Monitoring is an important aspect of all networks as it prevents attacks and identifies vulnerabilities at the earliest. Network administrators and IT security personnel are always on their toes to have complete control over what’s going on in their organization’s network and to identify vulnerabilities at the earliest. This is a race against time to identify and fix bugs before cyber attackers get to it. Unfortunately, identifying and fixing vulnerabilities continues to be a highly manual task. In fact, a report by Cisco shows that 35 percent of network strategists believe network troubleshooting is the most time-consuming and resource-intensive activity for network administrators. The good news is many monitoring tools and utilities are available today to ease this workload of network administrators and to enhance their productivity. Out of these many network monitoring tools, Nmap stands out and is even considered as the de facto standard due to its versatility and utility.
In this article, we’ll take a deeper look into this powerful network monitoring tool is and why it is so important for network administrators.
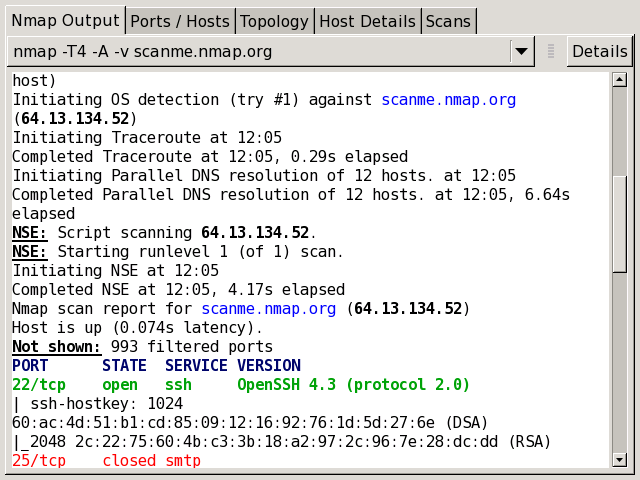
What is Nmap?
Network Mapper, or Nmap for short, is a free open-source tool used to scan networks, identify vulnerabilities, find open ports, discover hosts automatically, and more. It started as a utility for Linux and was ported to Windows, macOS, and other operating systems because of its usefulness. Even today, it continues to be one of the most useful utilities on Linux and Windows.
Nmap features
Nmap is popular because it can do a ton of things for IT security professionals. Some of the key features are:
- Identifies hosts on a network based on different criteria. For example, you can list devices that respond to ICMP requests or those that access a particular open port, and so on.
- Lists the number of open ports in a network, as this is a major vulnerability point.
- Checks remote devices to identify the applications and their versions.
- Detects the underlying operating system and hardware characteristics of devices.
- Gets the accurate path by routing packages to the target machine.
- Monitors hosts to detect and identify a new device or access.
- Provides network information such as DNS names and device types.
As you can see, these features are comprehensive and cover almost every aspect of network monitoring, and it justifies the de facto standard position that it enjoys today.
What can you do with Nmap?
Port scanning is the core functionality of Nmap, but over the years, it has evolved to perform wide-ranging activities for its users. Its true power lies in its flexibility and versatility. Here are some things you can do with this tool.
Port scanning
Nmap sends out packets to other devices, and it comes back with a wealth of information such as IP addresses, network attributes, and more to give you a precise idea of the devices and your network. You can easily create a hardware and software inventory of your network. This is particularly useful for identifying vulnerabilities quickly.
Supports different protocols and operating systems
Nmap supports different protocols such as Transmission Control Protocol (TCP), User Datagram Protocol (UDP), Stream Control Transmission Protocol (SCTP), and Internet Control Message Protocol (ICMP), so you can use it to send messages to a wide range of devices. Also, you can use it on many ports and for many purposes, and this flexibility is what makes Nmap so popular, even 23 years after it was first released.
Host discovery
Nmap can easily discover devices on a network and their physical connections. It can identify all kinds of devices such as servers, routers, and switches, and this makes it particularly helpful for capacity planning and inventory management. It also identifies the service and role of a device. For example, it identifies if a server is used for emails or for application hosting and in the case of the latter, the applications and its versions running on it.
Hardware and operating system details

Nmap provides details of the operating system and the underlying hardware of different devices. This includes comprehensive details such as the name of the operating system, its vendor name, version, and even an estimate of the device’s average uptime, all of which are sure to come in handy for capacity planning.
Security auditing
When you know the operating system, versions, and even the applications running on a server, it becomes easy to identify possible security flaws associated with that operating system and version. It helps with troubleshooting as well, and a network admin can even proactively write scripts to identify those vulnerabilities and troubleshoot them before they impact the network negatively.
Interactive GUI
Zenmap is the interactive GUI of Nmap, and it helps to save scans, compare them, view network topology maps, list ports, store scans, and more.
Thus, these are some of the things you can do with it:
Types of scans
Nmap works by scanning ports and devices to gather pertinent information, using which, you can take proactive steps to secure your network. Here are some supported scan types:
TCP scan

TCP scan is mostly used for IPv6 networks. In this type of scan, Nmap sends a “connect” system call to an operating system to direct it to establish a connection with the target machine. This is a high-level connection often used by web browsers and other network-related applications and is based on a programming interface called the Berkeley Sockets API. Nmap uses the same interface to get status information.
UDP scan
Nmap uses UDP scans to identify the open and vulnerable UDP ports. It is also used to check on incoming requests on the target machine. However, a problem is that UDP can’t send a positive acknowledgment, so there’s always a chance for false positives. Also, if Nmap sends a message to a UDP port that’s not open, the system responds with an ICMP message. Due to these aspects, the UDP scan is not reliable.
SYN scan
SYN scan is similar to a TCP scan, except that Nmap creates an SYN packet, which is nothing but the first packet used to establish a TCP connection. A unique aspect here is that there’s no connection at all, and Nmap analyzes the responses to produce the results.
ACK scan
Nmap uses an ACK scan to check if a port is filtered or not, and this helps to check firewalls and their properties. Most times, this scan is used for checking whether a firewall is stateless or stateful and is distinguished from other scans by the presence of only an ACK flag in the probe packets.
FIN scan
Nmap uses a secretive scan called FIN scan to probe devices that block incoming connections with SYN flags. In other words, FIN scans penetrate into devices that block SYN scans and are highly useful for probing devices that come under IDS programs. But one problem is that some computers can send an RST (reset) packet in response to FIN, so there’s always a chance for false positives and negatives.
NULL scan
Nmap uses NULL scans to stealthily get information from non-stateful firewalls, packet filtering routers, and other devices that have high-security measures to prevent scanning requests. As the name suggests, the header is set to 0, so these packets are not considered valid and hence, can filter through most devices. At the same time, it’s important to note that this scan doesn’t follow the RFC 793 standard and can’t distinguish open ports from filtered ones.
Xmas scan
Xmas scan was once considered a stealthy scan but is not used so much now because devices have evolved to identify it. Still, Nmap uses a Xmas scan to manipulate packets that can’t be identified by stateless firewalls and some Intrusion Detection Systems (IDS), especially if they are not configured well.
IDLE scan
An IDLE scan is one of the stealthiest and most advanced scans as it gives complete anonymity. In this scan, Nmap doesn’t send packets from your real IP address, rather from another host in the target network. Thus, these are some of the different scan options available for you.
Nmap commands
Let’s take a brief look at some of the popular commands:
Purpose |
Nmap command |
Example |
| Basic scan | Nmap “Ip” or nmap “hostname” | Nmap 1.1.1.1 or Nmap google.com |
| Scan specific port | Nmap -p “port number” “Ip address” | Nmap -p 80, 84 11.1.1.1 |
| Scan an entire port range | Nmap -p “port range” “IP” | Nmap -p 1-80 1.1.1.1 |
| Scan multiple IP addresses | Nmap “IP addresses” | Nmap “1.1.1.1 2.2.2.2 3.3.3.3” |
| Scan hosts from a text file | Nmap -iL “text file” | Nmap -iL iplist.txt |
| Scan the top ports | Nmap –top-ports “number of ports” “IP” | Nmap –top-ports 10 1.1.1.1 |
| Discover hosts | Nmap -sn “IP” | Nmap -sn 1.1.1.1 |
| Disable DNS resolution | Nmap -n “IP” | Nmap -n 1.1.1.1 |
| Detect the version | Nmap – sV “IP” | Nmap -sV 1.1.1.1 |
| Detect operating system | Nmap -o “IP” | Nmap -o 1.1.1.1 |
As you can see, Nmap is a monitoring utility that gives comprehensive information about devices. It uses different scans to gather information from different devices, and this helps network administrators to proactively understand vulnerabilities and thwart attacks. Ready to give it a whirl? You can download Nmap here.
Featured image: Pixabay



