Application security has become one of the key concerns of application developers. “Shift left” — starting to care about security as early in the development cycle as possible — is obviously the best way to marry security and developer agility. Software vendors agree and compete on enabling this approach. In this article, Dmitry Sotnikov, chief product officer at 42Crunch, shows how GitHub and its partners enable that scenario with the recent launch of GitHub code scanning and its marketplace.
What is GitHub code scanning
Doing security analysis on source code right when it gets committed seems like a natural way to do source code repositories. GitHub is by far the most popular source control system with hundreds of millions of repositories hosted.
In September 2019, GitHub acquired Semmle with the idea of incorporating their static code analysis technology into the platform. A year later, the technology got fully integrated into GitHub, made compatible with GitHub Actions (GitHub continuous integration / continuous delivery mechanism) and GitHub marketplace, and launched as GitHub code scanning.
Code scanning is free for public repositories and is a GitHub Advanced Security feature for GitHub Enterprise.
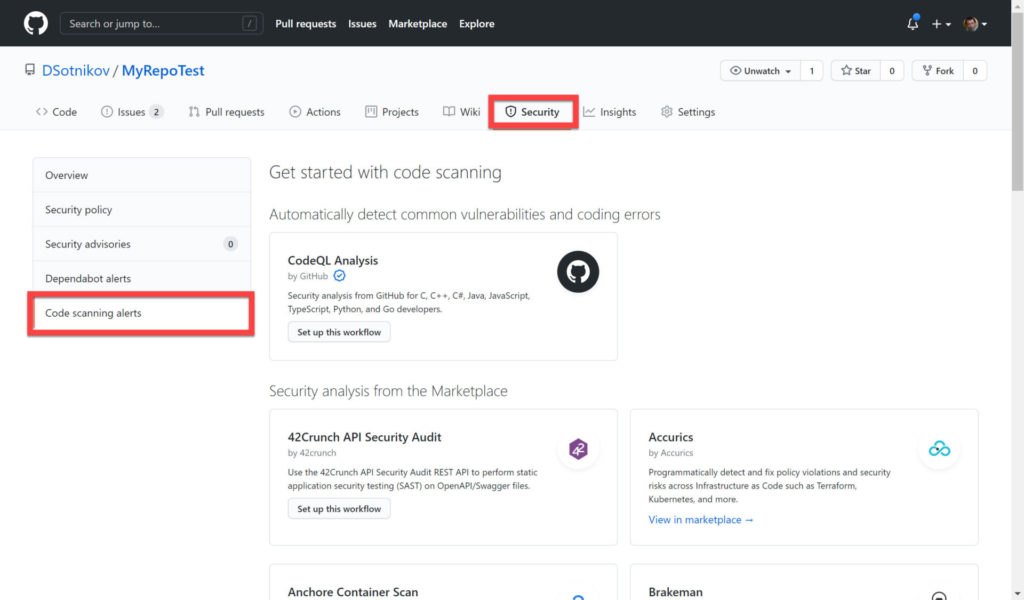
To enable it, simply go to the Security tab of your code repository and GitHub code scanning alerts there:
You can see the variety of options on this page. CodeQL Analysis is the module for C, C++, C#, Java, JavaScript, TypeScript, and Go that came to GitHub through the Semmle acquisition. The other modules (42Crunch, Anchore, and so on) are coming from GitHub partners.
Alerts, workflows, actions
To enable code scanning, you basically need to:
- Select which checks you want to run.
- Set up workflows that will run these checks.
- Fine-tune conditions and other parameters.
As you can see from the screenshot above, setting up GitHub code scanning takes more than just selecting a checkbox. Instead, you need to click the Set Up This Workflow buttons on the modules of your choice (where vendors made these initial workflows available, for others, you need to follow the View In Marketplace links and read the instructions there.)
Workflows are GitHub Actions scenarios that are described in YAML format and can be run by GitHub based on certain events. These represent GitHub’s automation and continuous integration / continuous delivery (CI/CD) process at GitHub.
You can have multiple workflows set up in your repository and have them used on different events: on code changes in the repository, on pull request reviews, and so on.
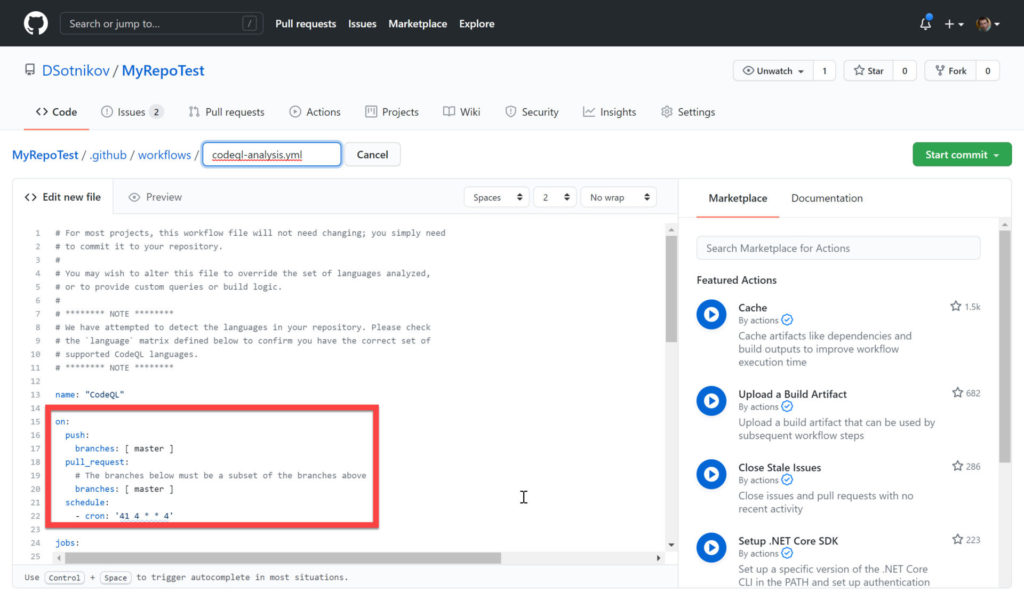
Click the Set Up This Workflow button on the CodeQL module, and you will see the suggested workflow script that you can fine-tune and save (by clicking the Start Commit button at the top right):
As you can see, by default, this workflow will run:
- On code pushes to the master branch.
- On pull requests to the master branch.
- On schedule, every Thursday at 04:41 UTC.
You can add, delete, or modify these conditions as you see fit.
Partner extensions
GitHub and Microsoft are extremely partner-focused and realize that they cannot provide full technology coverage on their own. This is why GitHub code scanning has been launched with key partner components in there from day 1.
There are two ways you can use these extensions.
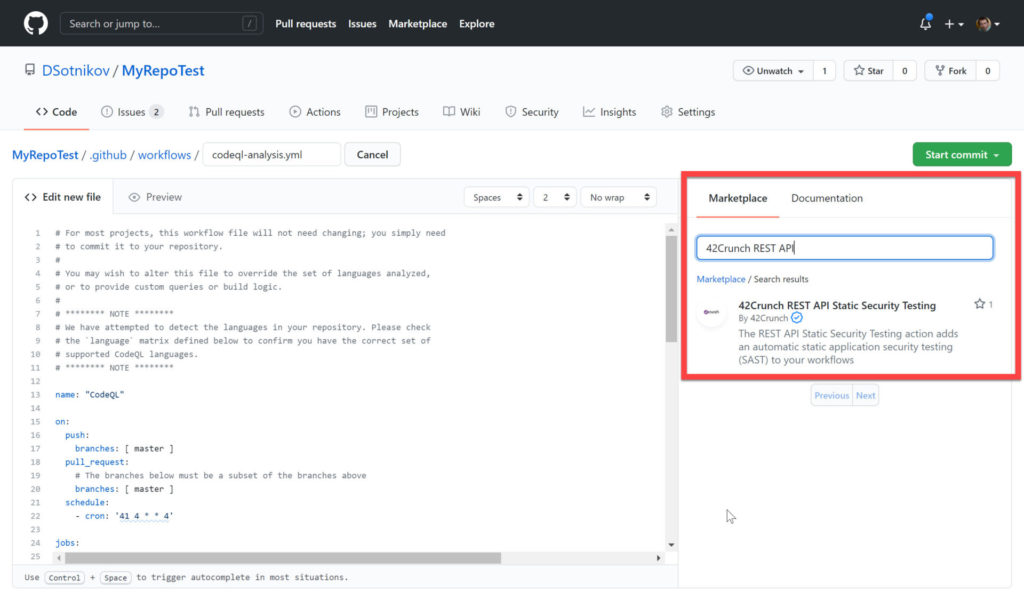
By adding them to existing workflows — using the search panel on your right-hand side when editing a workflow:
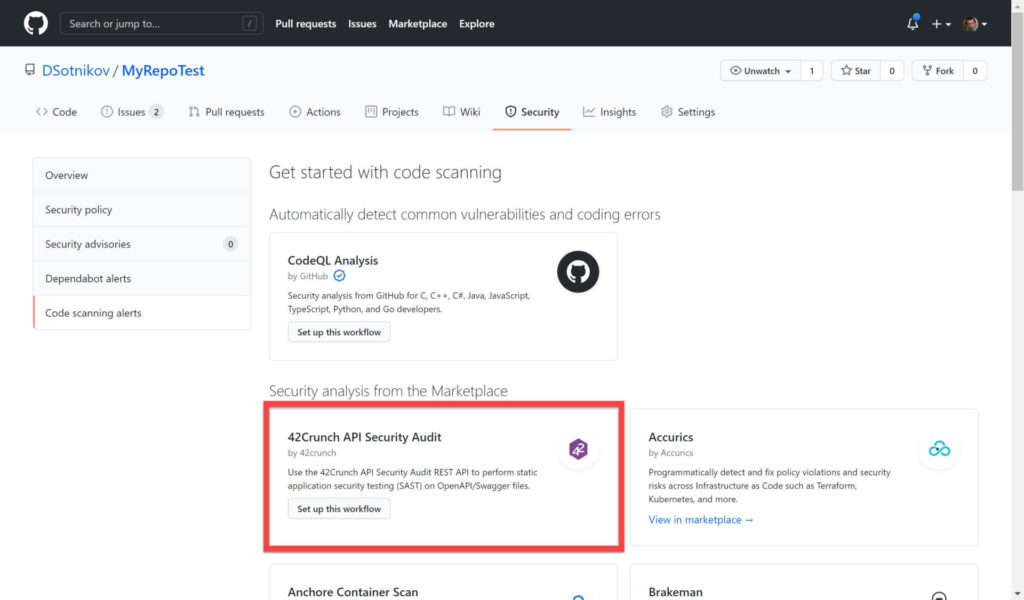
Or by creating standalone workflows from the main GitHub code scanning screen:
In the first case, the actions will all be run within the same workflow under the same trigger conditions. In the second one, they will run independently.
Note that in most cases partner extensions will require you to create an account with the corresponding GitHub partner and to set the corresponding partner API key in GitHub secrets to enable the integration. Partner extensions will have the corresponding instructions in the comments of their action — so read these carefully.
For example, if you want to add security analysis of the REST APIs in your repository, you will need to follow these instructions linked from the 42Crunch API Security Audit extension. For more information, also see this article.
Running code scans
Next time your trigger conditions happen, the workflows will run. You can see the status and logs of these executions on the Actions tab of your repository.
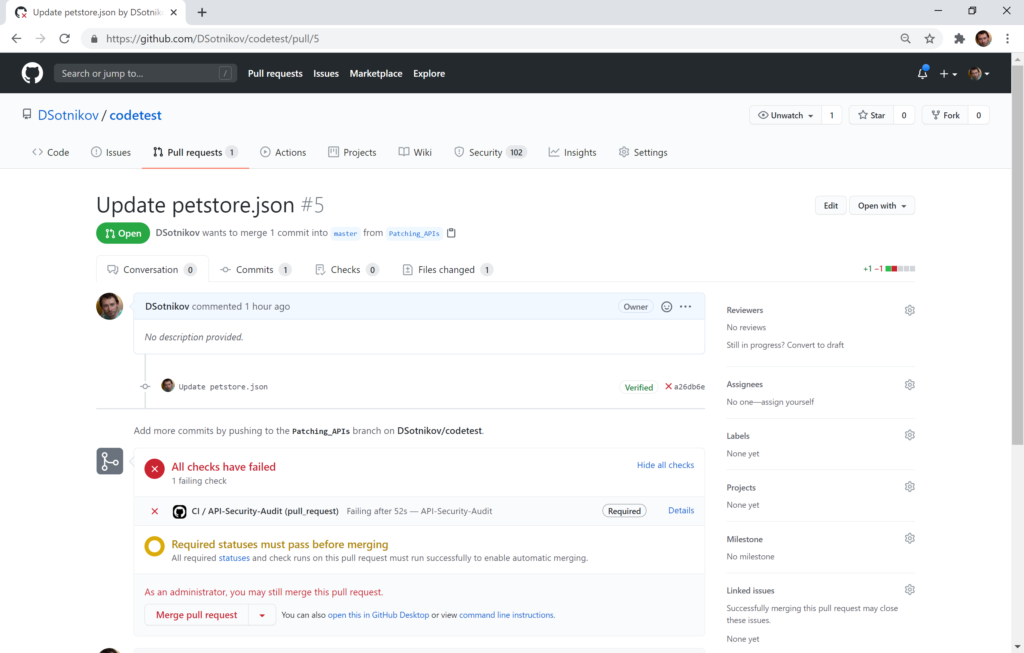
If you add the workflows to your pull request reviews, you will also get them right on the pull request screen:
Reviewing the alerts
Once the workflows run, you will see a number added right on the Security tab of the repository showing you the number of alerts that the code scan generated.
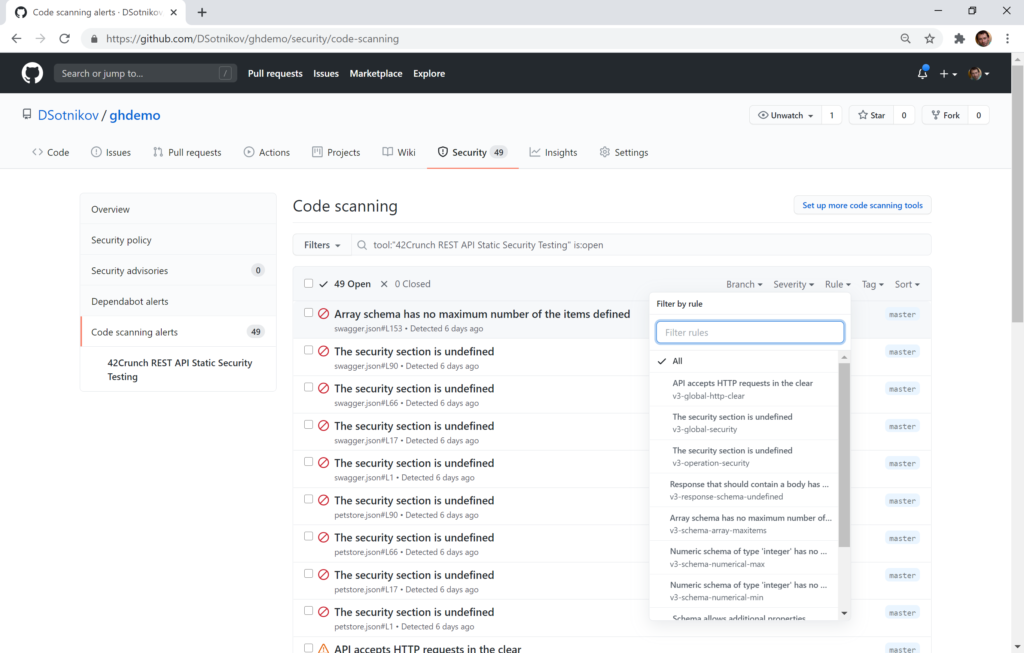
You can go to the Security / Code scanning Alerts tab to see the list of alerts. The list can be sorted and filtered by file, branch, severity, rule, tags:
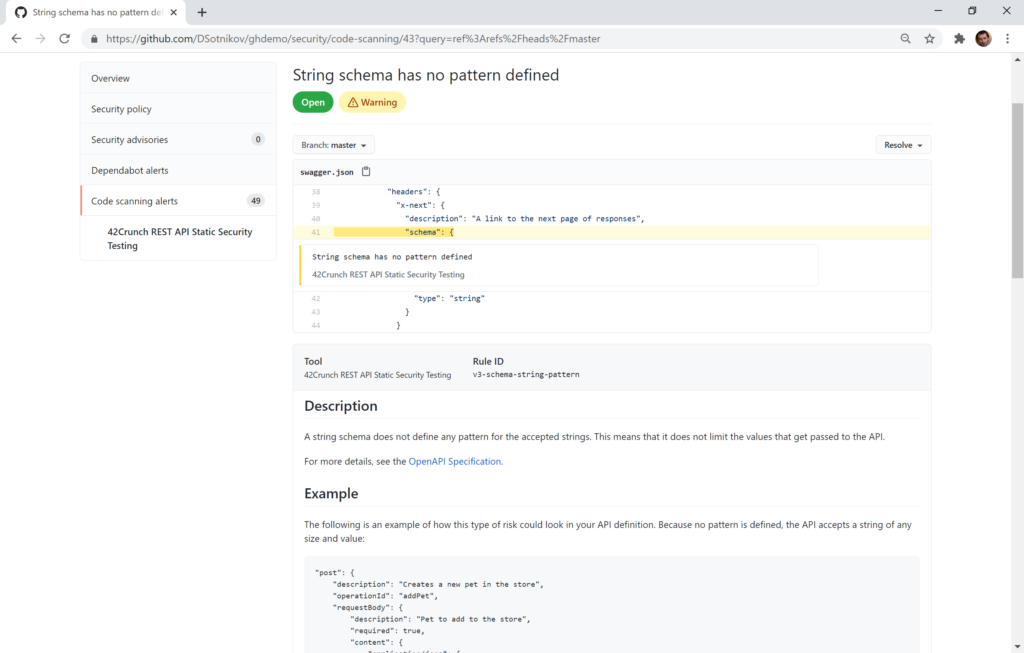
You can then click any of the alerts and see the exact place in your source file that has the issue. If you expand the details you will also get the corresponding knowledgebase article with details description and fix recommendations:
GitHub code scanning: A powerful platform
GitHub code scanning and partner extensions provide comprehensive security static code analysis right within your code repository. This powerful platform helps companies make sure that no insecure code ever gets introduced into their systems and deployed to production.
Featured image: Shutterstock