
High traffic causes networks to slow down. But, you can use network management to manage this heavy traffic. When you do that, the overall network performance improves. Also, it can help you achieve Quality of Service or QoS. The two most common network management techniques are traffic shaping and traffic policing.
In this article, I’ll look at traffic shaping and traffic policing. In addition, I’ll look at their benefits and drawbacks. Lastly, you’ll learn about their use cases.
What Is Traffic Shaping?
Traffic shaping or packet shaping is a popular bandwidth management technique that helps companies control outbound traffic.
Moreover, this technique helps some applications perform better by allocating them more network resources. More specifically, it controls bandwidth allocation. It’ll reduce the bandwidth consumption of some applications and allocate those resources to the essential applications to improve their performance.
As a result, it’s responsible for essential applications, protecting them against latency or delay issues.
A network that has too many data packets faces packet loss or delay. This is also called network congestion.
To avoid congestion or delay, you can use the leaky bucket algorithm. In essence, this algorithm controls the traffic rate in the network, allowing you to determine the rate of data packets for each application.
In addition, packet queuing also prevents data loss when a network has too much traffic.

Source: Techgenix
Benefits of Traffic Shaping
- Buffers excess network packets to prevent data loss
- Makes network traffic more consistent
- Improves the overall network performance
Drawbacks of Traffic Shaping
- Slows down the overall network due to queuing
- Allocates bandwidth resources inefficiently
Let’s now look at some practical applications of this bandwidth management technique.
Use Cases and Applications
Traffic shaping is a good option for TCP-based applications. Moreover, companies with centralized servers should use it to manage heavy traffic loads.
The most common use cases of network shaping include audio-video bridging, automatic bank teller (ATM) machines, and internet service providers (ISP). In particular, data centers use it to meet service level agreements (SLAs).
Further, you can use it to allocate the highest bandwidth resources to some programs or data packets. For example, it helps you prioritize specific packet types (such as voice packets) over data packets in the cloud or VoIP calls.
Next up, we’ll discuss traffic policing.
What Is Traffic Policing?
Traffic policing is another network management and monitoring technique. Specifically, it limits or discards extra data packets that cross the predetermined traffic rate.
Moreover, traffic policing manages both inbound and outbound network traffic. Plus, it ensures the proper distribution of network resources.
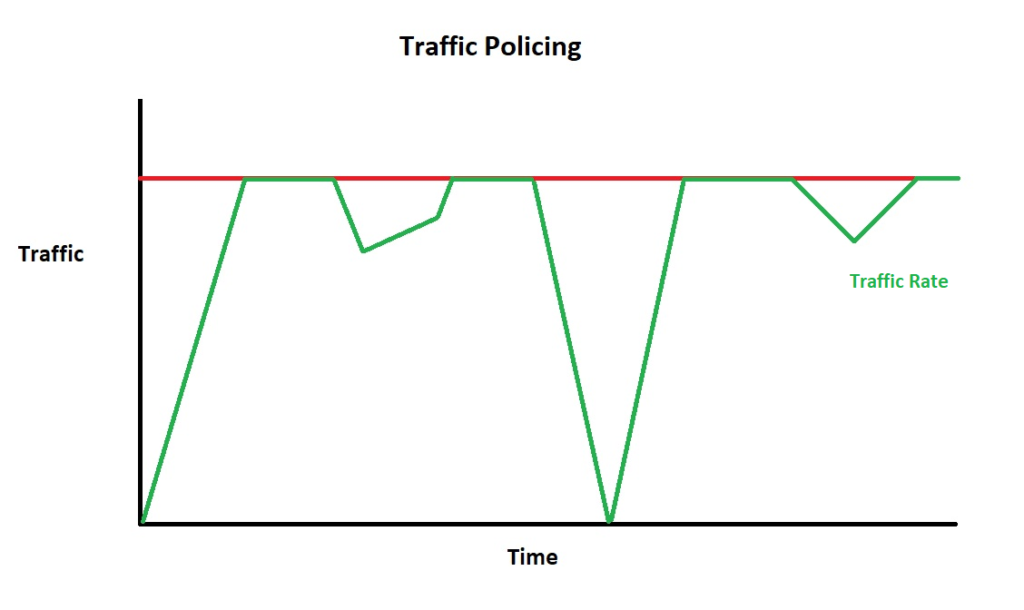
Source: Study-ccna
Benefits of Traffic Policing
- Avoids network delays due to queuing
- Controls the overall network traffic
Drawbacks of Traffic Policing
- Doesn’t apply in EtherChannel interfaces
Use Cases and Applications
Traffic policing is the better option for media-based applications and networks, which include video, voice, and UDP-based communication.
Traffic policing is a lot easier to do than traffic shaping. In essence, any networking environment or application can use traffic policing. Traffic policing is compatible with client-server or distributed networking models, transactional systems, etc.
Now, let’s look at some of the major differences between traffic shaping and traffic policing.
Traffic Shaping vs Traffic Policing
Basically, both traffic shaping and traffic policing carry out the same functions. But, the two vary in a lot of ways as well.
Here are the main differences between traffic shaping and traffic policing.
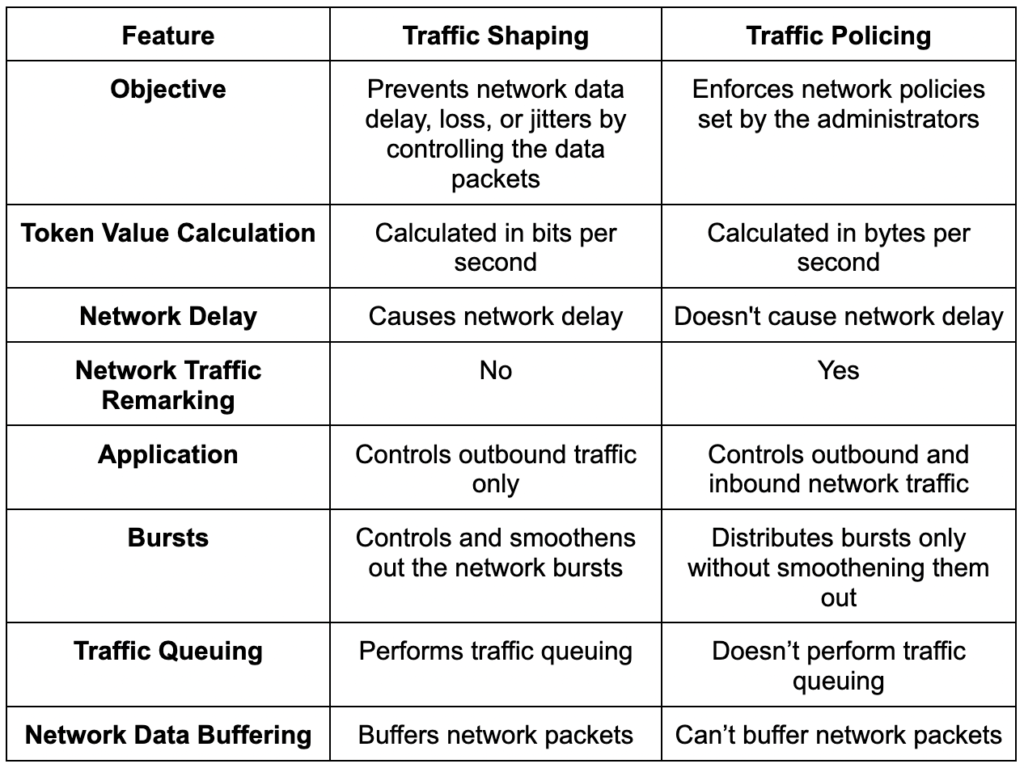
Final Words
Companies need network traffic shaping and policing to manage their network infrastructure.
In this article, I described network traffic shaping and policing. Both these network management techniques ensure the best network performance. But the two are also different from each other.
Traffic shaping uses queuing to prevent data loss, which leads to buffering and delay. Where traffic policing discards extra data packets that exceed the set limits, traffic policing ensures the proper distribution of bandwidth resources to help improve performance in essential programs.
Do you have more questions about traffic shaping or traffic policing? Check out the FAQ and Resources sections below.
FAQ
What is UDP?
The User Datagram Protocol (UDP) is a communication networking protocol that transfers data between endpoints. Video streaming applications often use UDP. However, it doesn’t always guarantee the delivery of data.
What is TCP?
The Transmission Control Protocol (TCP) is a networking protocol that transfers information between endpoints. TCP guarantees the delivery of data packets for emails, FTP, or peer-to-peer data transfers. Moreover, TCP-based applications require traffic shaping.
What is an SLA?
Service providers and their clients work under service agreements. These are called SLAs (service level agreements). Under SLA, service providers provide services within a given timeframe. SLAs quantify services. Moreover, you can use them to measure the efficiency of traffic shaping and policing.
What is packet queuing?
Packet queuing is the process of storing network packets so you can use them later. It prevents data packet loss, handles latency, and retains data packets for later use.
What is the leaky bucket algorithm?
The leaky bucket is a network algorithmic approach that prevents excessive data use. This algorithm helps in data transmission in telecommunication networks.
Resources
TechGenix: Article on Network Observability and Network Monitoring
Learn about the differences between network observability vs network monitoring.
Cisco: Guide to Traffic Shaping and Traffic Policing
Here is a guide on the implementation and application of traffic shaping and traffic policing.
TechGenix: Article on WAN Optimization Tools for SMBs
Learn about several different WAN optimization tools and techniques for small and medium businesses.
TechGenix: Article on the Top 5 Network Security Tools
Discover the top network security tools for your organization.
TechGenix: Article on the Importance of Network Security
Learn about the importance of network security and how it’s essential for your company.



