A malware that has been on InfoSec experts’ radars for some time is Shamoon. A malware that has primarily attacked entities in the Gulf nations, Shamoon is vicious as it destroys hard drives through master boot record (MBR) and data wiping. Well-known attacks involving Shamoon have occurred since 2012 and as recently as January 2017. While the mechanics of the malware itself and how it attacks a system have been discovered, the actual entry point has still been a mystery.
At least this was the case until recently, when IBM’s X-Force Incident Response and Intelligence Services (IRIS) team released a report detailing their research. In this report, the IBM team details how the infection by Shamoon is caused by “a document containing a malicious macro that, when approved to execute, enabled C2 communications to the attacker’s server and remote shell via PowerShell.”
The macro in question is usually sent via email, namely a spear phishing email. The reason why this rather obvious entry point was not discovered earlier has to do with how threat actors deployed Shamoon. What I mean by this is that instead of infecting a machine right away, the hackers would do heavy reconnaissance of the machine before sending Shamoon into the hard drive. The graphic from IBM’s report explains the entire process, as seen below:
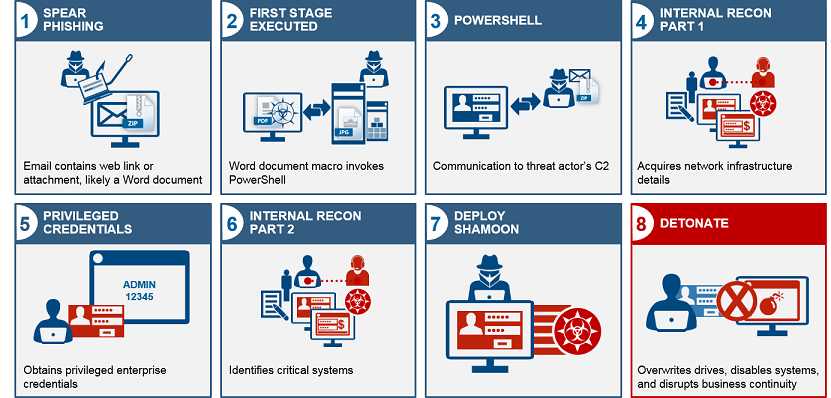
This attack tends to run counter to normal methods of infection. Take ransomware, for example. The second that a malicious .exe is opened, the malware proceeds to attack files or the hard drive itself. In this case, the threat actors do a great deal of recon post-infection before deploying the highly destructive malware. IBM was able to reach this conclusion after studying the vast number of cases where Shamoon was deployed since 2012. Only then was the connection between the initial macro and the much later Shamoon infection made.
Now that the entry point has been identified, what should cybersecurity experts do to prevent a Shamoon infection? Besides the obvious, namely educating employees on spear-phishing identification, IBM researchers point to their findings as a pathway for defensive measures. In an interview with SC Media, Kevin Albano, global lead of threat intelligence at IBM X-Force IRIS, said by discovering the techniques that the hackers use will help organizations “determine if they’ve been impacted, which was impossible before, because the indicators weren’t public until now.”
While the Shamoon attacks have been isolated to Gulf nation-states, we all know that malware spreads quickly (especially via the Dark Web). Stay vigilant no matter what region of the world you conduct cybersecurity in.
Photo credit: Wikimedia



