
SOURCE: Computer Assistance
Microsoft has long used a shared responsibility model for its various cloud services, including Microsoft 365. The model states that Microsoft is responsible only for securing its cloud infrastructure. This means users are responsible for securing their data. But the problem is Microsoft 365 isn’t secure by default. So how do you get around this issue and improve Microsoft 365 security?
Microsoft 365 deployments have several built-in security mechanisms. You’ll need to take advantage of these mechanisms to get around this issue. Although many security settings are available, some are more important than others. In this article, I’ll discuss 4 key areas to focus your efforts on if you’re just starting with Microsoft 365 security.
4 Key Areas to Focus On for Better Microsoft 365 Security
Forgetting to batten down the hatches on your Microsoft 365 security solution will inevitably lead your business to land on the rocks. So, you must focus on these 4 Microsoft 365 security areas to keep you sailing smoothly.
1. Secure Score
When it comes to Microsoft 365 security, the very first thing you should look at is your company’s secure score. A higher score indicates you have good security practices that provide effective protection. Conversely, a lower score shows that your business is more vulnerable to cyberattacks.
That said, the score is relative. It’s not an absolute score calculated from the security practices in your company. It gives you a benchmark to work from when improving the security of your system. Without a benchmark, you’ll find it difficult to determine if you’ve improved your system’s security and how much impact your changes have made.
You can access your Secure Score by following these steps:
- Open the Microsoft 365 Defender console
- Click on the Secure Score tab
You can see what the secure score looks like in the figure below.
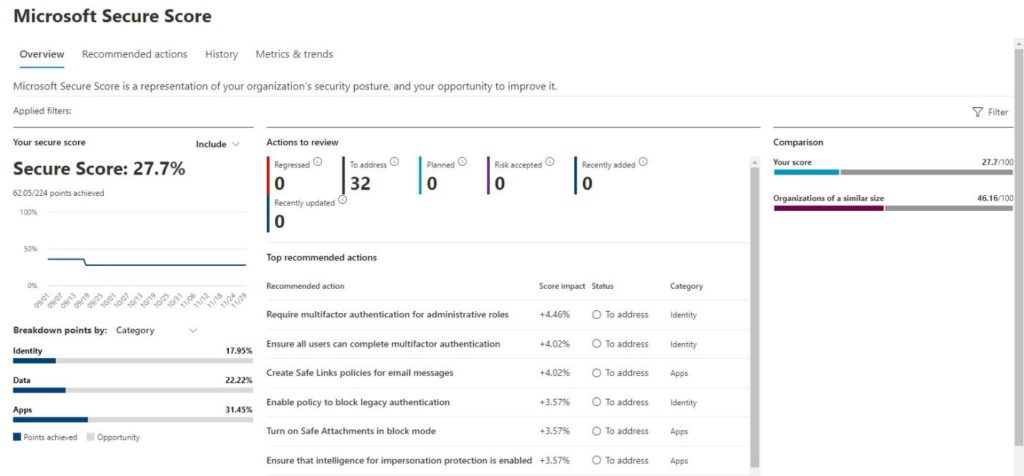
To increase your security score, look to the lower right of the security score screen for change recommendations and how much they’ll impact the score. It can take up to 24 hours for the score to update. Ideally, I recommend you aim for a security score above 80%.
Pro Tip
Clicking the Recommended Actions tab at the top of the screen takes you to a page where Microsoft has broken down each action in more detail. That said, you’re not expected to perform every recommended action. Some actions require a subscription, like Azure Premium. Other actions may not incur an additional cost but might not be appropriate for your company.
2. Multi-Factor Authentication
When it comes to hardening Microsoft 365, one of the most important things you can do is to enable multi-factor authentication (MFA). According to Microsoft, “MFA can block over 99.9% of account compromise attacks”. While some claim this figure is overly optimistic, most IT pros agree that using MFA improves overall security.
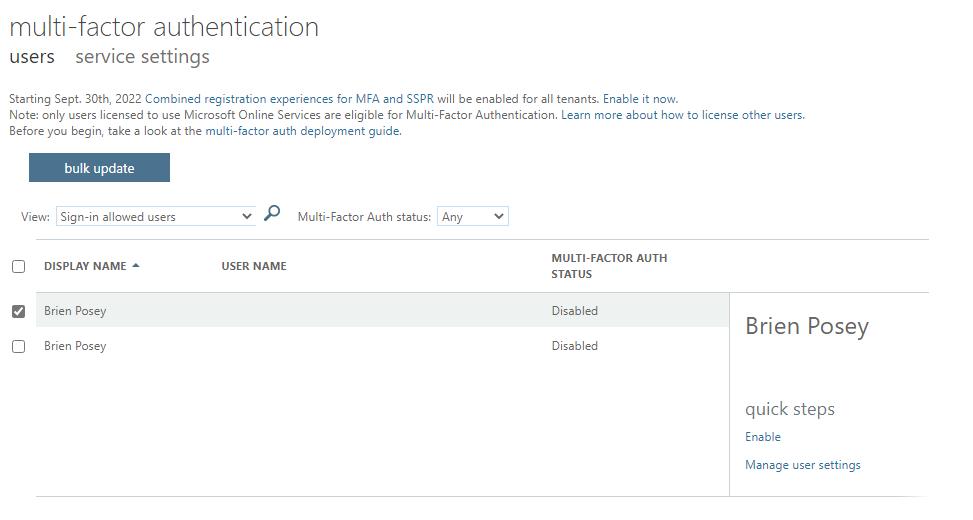
Microsoft makes it easy to enable MFA. Before doing so, it’s important to disable any legacy MFA options you might have used in the past. To enable MFA, follow these steps:
- Open the Microsoft 365 Admin Center
- Click on Settings
- Click on Org Settings
- Select the Services tab at the top of the screen
- Click on Modern Authentication (Don’t click on Multi-factor Authentication)
- Ensure that Modern Authentication is enabled
- Click Save
- Click on Multi-factor Authentication
- Select Configure Multi-factor Authentication
- Select the users for whom you want to enable MFA
- Click Enable
3. Password Expiration Policy
Another way to shore up your Microsoft 365 security is to ensure your company has a password expiration policy. This policy controls the frequency with which your passwords expire and must be changed. To review and configure the password expiration policy, follow these steps:
- Open the Microsoft 365 Admin Center
- Click on Settings
- Click on Org Settings
- Select the Security and Privacy tab at the top of the screen
- Locate the Password Expiration Policy and Self Service Password Reset options available on this screen, as shown below
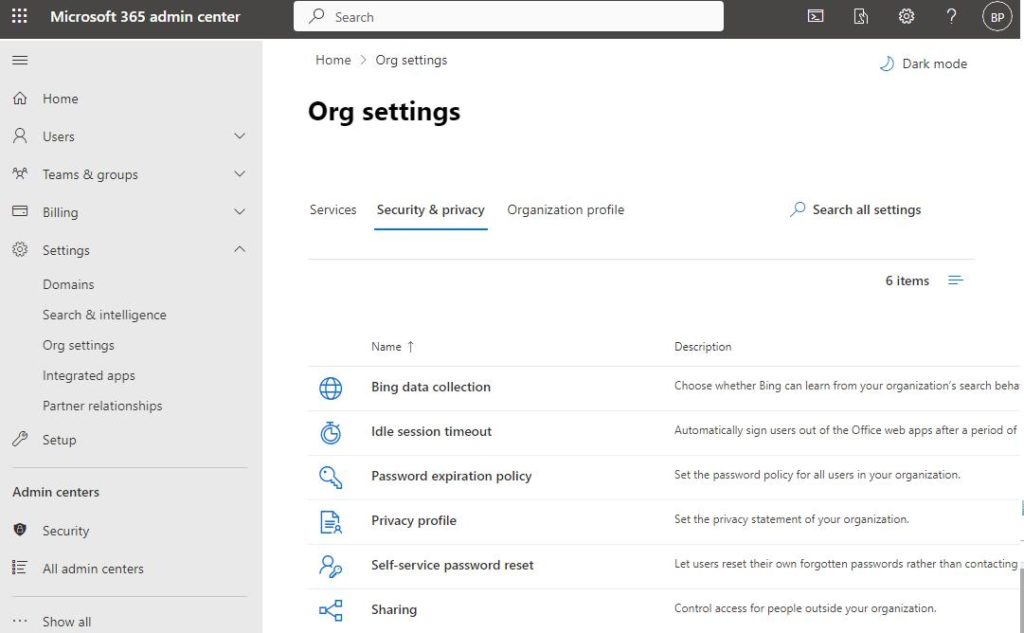
By default, Microsoft sets passwords to never expire, which is Microsoft’s recommended configuration. If you want passwords to expire periodically, follow these steps:
- Click on Password Expiration Policy
- Deselect the Set Passwords to Never Expire checkbox
- Enter your preferred password expiration period
- Click Save
4. Sign-in Monitoring
One more thing you can do to improve your Microsoft 365 security is to monitor recent sign-ins. The idea is to regularly search the logs for anything abnormal that might signal a breach in your system. Some excellent third-party tools can also help you to monitor your Microsoft 365 logs. Examples of these tools are GFI’s KerioControl, CrowdStrike Falcon LogScale, and SolarWinds Server Log Management and Analysis. That said, you can access your company’s sign-in logs without supplementary software.
To review your sign-in logs, follow these steps:
- Open the Azure Active Directory Admin Center
- Click on the Azure Active Directory container
- Locate the Monitoring section and then click on Sign-in Logs
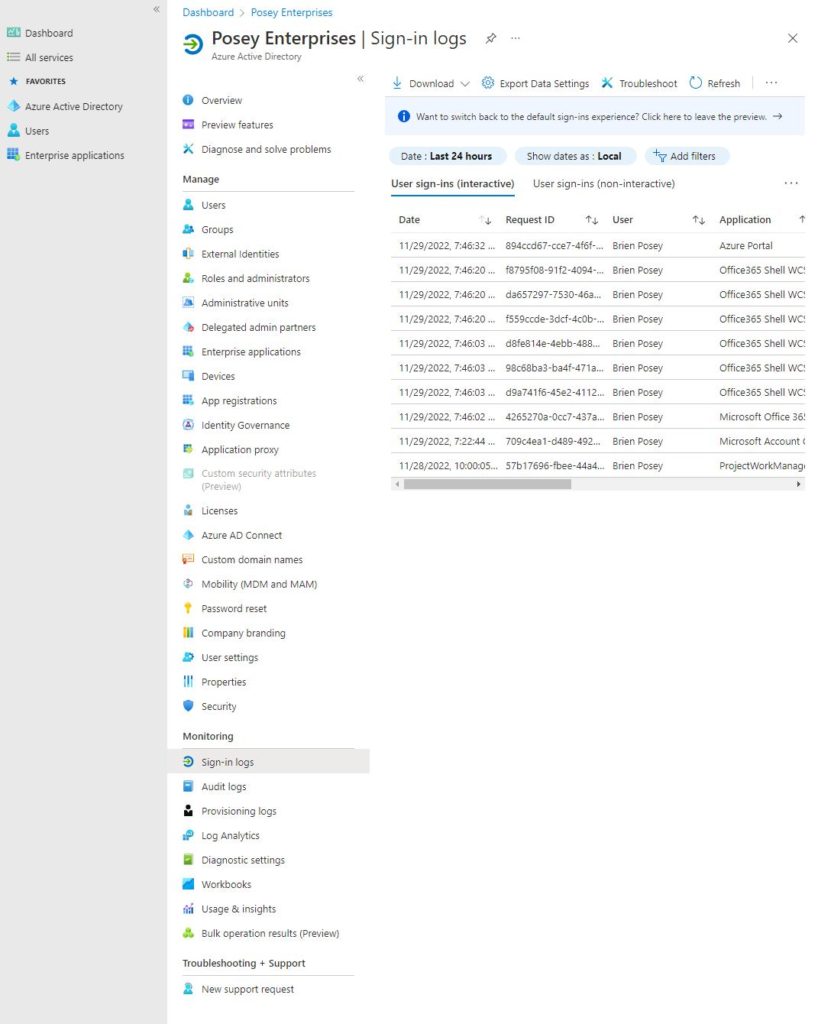
Pay attention to these two things shown in the pictures above:
First, sign-ins are organized as interactive or non-interactive. Interactive sign-ins are those in which a user had to enter a set of credentials. Meanwhile, non-interactive sign-ins have to do with automated processes.
The other thing to pay attention to is that by default, the console only shows logins that have occurred in the last 24 hours. You can change the filter, though, by clicking on Last 24 Hours. You can then configure the console to show you logins over a different duration of time.
Final Thoughts
The door to better Microsoft 365 security begins with 4 key areas. First, check your Microsoft 365 secure score and security recommendations to improve your network security. Implement as many recommendations as possible. And, if necessary, prioritize by determining how much the activity will improve your secure score.
You should also implement multi-factor authentication to reduce the risk of bad actors accessing your system. MFA does this by using one or more verification processes to assess if the user accessing the system is who they say they are.
In addition, implement a password expiration policy to ensure bad actors can’t use old passwords to access your network.
Finally, use a sign-in logging solution that helps audit who is accessing what parts of your system and when. Most solutions also come with security tools that flag abnormal network usage to administrators for immediate attention based on a pre-established baseline.
Have more questions? Check out the FAQ and Resources sections below.
FAQ
What percentage of attacks can MFA realistically prevent?
MFA only guards against an attacker logging in using stolen credentials. When it comes to the percentage of stolen credential attacks that MFA prevents, it’s difficult to get an accurate number. In my experience, MFA can stop approximately 70% to 80% of stolen credential attacks. This number is trending downward, though.
Why can’t MFA stop all stolen credential attacks?
A big part of the reason why MFA sometimes fails to prevent stolen credential attacks has to do with smartphone theft. If a criminal has physical possession of a user’s smartphone, an MFA prompt asking a user to enter a number that has been texted to their smartphone will be ineffective. That’s because the criminal will receive the MFA code.
Do attackers have other ways to circumvent MFA?
A cybercriminal can beat an MFA prompt in several ways. One option is to use a SIM swapping attack, which causes a copy of the MFA code to be sent to the attacker’s phone. Another attack involves setting up a phishing site that relays credentials and MFA codes between the user and the real site. Since the attacker controls this phishing site, they’re privy to any information that is relayed through it.
Is it possible to export the Azure Active Directory sign-in logs?
Yes, you can export the sign-in log data. To do so, just click on the download link and choose your preferred format. You can download the logs as a JSON or CSV file.
What is the elf-Service Password Reset option shown on the Microsoft 365 Admin Center’s Org Settings screen?
The Self-Service Password Reset feature allows users to reset their passwords without calling the helpdesk. To enable this feature, you’ll need an Azure Premium P1 license. Users will also have to register their contact information before they can use the feature.
Resources
TechGenix: Article on Multi-factor Authentication MFA
Learn why you need MFA for Microsoft 365 for your business.
TechGenix: Article on Azure Premium MFA Changes
Read more on how MFA changes when enabling Azure premium features.
TechGenix: Article on Secure Score
Find out how to use Microsoft 365 Secure Score.
Microsoft: Article on Password Policy Recommendations
Discover how Microsoft’s password policy recommendations improve your businesses security.
Microsoft: Article on Self-Service Password Reset Policy
Read about self-service password reset policies.



