Cisco recently expanded the capabilities of its Stealthwatch platform. Now, the security and analytics product can help organizations detect threats in both encrypted and unencrypted traffic areas across public multicloud environments and private networks.
Here’s some more information about this security platform update, including the specific features and benefits.
Benefits of Cisco Stealthwatch
Today’s cybersecurity professionals have been tasked with detecting threats across a wide array of environments. Organizations often store data on multiple public cloud platforms and on-premises environments, all of which can require different types of monitoring, especially when some network traffic is encrypted and some is unencrypted.
The new Stealthwatch platform gives your security team a single platform to detect threats in a uniform way across all of those different environments. This allows network architects to spend more time and energy creating modern architecture solutions. And it allows DevOps teams to create more blobs, clusters, functions, and other resources without worrying about how your organization will store and protect them.
Features
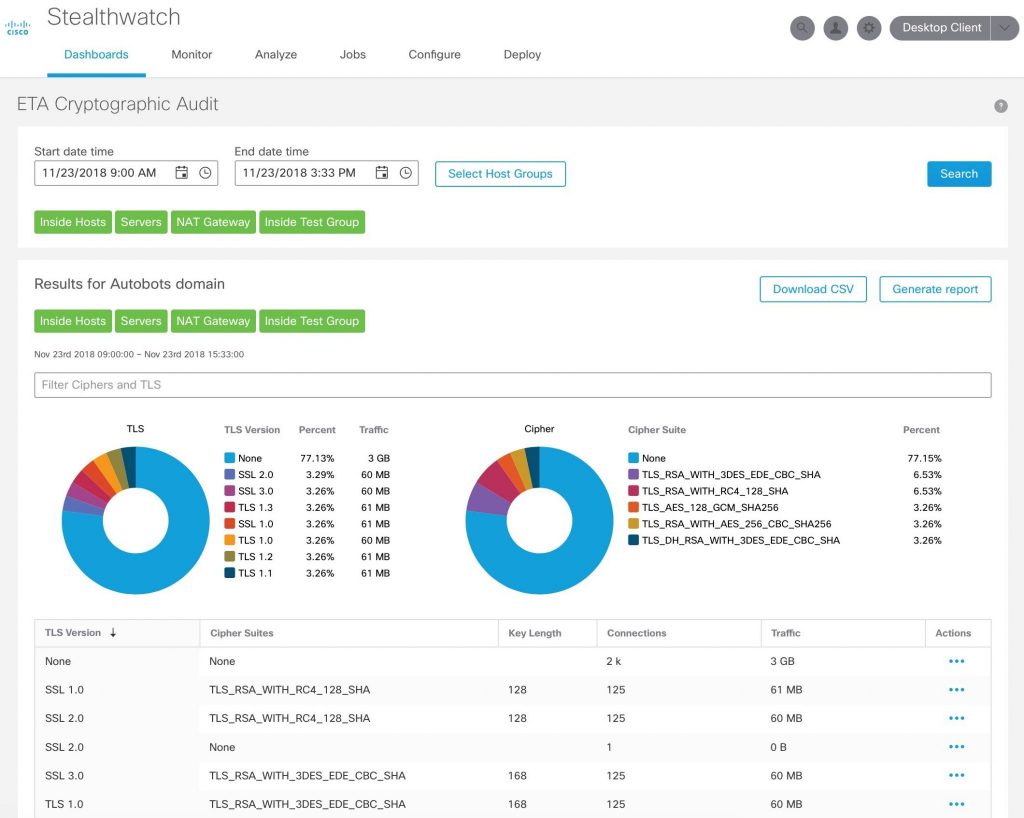
Basically, Stealthwatch monitors the activity of all the devices on your network. It creates a baseline that it considers to be normal behavior. Then it can detect when traffic events differ from that baseline. It also offers a single view of those threats across all of your environments, including private networks and public clouds like Microsoft Azure, Amazon Web Services, and Google Public Cloud.
Additionally, Stealthwatch is extending visibility, threat protection, and compliance verification to work with Microsoft Azure, without the need for additional agents or sensor deployments for your cloud environment. So now, the tool works with three of the major cloud environments (Microsoft Azure, Amazon Web Services, and Google Cloud Platform) natively. So you don’t need agents for any of those platforms and can instead deploy the product and start monitoring threats within minutes.
How it works
Stealthwatch uses a combination of predictive security analytics, behavior modeling, machine learning, and global threat intelligence to detect malware. They have about 100 security behavior modeling heuristics they use to analyze traffic behavior, like scanning, brute force logins, and suspect data hoarding or loss.
Featured image: Freerange Stock



