If you would ike to read the first part in this article series please go to:
Introduction
Although Exchange Server 2010 Database Availability Groups (DAG) do a pretty good job protecting data from accidental lost, especially when keeping 3 or more copies of the databases (even better if one of them is a lagged copy), the truth is that many Exchange administrators throughout the World prefer a more hybrid approach. And this hybrid approach usually consists of leaving circular logging turned off (a DAG backup-less solution requires circular logging) and continuing to rely on regular backups, but on a less frequent schedule.
This is where Microsoft System Center Data Protection Manager (DPM) can help, since it was designed to provide specific protection for Windows environments and products, namely SharePoint, Exchange Server, and SQL Server. DPM provides continuous data protection for Exchange Server 2003, 2007 and 2010, through disk-to-disk, disk-to-tape and disk-to-disk-to-tape technologies. DPM supports backing up standalone mailbox databases, active and passive databases in a Database Availability Group (DAG) in Exchange 2010, as well as continuous replication (LCR, CCR and SCR) in Exchange 2007
DPM can be configured to use disk-based, tape-based, and cloud-based backup systems.
- Disk-Based Backup: disk-based backup is used for short-term data protection operations and allows rapid backup and restore of protected data.
- Tape-Based Backup: although protected data is not initially written to tape, DPM allows backed-up data to be copied to tape for the purposes of meeting long-term data retention and archiving requirements.
- Cloud-Based Backup: DPM can be configured to back up data across the Internet to a disaster recovery facility at a separate data center.
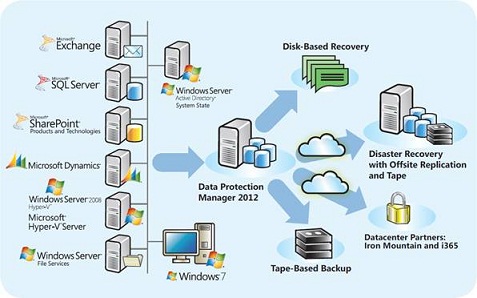
Figure 1 – DPM Backup Process (DPM 2012 Datasheet)
This article will cover the Release Candidate (RC) of System Center Data Protection Manager 2012. Since the last time I wrote about this topic was with DPM 2007, let’s look at the main changes since that version until the latest release.
What’s new in DPM 2010:
- Automatically growth of volumes as required.
- Support to shrink volumes so your space is used effectively.
- Support for system protection of Windows Server 2008 and later editions.
- Support for Exchange Server 2010 Database Availability Group (DAG).
- Improved Windows SharePoint support.
- The DPM Library Management tab now displays the amount of data that has been written to available tapes.
- New SQL Server Self Service Recovery Configuration Tool user interface.
- Enhanced support for SQL Server database administrators, using the SQL Self Service Recovery tool.
- Support for short (quick) erase operation from tape.
- Protection for client computers, like laptop computers, that may not be connected to the network at all times.
- Users of protected client computers can recover their data without waiting for the backup administrator.
What’s new in DPM 2012:
- Centralized management of multiple DPM servers.
- Remote management of DPM servers.
- Support for multiple DPM servers to share one instance of SQL Server for DPMDB.
- Certificate-based authentication for computers in workgroups or untrusted domains.
- Optimized item-level recovery for SharePoint farms.
- Improved usage of tapes through protection group sets.
- Support for protecting VMM hosts.
- Fresh user interface.
And since DPM supports protection and recovery of Exchange Server 2010, let’s look to what’s new for Exchange 2010:
- Protection of a stand-alone Exchange Server 2010 server
- Protection of databases under a database availability group (DAG)
- The procedures to protect and recover Exchange Server 2010 are similar to those required to protect and recover Exchange Server 2007. Since Exchange Server 2010 does not use storage groups, the databases are grouped in the DAG.
The following table lists the types of data that DPM 2012 can protect and the level of data that you can recover.
|
Product |
Protectable Data |
Recoverable Data |
|
Exchange Server 2003 Exchange Server 2007 |
|
|
|
Exchange Server 2010 |
|
|
|
Windows Server 2003 Windows Server 2008 Windows Storage Server 2003 Windows Storage Server 2008 |
|
|
|
Hyper-V |
|
Item-level recovery of:
|
|
All computers that can be protected by DPM except computers running Windows Vista |
|
|
|
Client computers |
|
|
Table 1 – Protectable and Recoverable Data
Some DPM Background…
Let’s do a quick review on the principle behind disk-based data protection in DPM and how it uses the VSS writers provided by the application workloads.
DPM server creates and maintains a replica of the data to be protected. This replica is then synchronized at regular intervals, according to the settings that you define, by protection agents that track changes to protected data.
DPM combines the Exchange Server transaction log architecture with the block-level synchronization. After the initial baseline copy of data using the DPM block-based synchronization engine, two parallel processes enable continuous data protection:
- DPM captures “express full” backups using the Exchange Server VSS writer and the DPM agent to identify which blocks have changed in the database, and send just the updated blocks or fragments. This “translates” to the regular “full backup”, with the DPM server having a complete and up-to-date copy of the data, without the penalty of transmitting everything across the network like a normal “full”.
- Transaction logs are continuously synchronized to the DPM server, as often as every 15 minutes, between express full backups. The log files themselves are replicated by DPM, so you can call this the “incremental backup”.
Figure 2 illustrates the previous described process.

Figure 2 – Exchange synchronization process
At the file level, this is what happens during an Express Full Synchronization process:
- DPM Finds Files That Make Up Data (the database .edb files and the transaction log .log files)
- The DPM filter creates a volume map, to monitor which disk blocks contain portions of the files to be protected, as depicted in Figure 3.
- Changed blocks are noted. Figure 4 and Figure 5 show the Exchange files being modified on disk from time 0:00 to 0:05
-
At time 0:05 a VSS Snapshot is taken on the production volume to ensure consistent data and the changed blocks are sent to DPM server (Figure 5), while live disk continues.
- Frozen blocks from snapshot are released
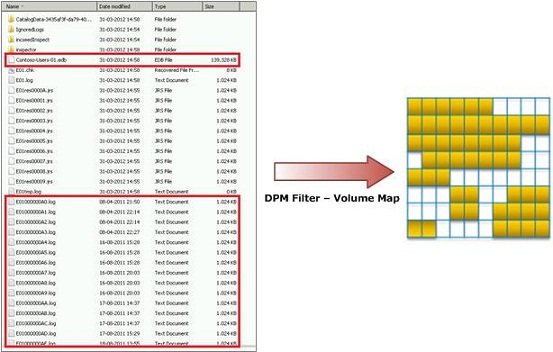
Figure 3 – DPM Filter – Volume Map
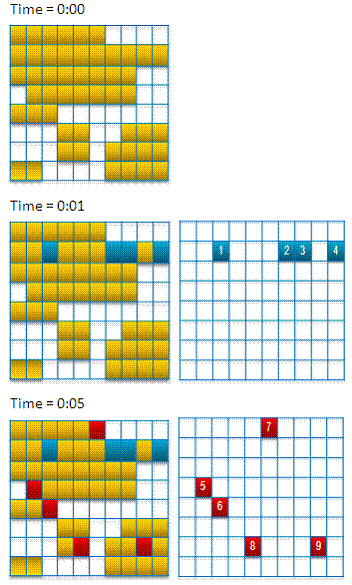
Figure 4 – DPM Filter – Volume Map changes through time
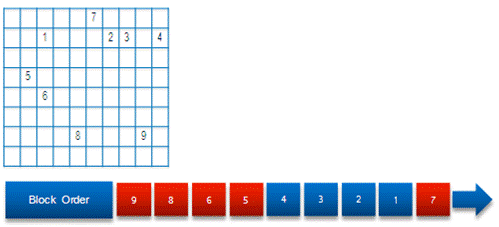
Figure 5 – DPM synchronization
DPM, DAG and Backupless Scenarios
As previously stated, it is possible to build a backupless Exchange infra-structure, as long as you keep 3 or more copies of the databases, being one of these copies, preferably, a lagged copy.
Although one can argue if this is enough or not to protect crucial data, against application errors for example, there are several good reasons to implement DPM in conjunction with DAGs:
-
Less complicated point-in-time (PIT) restoration – DPM allows administrators to perform PIT recovery with several quick selections from an intuitive GUI interface, minimizing the complexity and time required for a restoration.
-
Fewer Exchange servers needed – Leveraging DAGs to provide a comprehensive data protection solution requires that you deploy a minimum of three Exchange mailbox servers: one to host the active mailbox database, one to host the up-to-date copy, and one to host the lagged copy.
-
If you are attempting to also provide offsite backup and recovery, even more Exchange mailbox servers are required. With a DPM solution in place, offsite backup and PIT restores can be handled through DPM with DAGs implemented primarily as a high availability solution.
-
Longer retention range – By design, PIT recovery from a lagged recovery is limited to a maximum of 14 days. DPM enhances the data protection available to administrators by providing PIT restore from outside the 14-day limitation.
-
More consistent backup and recovery process – DPM allows an organization to use a consistent backup and recovery process across multiple workloads such as File servers, SQL, Hyper-V, and SharePoint.
Solution Topology
For the purpose of writing this article, I used the following environment:

Figure 6 – Solution topology used in this article
|
Server Name |
Role |
Software |
|
DPM2K12 |
Data Protection Manager |
Windows Server 2008 R2 SP1 System Center DPM 2012 RC |
|
E2K10 |
Domain Controller Mailbox Server CAS Server HUB Transport Server Unified Messaging |
Windows Server 2008 R2 SP1 Exchange Server 2010 SP2 + RU1 |
|
E2K10-MBX2 |
Mailbox Server |
Windows Server 2008 R2 SP1 Exchange Server 2010 SP2 + RU1 |
|
E2K10-EDGE |
Edge Server FSW |
Windows Server 2008 R2 SP1 Exchange Server 2010 SP1 + RU3 |
Table 2 – List of servers
Configuration Process
Before starting to configure DPM 2012 to protect Exchange Server 2010, there are some pre-requisites that must be met:
- The minimum version of Exchange Server 2010 that DPM 2012 can protect is Exchange Server 2010 with Rollup Update version 1 (RU1).
- The eseutil.exe and ese.dll versions that are installed on the most recent release of Exchange Server must be the same versions that are installed on the DPM server (this will be covered during the article). In addition, you must update eseutil.exe and ese.dll on the DPM server if they are updated on a computer running Exchange Server after applying an upgrade or an update.
- To protect an Exchange Server 2010 DAG node, you must install a protection agent on the node. For instructions about installing protection agents, see Installing Protection Agents.
- It’s possible to protect Exchange Server 2010 DAG nodes from different DPM servers. However, one node can be protected by only one DPM server. For example, assume that CONTOSO-DAG-01 has nodes N1, N2 and N3. One DPM server can protect N1 and N3, and another DPM server can protect nodes N2.
- Windows Server must recognize a storage device as locally attached before DPM can use it for storage. DPM can use direct-attached storage (DAS) or SAN devices attached through iSCSI or Fibre Channel to store protected data. DPM cannot store protected data on removable disk media like USB or IEEE 1394 hard disk drives because these devices are not always attached and do not support VSS unless these devices are part of a VTL solution that appears as a tape device to DPM. Any volumes that are used must be dedicated to DPM.
- Microsoft recommends the use of RAID5 for DPM as this provides the necessary data integrity and storage reliability. When performing this task, design the RAID5 configuration, take the IOPS requirement into consideration and then balance the number of overall LUNs used to meet the IOPS. You must also pay attention to the number of LUNs allocated for the RAID parity bits as this affects the IOPS as well
- With DPM, the maximum amount of data that you can protect with a single DPM server is 80 TB. Therefore you can protect DAG’s that have up to 20 nodes with a single server or up to 10,000 mailboxes with a DPM server.
Protecting Exchange 2010 servers with DPM 2012 can be accomplished with these 5 configuration steps:
- Plan the required storage with Storage Calculator
- Install DPM 2012 server (not covered in this article)
- Configuring disk/tape media for the DPM server
- Install DPM agents and preparing Exchange
- Configuring protection groups
Summary
And this concludes part 1 of this 4-part article. The next part will cover agent installation and the configuration process that will trigger the continuous protection of your Exchange Servers.
If you would ike to read the first part in this article series please go to:



