We’ve all heard horror stories about the applications that pose a significant threat to security. These applications might actively spy on your users. They may even parse your organization’s most sensitive data. You don’t want that to happen to your Microsoft 365 account! Even legitimate apps could also contain an unchecked security vulnerability. That’d allow an attacker to gain access to your organization’s resources. To counter this, many modern computing platforms don’t give free rein to any newly-installed app. The application must ask for permissions. Unfortunately, many users click OK without considering the consequences. That said, you can prevent users from granting permissions to the applications they install themselves by changing the consent settings!
I’ll show you how to prevent users from granting app permissions in Microsoft 365. I’ll also show you the different options you have.
Microsoft 365 Data Exposure
When a user installs an application, they don’t always expose the same data. It depends on the application’s permissions. Some applications might not expose any data at all. Others, though, could theoretically attempt to access all your data. That said, you can’t take risks and your only approach to data protection is pre-emption. That’s why it’s good practice to change your consent settings to avoid granting unwanted application permissions.
Here’s how you change use consent settings.
Configuring User Consent Settings
Before I begin, this article assumes that the user trying to grant permission is logged into Azure Active Directory and has a Microsoft 365 account. Azure Active Directory (Azure AD) is a core component of Microsoft 365 since it serves as a cloud-based counterpart to the Active Directory environment.
When a user installs an application, the installer will typically ask for various permissions. The requested permissions vary widely between applications. They may request access to the device’s hardware, like the camera or microphone. They may also require access to data. Not every application asks for data access, but many do. When a user grants data access, the application has access to sensitive Microsoft 365 data. That compromises the organization’s privacy.
To prevent users from granting access to apps, you need to tweak the user consent settings. You can access these settings through the Azure Active Directory Admin Center.
Follow these steps to find the user consent settings:
- Open the Azure Active Directory Admin Center, then select the Azure Active Directory tab.
- Click on the Enterprise Applications tab, shown in the figure below.
Azure Active Directory, I’m in. Where next? - Select the All Applications (Preview) tab to view all available applications.
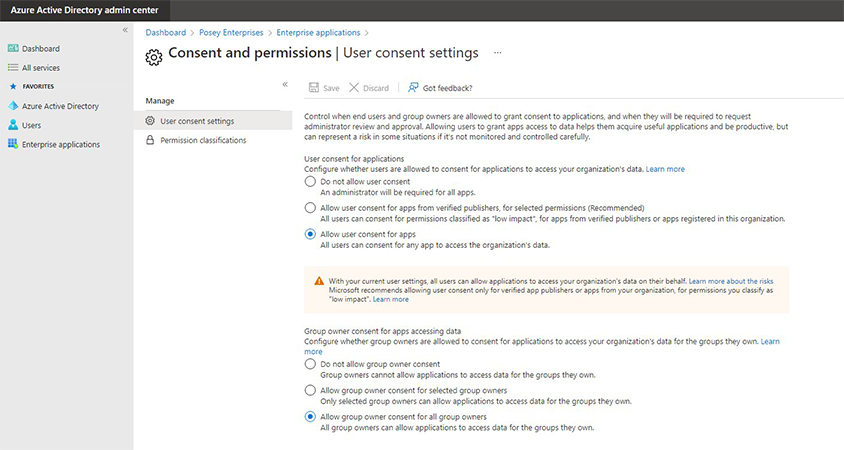
All these apps can see my data? - Click the Consent and Permissions tab. You’ll also see the User Consent Settings Screen.
At least I can decide what the users can do!
Explore the Tabs
Let’s talk a little about the tabs we went through. The Enterprise Applications tab is the location for managing applications. The apps on that tab will use the current Azure AD tenant as their identity provider.
The Consent and Permissions contains the user consent settings. It explains that you should monitor and control the users’ ability to give app permissions. Users can benefit greatly from this ability, but the admins should be aware of the risks that come with it.
That’s why Microsoft gives you different options for user consent. That’ll help you be sure your organization’s data is as safe as possible. Let’s take a look at these settings.
User Settings
Before I discuss the existing settings, it’s worth noting that settings come in 2 different categories: User Settings and Group Settings. We’ll discuss Group Settings later. For now, let’s see what are the 3 User Consent Settings:
1. Do Not Allow Consent
This option prevents users from granting app permissions. They need administrator approval.
2. Grant Consent for Approved Publishers
This setting allows users to grant consent to apps from verified publishers. The permissions are usually low-impact (per Microsoft’s standards). The condition is that the app’s publisher has been verified. Otherwise, the app has to be registered with the organization.
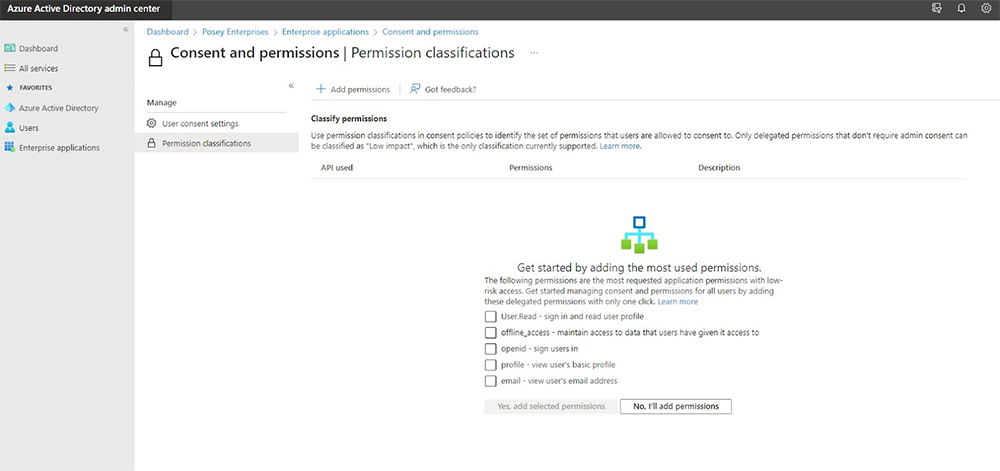
It’s up to the administrator to define which permissions are low-impact. If you look back at the previous figure, you’ll notice a Permission Classification tab. This tab lists what Microsoft considers as low-impact permissions. You still need to select the permissions and add them yourself.
3. Allow Consent
This option allows users to grant permissions to apps as needed. This setting is the most convenient for the users. That said, it poses the greatest risk. That’s why this option is generally not recommended.
Group Settings
The settings for group owners are similar to the user consent settings. That said, the two aren’t identical. Here are the 3 group settings for app permissions:
1. Do Not Allow Permissions to Be Granted
This setting doesn’t allow group owners to grant any permissions. While this setting is quite secure, some may find it impractical.
2. Allow Approved Group Owners to Grant Permissions
This setting will only allow select group owners to grant permissions to applications. The administrator has to add these individuals to an allowlist.
3. Allow Permissions to Be Granted
This setting gives group owner consent for all group owners. This setting tells Azure AD that all group owners can grant permissions to applications.
The Bottom Line
Azure AD provides many settings for Admins. These help limit, or even block, a user’s ability to grant app permissions. That also applies to group owners. That helps protect an organization’s Microsoft 365 data.
Ultimately, administrators need to find a balance. While it’s good for users to install and allow applications, the admin needs to realize the risks associated with that freedom. It’s usually best to require administrative approval for application permissions. It’s also good to give users the ability to grant only low-impact permissions to applications.
FAQs
Why are Consent Settings divided into two, nearly identical, groups?
Group owners are often managers. While you might not want users to allow apps to access your data, a manager may need to grant such permissions.
What are the default low-impact permissions?
By default, Microsoft doesn’t enable any low-impact permissions. That said, it provides a list of what it considers to be low-impact permissions. These permissions allow an application to read a user’s profile, have offline access, allow user sign in, view basic profile information, and view the user’s email address.
What permissions do applications commonly ask for?
It depends on the application. Still, it’s relatively common for an application to ask for read/write access to Microsoft 365 data.
What are the risks of allowing user-installed applications to access data?
A company’s privacy is at risk if applications can access their Microsoft 365 data. That’s especially problematic for organizations in regulated industries. A malicious application could use its access to delete, encrypt, or expose corporate data.
Would applications have any legitimate reason to need access to Microsoft 365 data?
Yes, they may. A mail client needs access to send files as attachments. Grammar checking tools also can’t analyze Word documents without access.
Resources
Microsoft Guidelines
- Learn Microsoft’s guidelines for managing user consent settings here.
- Learn how to configure permission classifications here.
- Read more about permissions and consent in the Microsoft identity platform here.
- Learn how to plan Azure Active Directory My Apps configuration here.
- Take a deep dive into the Microsoft permissions and consent framework here.
- Learn about Azure AD administrative units here
- Read more about Azure AD application security here
- Learn how Microsoft 365 subscribers can utilize Azure AD here



