
SOURCE: Public Domain Pictures
Have you ever wondered how your network works? The Open Systems Interconnection (OSI) model might have the answer. This model helps you convey traffic data using different operations paired with the protocols needed to run those operations. The model itself consists of several layers, one of them being the network layer. This layer is usually a target for many cyberattacks. This is why you need to learn how this layer works to securely traffic data without fear.
In this article, I’ll go over the OSI model, how it stacks up to the modern TCP/IP protocol, and how you can protect your network from malicious attackers.
What Is the OSI Model?
The OSI model is an industrial standard for network connectivity used to describe how a network works. Published in the 1980s by the International Organization for Standardization (ISO), the model seeks to provide a standardized way of networking devices efficiently.
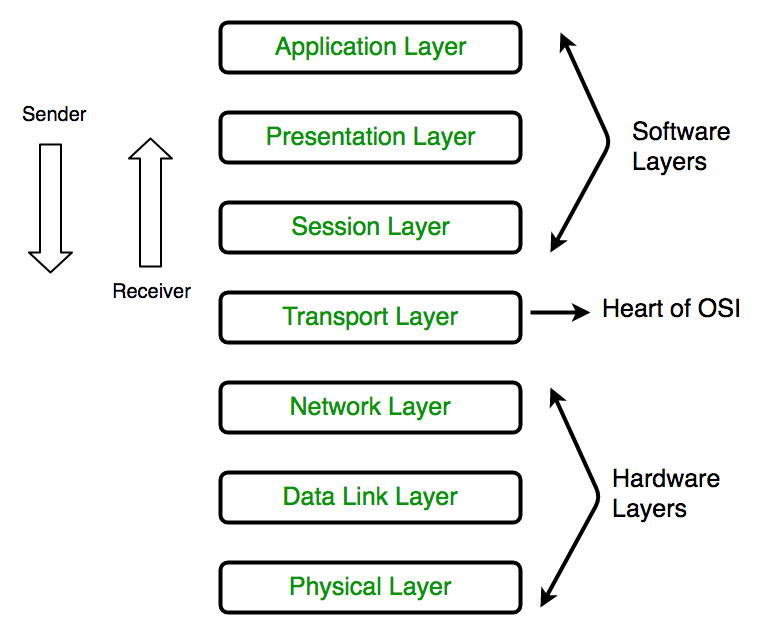
Source: GeeksforGeeks
Today, the more effective Transfer Control Protocol/Internet Protocol (TCP/IP) model replaces the OSI model. However, it’s important to note that many companies still use the OSI model to visualize and communicate network operations. Understanding the OSI model can help you understand what’s going on in your network. Additionally, it can help you isolate and troubleshoot any network issues.
As mentioned earlier, this article focuses on the network layer. The main function of this layer is to handle data routing through your network. I won’t go into too much detail on the other layers, but you can find a detailed explanation of each in this article. That said, let’s now look at the OSI model compared to the TCP/IP model in more detail.
OSI Model vs TCP/IP Model

SOURCE: Free Images Live
The critical difference between OSI and TCP/IP is that the latter collapses several OSI layers into 4, making it more efficient at sending data. That said, merging layer functionality also makes it more difficult to understand. In turn, this can make problem-solving a bit more complex.
Overall, TCP/IP’s application layer combines OSI layers 5, 6, and 7. Likewise, OSI layers 1 and 2 comprise the Network Access Layer in TCP/IP. Therefore, you can think of TCP/IP as a more functional model used to solve specific communication problems based on standard protocols. On the other hand, OSI is easier and better for humans to understand.
Speaking of protocols, it’s time to delve deeper into the world of network layer protocols!
6 Network Layer Protocols You Should Understand

SOURCE: PickPik
Plenty of protocols exist other than the widely adopted internet protocol (IP). Network protocols at Layer 3 include those used for secure communications as well as network dynamic routing, translations, and redundancy.
As an IT admin, it’s important to know all about the common protocols you might encounter, how they work, and what differentiates them. In turn, this will allow you to make better-informed decisions regarding network security overall.
Below, you’ll find several common protocols and their advantages and disadvantages. Let’s begin with Internet Protocol Security (IPsec).
1. Internet Protocol Security (IPsec)
IPsec is a secure network protocol that uses authentication and data encryption. It’s useful for securing your network traffic from cyberattackers.
Advantages
- Provides transparency to apps since it doesn’t impact network layers (your users never need to worry about IPsec configuration)
- Allows you to monitor all the traffic that passes over your network
Disadvantages
- Has issues connecting networks due to firewall restrictions if a network admin doesn’t obey the IPsec protocol
- Allows bad actors to exploit potentially hackable security algorithms found in the protocol
2. Hot Standby Router Protocol (HSRP)
HSRP is a virtual network path redundancy protocol that helps reroute traffic if the primary “active” router fails. An HSRP system always has an active and standby router. It makes router assignments based on the IP address assignments for each device and if the active router is reachable.
Advantages
- Supports configurable MAC addresses and can differentiate between physical and virtual addresses (this allows nodes to use HSRP as the first destination to start routing IP traffic)
- Allows IP redundancy and provides maximum IP redundancy for peer-to-peer networking apps as they use this protocol extensively
Disadvantages
- Has the issue of always making one of your gateways fully idle (due to the utilization of a single HSRP group between devices) until the active device fails—to remediate this poor utilization, you can use multiple HSRP groups to get the most out of this protocol
- Lacks load balancing in a multiple active router environment
3. Open Shortest Path First (OSPF)
OSPF is a dynamic routing protocol that connects networks using the shortest path for packets to travel. This protocol effectively deprecated the older Routing Information Protocol, or RIP for short (more on this later).
Advantages
- Multicasts any network changes or changes to a routing table to all OSPF hosts
- Takes into account additional network info, like admin-provisioned cost metrics, for traditional router hops (they’re no longer based on latency)
Disadvantages
- Requires you to have advanced knowledge about complex networks, making it difficult to learn and use compared to other protocols
- Isn’t scalable with more routers, which makes it unsuitable for routing across the internet
4. Routing Information Protocol (RIP)
Much like OSPF, RIP is a dynamic routing protocol. However, unlike OSPF, it’s less efficient during routing table updates.
Advantages
- Is an established and trusted routing protocol used for many years
- Promotes load balancing
Disadvantages
- Consumes more resources than OSPF due to inefficient table updates
- Doesn’t allow path prioritization based on a cost basis
5. Network Address Translation (NAT)
The NAT protocol maps an IP address to another by changing the header of IP packets while in transit using a router.
Advantages
- Obscures sender and receiver IPs, making it able to stop bad actors from mapping and targeting your network intrusion prevention servers
- Decreases the number of IP addresses you need
Disadvantages
- Is very time-consuming when it comes to IP address conversion
- Requires memory and other resources to convert local and global IP addresses
6. Virtual Router Redundancy Protocol (VRRP)
VRRP stops your virtual network routing from having a single point of failure associated with a static routed environment. Moreover, an election process dynamically assigns primary router responsibility to one of the VPN concentrators on your network. In brief, this is useful if a multicast packet transmission fails to ping a designated router.
Note: A VPN concentrator is a router designed to manage VPN connections.
Advantages
- Reduces failover time if a primary router becomes unavailable
- Provides redundancy for a load-balanced routing solution
Disadvantages
- Requires additional VPN concentrators and associated resources to operate
- Requires bandwidth to function in the case of multicast packet transfer
As you can see, each protocol has its unique strengths and weaknesses concerning security. With this knowledge, you’re now ready for the top 5 ways to protect your network layer.
Top 5 Ways to Protect Your Network Layer

SOURCE: PickPik
It’s been a long journey, hasn’t it? You’ve come far. But we’re not done yet. With this information in your arsenal, all that’s left is to talk about defending your network layer. Below, you’ll find the top 5 ways to defend your network layer from cyberattackers and their deadly attacks.
1. Utilize Traffic Shaping
Traffic shaping is a bandwidth management technique designed to delay the flow of data packets. You’d typically use this technique to improve overall network performance and end-user experience. Your network hardware sends data at one speed based on the transmission means used.
To stop your infrastructure from transmitting every bit that comes to it, you can group data into “buckets”. Traffic shaping defines the periods when you don’t send information, as well as the bucket size you use. Overall, this results in more data getting sent out efficiently.
With traffic shaping, you can defend your network against denial-of-service (DoS) attacks designed to max out your bandwidth. Additionally, the technique protects your networks and apps from traffic spikes, regulates bad actors, and prevents attacks designed to consume network layer resources.
Traffic shaping occurs on the application layer (Layer 7) using HTTP. The presentation layer (Layer 6) encrypts your data using HTTPS to protect your network and stop interception by bad actors. These two processes overall help protect your network layer. It’s also a good idea to use network security solutions that allow you to implement HTTPS across your network and provide you with a VPN solution for off-site connections.
2. Segment SD-WAN Traffic
A wide-area network (WAN) connects remote site networks, effectively extending your LAN network. Traditionally, ISPs would charge a premium to provide this service. A software-defined wide area network (SD-WAN) is a virtual WAN that allows you to leverage any combination of connection services, such as MPLS and LTE, to achieve a cost-effective WAN.
SD-WAN is an overlay technology independent of how you send your network or connections. SD-WAN vendors often provide cloud-based software to help you create one with ease.
Some SD-WAN solutions support subinterfaces on the network layer (Layer 3) to help the solutions work with firewalls to segment network traffic. To do this, you’ll need to configure VMware or similar to allow the SD-WAN to use this layer first. Also, consider setting up a static IP address that uses the Dynamic Host Configuration Protocol (DHCP) to get the address.
Lastly, to maximize your network layer security, consider using a next-generation firewall (NGFW) that supports SD-WAN to allow you to screen and filter traffic across your network.
3. Perform Security Audits
Your network is never static and grows continually to meet the needs of the business. Due to this, it’s best practice and often a regulatory requirement to conduct security audits.
To do this effectively, use a security solution with automated reporting capabilities. This allows you to speed up the process and attain high-fidelity security data. When conducting security audits and assessing your network security, you should consider all of the layers in the OSI model, including the network layer.
4. Create a Backup and Recovery Strategy
You need a data backup and recovery plan to provide data redundancy should bad actors destroy or encrypt your production environment data. Backup and recovery plans depend on your risk tolerance to data loss, your existing infrastructure, and the time needed to resume operations.
In terms of data, you need to consider the security of your data in transit. Even for onsite data transfer, if you send unencrypted data, a bad actor can copy and read it. With endpoint encryption, even if someone intercepts your data packets, no one can read them.
5. Encrypt Your Data
Encrypting data often involves sending a key to a data recipient that enables them to unencrypt data using HTTPS. Bad actors intercepting encrypted traffic are unable to read data packet bodies. In short, encrypting your internal and external network traffic effectively protects your business data. This includes intellectual property,credentials, and your business strategy.
To roll out encryption, use an endpoint VPN solution that remote workers can use. Also use a total security solution that encrypts all your network traffic. You should always look for routers that support encrypted technology. These routers allow mobile devices with automated updates to connect using encryption without having the user set it up.
Lastly, you can reduce your security implementation workload with a unified threat management solution that adds multiple security features in one package. In essence, this reduces the risk of you missing an attack vector.
You’ve come so far, so I think It’s now time for a recap!
Final Thoughts
Overall, the OSI model can help you understand your network and network traffic in more detail. Through this model, you can efficiently manage your network. As discussed, your network works with a series of protocols to format and transmit data between endpoints. These protocols help you understand network traffic; each has unique strengths and weaknesses, as outlined above.
When protecting your network, you can use traffic shaping and SD-WAN traffic segmentation techniques. Additionally, you can also protect your network by performing security audits as your business grows or when required. Finally, creating a backup and recovery strategy and encrypting your data can be lifesavers in difficult situations.
Do you have more questions about network layers? Check out the FAQ and Resources sections below!
FAQ
Can I use a network management solution (NMS) to shape network traffic?
Yes, an NMS can monitor and manage network traffic and stop bandwidth-consuming attacks like DoS attacks. Also, traffic shaping is the most impactful way to optimize your network traffic. When optimized, you need fewer infrastructure resources and can improve the quality of service (QoS) end-user experience.
Does a vulnerability assessment solution miss network threats?
Yes, scanning tools used in vulnerability assessment utilities will only find some network threats as they work at the OSI model’s application layer (Layer 7). Due to this, you should use a unified threat detection solution that complements your vulnerability assessment utilities.
Should I switch from HTTP to HTTPS for all my network traffic?
Yes, HTTPS encryption protects your data packet contents from cyberattackers between endpoints. You never know if a cyberattacker is already present in your network. For instance, they might use wired or wireless data sniffing techniques to access your company’s valuable data. To this end, switching to HTTPS helps improve your overall security.
Can next-generation firewalls (NGFWs) protect IoT and edge devices?
Yes, NGFWs cater to modern network hardware, including IoT and edge devices. NGFWs have built-in features that enable you to create filtering rules based on IoT and edge device traffic. Use NGFWs to encrypt all network traffic by default.
What is TCP/IP?
Two protocols often used to transmit data packets on your network are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP). The term “TCP/IP” refers to both protocols due to their common usage. In short, the difference is that UDP doesn’t send an acknowledgment, and the sender doesn’t wait for one; it’s faster but leads to packet loss.
Resources
TechGenix: Article on Cloud Data Security
Discover how you can protect your cloud data from cyberattacks.
TechGenix: Article on Stateful and Stateless Firewalls
Learn the differences between stateful and stateless firewalls.
TechGenix: Article on Cybersecurity and Network Security
Find out what differentiates cybersecurity from network security.
TechGenix: Article on Cybersecurity Strategies
Get to grips with the best cybersecurity strategies you can use to protect your business.
TechGenix: Article on Network Management Solutions
Educate yourself on what a network management solution is and how it can improve your overall network security.



