The woes for Google Play Store just keep piling up. Once again, I’m sorry to report, the onslaught of infected applications is in full swing, proving how far the tech giant is from protecting consumers. The culprit this time, the Bankbot banking Trojan, is not new, as it has been observed in the wild by security researchers since February. Unfortunately, one of the places it was initially seen in action was the Google Play Store. Now it has returned to the store, proving just how easy it is for certain hackers to repeatedly bypass the vetting process.
In a blog post by ESET researchers, it was detailed how Bankbot had reentered the Google Play Store despite the company removing apps infected with the Trojan in the past. The attack method was complex in nature, as the post states:
The variant we discovered on Google Play on September 4 is the first one to successfully combine the recent steps of Bankbot’s evolution: improved code obfuscation, a sophisticated payload dropping functionality, and a cunning infection mechanism abusing Android’s Accessibility Service.
The end result was Bankbot appearing in a malicious app called Jewels Star Classic, which appears to be a deliberate attempt to confuse users looking for the legitimate app Jewels Star. This in turn created a situation in which roughly 5,000 users downloaded the infected app before its removal from the Google Play Store.
So what can victims expect if they accidentally downloaded the Bankbot-infested application?
Upon download, Jewels Star Classic will initially appear to be a normal Android mobile game. After 20 minutes of the first running of the application, however, the malicious software will begin its assault on your system. First the user will be prompted with the below message about enabling a real-sounding but fake service called “Google Service.” (This is not to be confused with the real “Google Play Services,” although, of course, many users will be.)
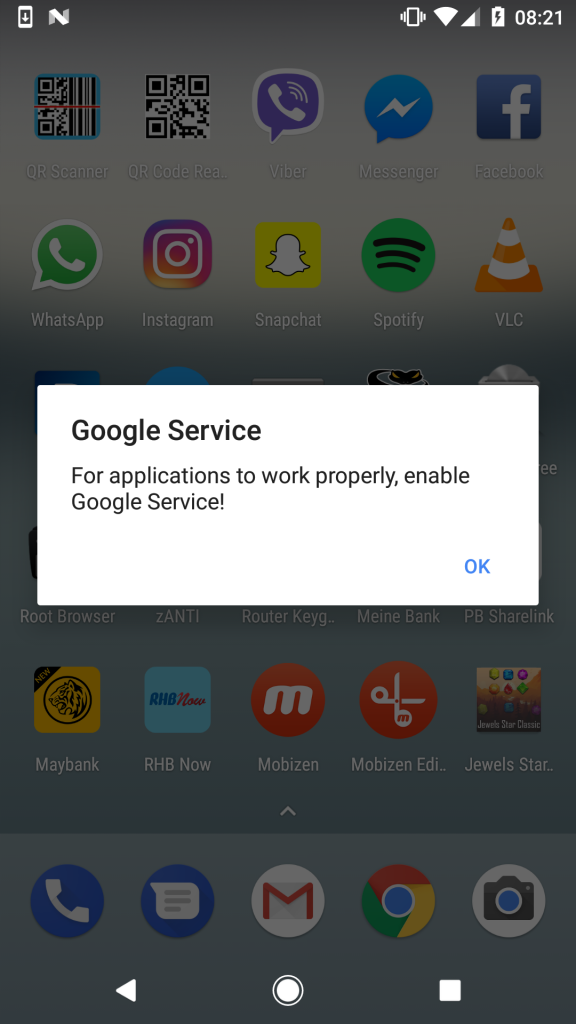
The message will not disappear until “OK” is selected, which shows that the Trojan is already beginning to take over your device. Upon selecting “OK,” the user will be taken to the Android Accessibility menu where the malicious “Google Service” option has been inserted, shown in the below image:
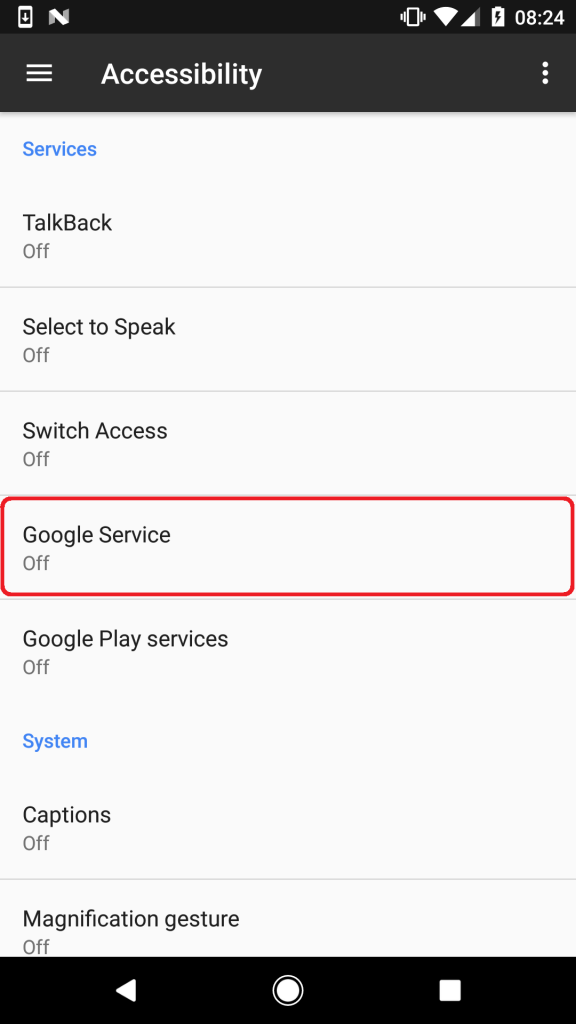
If the user chooses to turn the Google Service option on, they are met with the following permission requests:
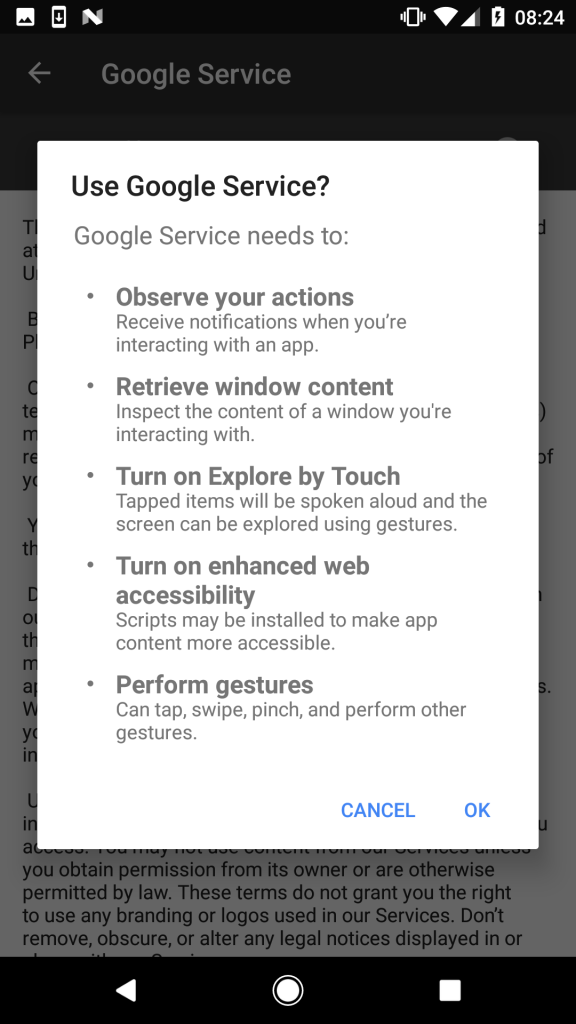
Once these are accepted, the malicious app is now able to carry out its nefarious plans. It will proceed to, under the guise of an “update screen” that covers the actual activity, force the system to install apps from unknown sources, install all of Bankbot’s assets, make Bankbot the default SMS messenger, and finally make Bankbot the device’s administrator.
The Trojan then proceeds to work on stealing banking credentials from the victim. Its method of attack is different than other Bankbot variants in that it will focus entirely on the Google Play app. When a user opens Google Play, Bankbot will force a screen on them that makes it seem like Google is requesting your banking info for records purposes (see below):
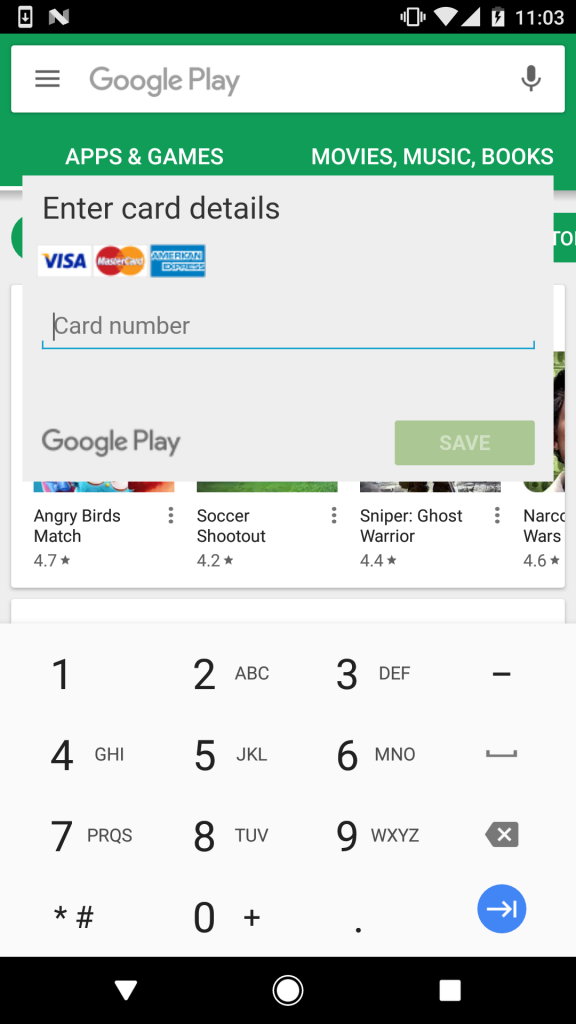
So what can you do to take action against this Trojan? The best course of action is to pay close attention to what gets installed on your device, as well as any apps that ask for absurd permissions. If you notice any unauthorized downloads that didn’t exist before, such as the malicious “Google Service,” take proactive measures to uninstall everything associated with the infected app. Disable device administrator rights for “System update” and then proceed to delete the app and anything else that recently appeared on your device.
This will not be the last we see of Bankbot, as its authors are getting very creative in how they approach their attacks. Stay aware of this nasty little program and also be aware of just what it is you are downloading in app stores.
Photo credit: Shutterstock



