An Introductory Guide to WireGuard
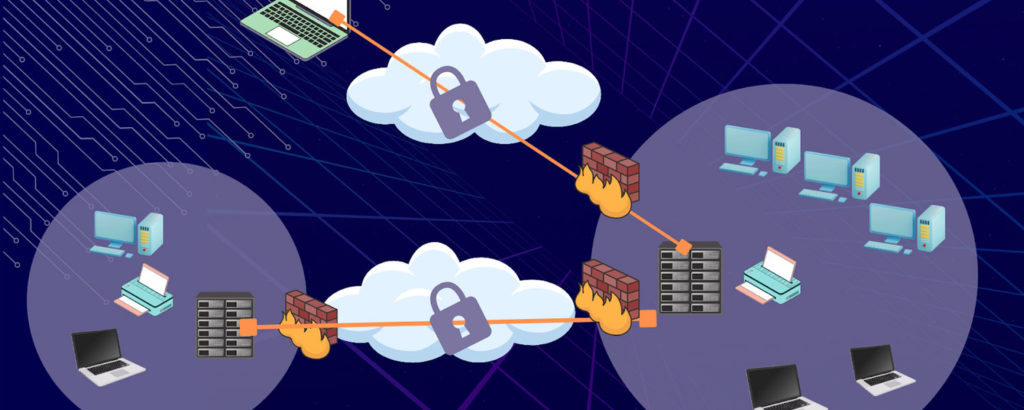
More and more employers are embracing remote work, which has increased the need for virtual private network (VPN) solutions. In this post, you’ll learn about WireGuard VPN, the fastest VPN protocol on the planet. You’ll discover how it works, its benefits, its disadvantages, how it compares with OpenVPN, and more.