When an Active Directory domain controller is implemented, it creates necessary objects for in the Active Directory. The domain controller installation process creates DNS records in the DNS Server such as SRV records, host records, and an NTDS object that includes some important settings about the domain controller. The NTDS object is very critical. If an NTDS object for a domain controller is missing, the domain controller cannot participate in Active Directory replication.
The NTDS object for a domain controller is visible via the Active Directory Sites and Services snap-in. While you can open the Active Directory Sites and Services snap-in and verify to make sure all domain controllers have an NTDS object created, it is important to note that in a large Active Directory environment where there are hundreds of domain controllers, it might take a considerable amount of time to check the NTDS object for all domain controllers.
This article provides a PowerShell script that you can use to ensure all domain controllers have NTDS objects created. If a domain controller does not have the NTDS object created, that domain controller is considered an orphaned domain controller in Active Directory terminology.
Checking NTDS object via AD Sites and Services snap-in
To check NTDS objects for an Active Directory domain controller, open the Active Directory Sites and Services snap-in, and then expand a domain controller for which you want to check the NTDS object as shown in the red square of the screenshot.
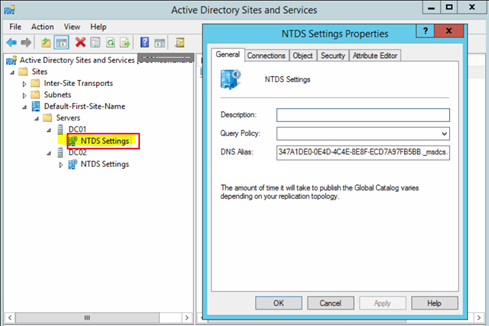
However, if you would like to check NTDS objects for all servers, you can use the PowerShell script below. The script generates a report that contains the domain controllers or servers that do not have an NTDS object created.
Requirements to run the PowerShell script
Please make sure to run the script from a Windows Server 2012 R2 member server or domain controller, and create a Temp folder on the C:\ drive, as the script generates a report by the name “OrpDCs.TXT” under the C:\Temp folder. Once you have met these requirements, copy the script in a PS1 file and execute it from an elevated PowerShell window.
What does the script do?
The script connects to the Active Directory Forest to which the local computer is joined, collects all server objects from the Active Directory, filters all the servers that are associated with the “nTDSDSA” class, checks to ensure the domain controller has the NTDS object and then generates a report in the C:\Temp folder.
Tip: Note that script does not perform any write operation in the Active Directory
$TestCSVFile = “C:\Temp\OrpDCs.TXT”
Remove-item $TestCSVFile -ErrorAction SilentlyContinue
$ThisString=”Domain Controller Name, Active Directory Forest, Final Status”
Add-Content “$TestCSVFile” $ThisString
$CurForestName = “TechGenix.com”
$TotNo=0
$TestStatus=””
$TestText=””
$SumVal=””
$Config = (Get-ADRootDSE).configurationNamingContext
$Servers = Get-ADObject -Filter {ObjectClass -eq “Server”} -SearchBase “CN=Sites,$Config” -SearchScope Subtree
foreach ($Server in $Servers)
{
$Ntdsa = Get-ADObject -Filter {ObjectClass -eq “nTDSDSA”} -SearchBase “$(($Server).DistinguishedName)” -SearchScope Subtree
if ($Ntdsa)
{
}
else
{
$ThisServer=$Server.DistinguishedName
$TotNo++
$Thisstr='”‘+$ThisServer+'”‘+”,”+$CurForestName+”,Not Ok – This Server does not have NTDS Object”
Add-Content “$TestCSVFile” $ThisStr
}
}
IF ($Error.count -eq 0)
{
}
else
{
$ErrorOrNot=”Yes”
}
IF ($ErrorOrNot -eq “Yes”)
{
$TestText = “Error.”
$SumVal = “”
$TestStatus=”Error executing AD Test.”
}
else
{
IF ($TotNo -eq 0)
{
$TestText = “No Domain Controllers Found that do not have an NTDS Object.”
$TestStatus=”Passed”
$SumVal=””
}
else
{
$SumVal = $TotNo
$TestStatus=”High”
$TestText = “A few Domain Controllers Missing NTDS Object”
}
}
$STR = $ADTestName +”,”+$TestStartTime+”,”+$TestStatus+”,”+$SumVal +”,”+$TestText
Tip: Note that the PowerShell script connects to the Active Directory forest to which the current machine is joined. When running the script, make sure to execute it from an elevated PowerShell command prompt. The currently logged-on user must have sufficient permissions to connect to the Active Directory forest.
Once you have finished executing the script, a report will be generated that contains all the Active Directory domain controller names and NTDS object status as shown in the report below:

As you can see in the report, the script collected all domain controllers from the current Active Directory Forest and checked the status of the NTDS objects for each domain controller in the Active Directory. The “Final Status” column indicates whether a domain controller has an NTDS object or not. As you can see “DC3.TechGenix.com”, “DC4.TechGenix.com”, and “DC6.TechGenix.com” do not have an NTDS object, so the script reported “Not Ok – This Server does not have NTDS object” message in the “Final Status” column. Once you have the report, you can check as to why a domain controller does not have the NTDS object.
This script is part of PowerShell-based Dynamic Packs that ship with the Active Directory Health Profiler, which you can use to perform a complete health check of an Active Directory forest. There are 99 health checks included in the AD Health Profiler.




I’m wondering if you can help me with this issue. Our problem started when we tried to DCPROMO a new hyper-vm host from Windows 2008R2 to Windows server 2016.
Our environment.
Windows 2008R2 running two domain controllers. Dominican-DC1 and Dominican-DC2. We are also running a Hybrid Exchange-2010. These are all physically servers.
Our plan was to move this to our new Hyper-V server. We created a Windows 2016 Hyper-V server with several VMs. The Hyper-V server is called Dom-HV01 (running Windows server2016) . We then created several VMs running Windows Server 2016,
• DOM-DC01 – Domain Controller
• DOM-DC-02 – Domain Controller
• DOM-Email – Hybrid Exchange
• D0M-Master – File/Printer
• DOM-Web. – Web server
Problem: We ran all of the prerequisite on Dominican-DC1, and proceeded to transfer and seize all roles to Dominican-DC2. We thought everything looked good until we tried to DCPROMO Dominincan-DC2 to our VM host called DOM-DC01. This is where the problem started . We were unable to DCPROMO from Windows 2008R2 to Windows Server 2016. We kept getting an error Object Not Found. We worked with the Microsoft AD engineers but they were unable to resolve the issue.
Now our dilemma:
We are now down to one DC. Dominican-DC02 is working (Windows Server 2008R2 with our Hybrid 2010 Exchange server). We are stuck moving forward to use our new servers. The users currently logon into to their PC’s using the WiNANS\username, for email their email addresses are either [email protected] or [email protected]. Some users in Office 365 and some are on-premise.
Best Approach?
Should we build a new domain? Should we build a new domain and call it WAPA.Academy and create a trust relationship with Dominican-DC2. Use the ADMT tool to transfer all users, computers, ssid etc…
Get the new Wapa.Academy up and running. Delete the problem domain (Dominican-DC2) and reverse the process. Re-create the Winans.spfs.k2.mi.us domain on the new server, run the ADMT tool and then delete the WAPA.Academy .
What we don’t know is, what the best way to handle the Hybrid Exchange 2010 server without loosing and the users mailbox, GUID etc…?
I really would like to avoid creating anoter Domain, if I can get this one working.
Any help you can provide would be helpful. Thanks
George (734)516-1003.