content cmdlet. In this case, I’m just reusing the $Password variable for the sake of clarity. I did, however, clear the variable.
The command used to read the password file into the variable is:
$Password = Get-Content “C:\Data\Password.txt”
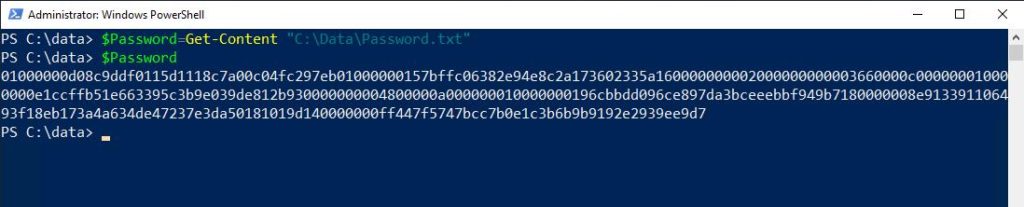
In the screenshot above, I performed the extra step of displaying the variable’s contents as a way of proving that the $Password variable does indeed contain the encrypted password.
Now it’s time to decrypt the password. Here are the commands used to do so:
- $SSPassword= $Password | ConvertTo-SecureString
- $Decrypted=[Runtime.InteropServices.Marshal]::PtrToStringAuto([Runtime.InteropServices.Marshal]::SecureStringToBSTR($SSPassword))
- $Decrypted
The first command creates a new variable called $SSPassword. Here, I’m converting the contents of the $Password variable to a secure string and writing it to this new variable.
The second command is the one that performs the actual decryption. PowerShell cannot do the decryption by itself, so I’m leveraging .NET. In turn, PowerShell runs the instructions against the $SSPassword variable. The results are then written to a new variable that I’m calling $Decrypted. The final line of code displays the contents of the $Decrypted variable, which is the clear text password.
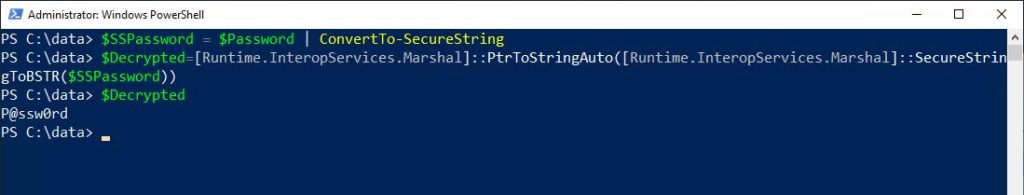
And there you have it. As you can see, it’s relatively easy to learn how to decrypt a password file using PowerShell.
The Bottom Line
In short, secure string encryption isn’t quite as secure as it sounds. This is because you have a way to decrypt the string, revealing the password in clear text. This lack of security means it’s extremely important to protect password files by saving them to secure locations where the file is unlikely to get compromised.
In any case, I hope this article helped you out in teaching you how to decrypt a password file using PowerShell. Feel free to refer back to this short and simple article in the future should you ever need a quick refresher!
Do you have any more questions on using PowerShell to decrypt passwords? Check out the FAQ and Resources sections below!
FAQ
What is the point of using encrypted credentials if PowerShell can decrypt passwords?
While it’s indeed possible to use PowerShell to decrypt passwords, you should encrypt them nonetheless. A clear text password is far more vulnerable to compromise than an encrypted password.
How can I safeguard a stored password if it can get decrypted?
The best option is to use permissions to restrict access to a password file. You should only allow people with permissions to run the script that uses the encrypted password, and no one else. Keep this in mind, and don’t give anyone unauthorized access!!
Is there any reason to worry about restricting access to a password file if there’s a zero chance that anyone in my organization knows how to use PowerShell?
Even if your colleagues don’t know how to use PowerShell, you should still restrict access to that file. If, for example, a hacker penetrates your network, you want to make it as difficult as possible for them to access any credentials. Similarly, restricting access to password files helps guard against accidental deletion.
Can a password file still pose a potential threat if I can somehow protect it against decryption?
Yes, it can. Consider the way that PowerShell normally uses a password file. PowerShell simply reads the file and uses it to acquire the necessary credentials to perform the required operation. To do this, PowerShell only needs to have the ability to read the file. No requirement for PowerShell exists to actually convert the file’s contents to a clear text password.
What are the chances that a hacker will know how to decrypt a PowerShell password?
Hackers know that a password file is still useful in some way even if it’s not decrypted. However, they likely also do know how to decrypt a file. After all, you’re reading a publicly accessible article on password decryption right now. Hackers have access to the same information. That’s why it’s so important to restrict access to password files.
Resources
TechGenix: Article on the Possible Extinction of Web Passwords
Learn why Web passwords may eventually become extinct.
TechGenix: Article on Passwords That Never Expire
Read more on how to use PowerShell to find passwords that are set to never expire.
TechGenix: Article on Employees Selling Their Passwords
Find out why one in five employees would be willing to sell their password.
Altaro: Article on Encrypting Passwords in PowerShell
Discover how to encrypt passwords in PowerShell.
Microsoft: Guide on Managing Passwords with PowerShell
Read more on how to use PowerShell to manage passwords.
N-able: Guide on Using Special Characters in a Password
Read more on how special characters in passwords may cause issues for PowerShell.



