Application layering is a relatively new addition to IT, but it is gaining popularity among administrators. With its adaptability in delivering particular apps to the specific users who need them, it’s no wonder why.
This tool can help to simplify certain tasks with its ability to deliver the needed apps to a user’s virtual desktop without actually installing these on that OS. This way, even fewer base images are required, making the IT administrator’s job simpler.
What exactly is application layering?
With application layering, administrators are able to separate Windows applications from the underlying infrastructure and send particular virtual apps to users, depending on given circumstances, without the need for installation.
There are many application-layering tools, and they’ll take your given requirements to show particular layers to certain users. The apps with the specific layers are assigned to the virtual desktops and run with native interoperability with the host OS.
Being able to revise, update, and manage the apps separately from a virtual desktop gives more simplicity to the admin, who now has the ability to work with fewer base images as the apps aren’t installed within the virtual image.
In fact, it’s even possible to deploy just one golden image, revoking the necessity of deploying numerous base images separately for each user or group. With this, the admin will have the ability to patch and update applications on numerous PCs immediately by doing it only once.
It’s important to recognize that application layering is not the same thing as virtualization; the layered apps do interact with the operating system, as well as any additional apps on the OS, as though the app were installed locally.
Therefore, it is more common to use application layering when the apps communicate with things like the user’s kernel drivers or other locally installed apps.
How do the layers function?
There are numerous application-layering tools, and they don’t all work in the same way. However, there is a three-layer structure they do adhere to, typically existing as a virtual hard disk file.
Well explained by TechTarget, they write, “The bottom layer is the virtual desktop’s primary hard disk, where the virtual desktop operating system lives. The middle layer is home to everything that puts meat on the app’s bones, including binaries, [application-specific] registry keys, drivers and more. The final layer hosts users’ profile data and keeps it separate from the operating system.”
To go more into detail about the important, middle section, it essentially holds the application as a virtual hard disk. Various tools create this middle layer in a couple of different ways.
One way is by intercepting write operations while the application is installing. This would need to be “initiated just prior to installing a copy of the application onto a clean operating system.” From this, these operations would be written to a virtual hard disk that becomes a layer.
Another way to create this is by creating multiple disk snapshots before deployment of an app. Then, you’ll be left with a virtual hard disk with necessary application information.
The final layer hosts the OS’s user profile and “it is designed to isolate the user profile from the virtual desktop OS to preserve the operating system’s integrity.”
So, the layer is essentially stored files and registry keys that occur during a typical software installation that makes the OS aware of the application. These changes made to the PC during and after installation are stored in a virtual disk and isolated by each “layer.” Thus, the application can act as though it were locally installed.
Using this process, you are able to give each application a layer, allowing a certain amount of separation between applications and delivering specific combinations to particular users.
Differences between application layering and virtualization
Of course, the main difference here is that application layering is dependent on the operating system, whereas apps are packaged so they are able to run independently of the OS with application virtualization.
However, one of the benefits to application layering (depending on your needs) is that applications are able to communicate with each other so no isolation issues arise. As virtualized applications run in isolated spaces, they can’t usually interact.
Keep in mind that these are two very different processes that can’t typically serve as replacements for each other. Application layering comes in handy if your application needs to be able to communicate with devices, kernel drivers, plug-ins, or additional applications.
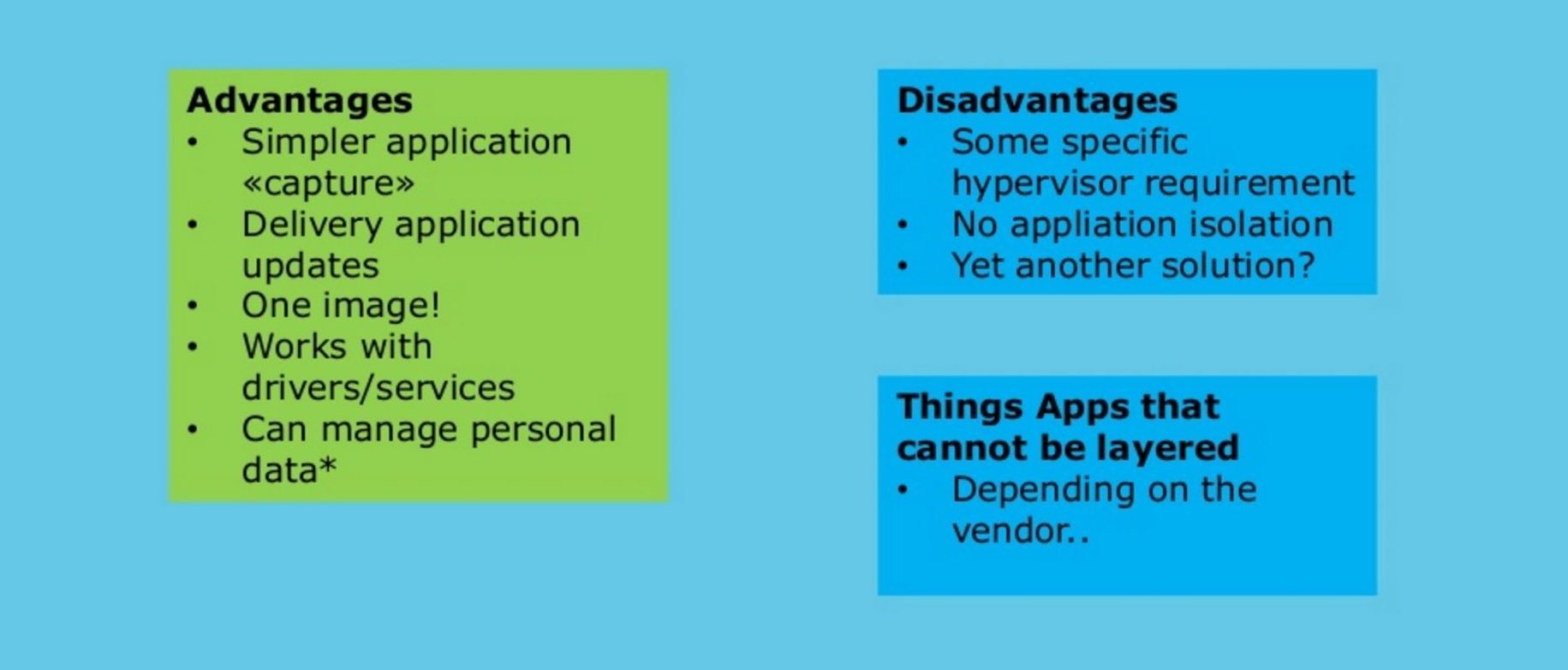
Benefits
There are quite a few benefits to application layering, some of which have already been mentioned. For example, administrators are able to work with a much smaller number of base images than when working with virtualization. This is a benefit in both virtual and physical environments (although be sure to check that the tool you use works with physical desktops).
Users are also more free from vendor lock-in, better application flexibility, typically pay a lower cost, and have more flexible disaster-recovery options. Additionally, users don’t need to worry about applications being unable to communicate.
As you may know, some applications are difficult or even impossible to virtualize for various reasons, often because of the isolation. However, as application layering does not have this characteristic, it has more portability and fewer compatibility issues. Of course, this is considering that it is compatible with the operating system. If not, virtualization is your only option between these two tools.
Because of the smaller amount of base images necessary, it’s easier to deliver, patch, and update applications quickly. By updating or patching one application, you can send this update to every applicable desktop in the company.
Because this saves time, it also saves money. Layering also gives organizations a very cost-effective strategy if they choose to transition from physical PCs to virtual or remote desktops.



