Numerous federal agencies have recently been engaging in bug-bounty programs. Often, these events were facilitated by San Francisco-based company HackerOne, which is backed by major tech players Microsoft, Google, and Facebook. Putting aside the irony of major antiprivacy figureheads in the corporate and government spheres working in tandem against hacking, these events have resulted in numerous security advances.
The U.S. Army recently discovered this for themselves as they completed their own bug-bounty program on January 19. As reported in a blog post by HackerOne, the “Hack the Army” program was intended to reinforce the security of key mission-oriented systems, and also build a bridge between the hacking community and the military.
In terms of the first goal, there were 416 bug reports, and of those 416 reports, 118 were deemed “unique and actionable.” Below is a graphic summarizing the key events that transpired during the bug bounty:
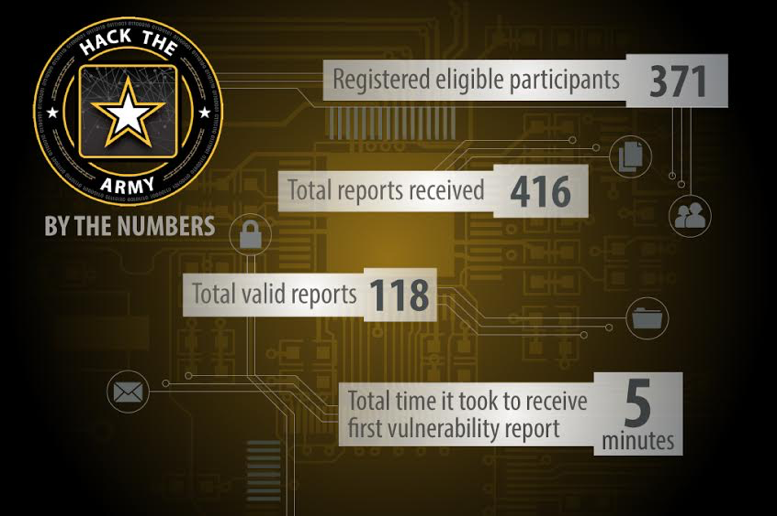
One of the most significant vulnerabilities allowed a hacker to go from the publicly accessible website goarmy.com to an internal Department of Defense website “that requires special credentials to access.” How this vulnerability had not been exploited is a stroke of luck for the Army as these are the types of issues that create massive security breaches.
The bug-bounty participants were paid upwards of $100,000 total (this number may change). The vast majority of the 371 participants to be compensated were from the private sector, but it should be noted that 25 government employees (17 of those in the military) were a part of Hack the Army as well.
It would appear that the second major goal of connecting white hat hackers and the feds was achieved (at least in terms of the numbers provided above). Does this mean that hackers and the military are about to hold hands and skip down the Pentagon’s hallways together? Highly unlikely. As I have reported numerous times, many hackers hold a decentralized view of authority, more or less a “no gods, no masters” mentality.
Working en masse with any government, especially the United States, is considered a poisonous idea to many hackers. This is a government that has harshly prosecuted gray hats for disclosing vulnerabilities to companies for no monetary gain, created trumped up charges against hacking legends like Kevin Mitnick that resulted in him wrongly being placed in solitary confinement, and to this day seeks out hacktivists and whistleblowers with a psychotic vengeance.
Until the government changes the way it treats hackers, namely white and gray hats, we can expect these bug-bounty programs to have only a fraction of its potential participants. Hackers as a whole do not trust the government. Can you blame them?
Photo credit: U.S. Army



