
According to Microsoft, Multi-Factor Authentication (MFA) can prevent 99.9% of account attacks. This might sound enticing to some of you. However, you must strive to maintain a balance between security and usability. Occasionally, the MFA can behave so aggressively that you keep getting bombarded with the constant MFA prompts. Fortunately, you have a way to limit these prompts if you work from a trusted device.
In this article, I’ll explain how you can use Azure Active Directory’s (Azure AD) “Remember MFA” feature to adjust your authentication. I’ll show you how to enable it, and how to disable the “Keep Me Signed In” feature in Azure AD.
Let’s begin with a brief overview of device trust.
The “Remember MFA” Feature
In the context of Azure AD, device trust can have many different meanings. In the context of this article, device trust is when you acknowledge that you regularly work from a particular device, and therefore trust that device. It doesn’t refer to Azure AD device registration.
Using MFA is essential, but there’s no reason for you to constantly get pestered with many prompts if you’re working from your device. “Remember MFA” allows you to defer authentication prompts on devices that you trust. That way, admins in your organization can ask users to use MFA periodically to validate their identities without doing so excessively.
Let’s now go over how to enable MFA.
How to Enable the “Remember MFA” Feature
When enabled, the “Remember MFA” feature tracks the last time you proved your identity through multi-factor authentication. If you use a browser-based application, a persistent cookie allows you to remain authenticated until it expires.
If you work from non-browser applications, the hourly refresh token validation process checks to see whether it requires multi-factor authentication.
It’s a relatively simple process to enable the “Remember MFA” feature. To do so, follow these steps:
- Log in to Azure AD
- Open the Azure Active Directory Admin Center
- Click the Users container
- Click the Per-user MFA button at the top right of the image
- When the Multi-Factor Authentication window appears, click on “service settings” near the top of the page
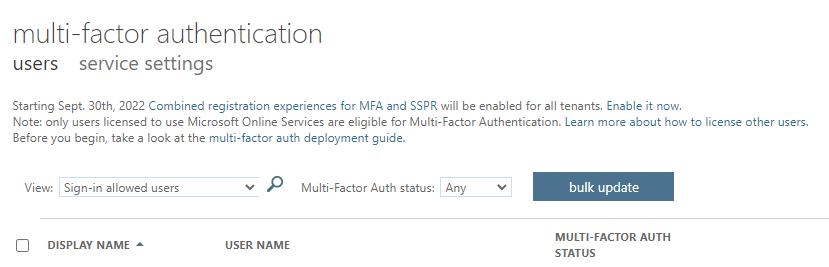
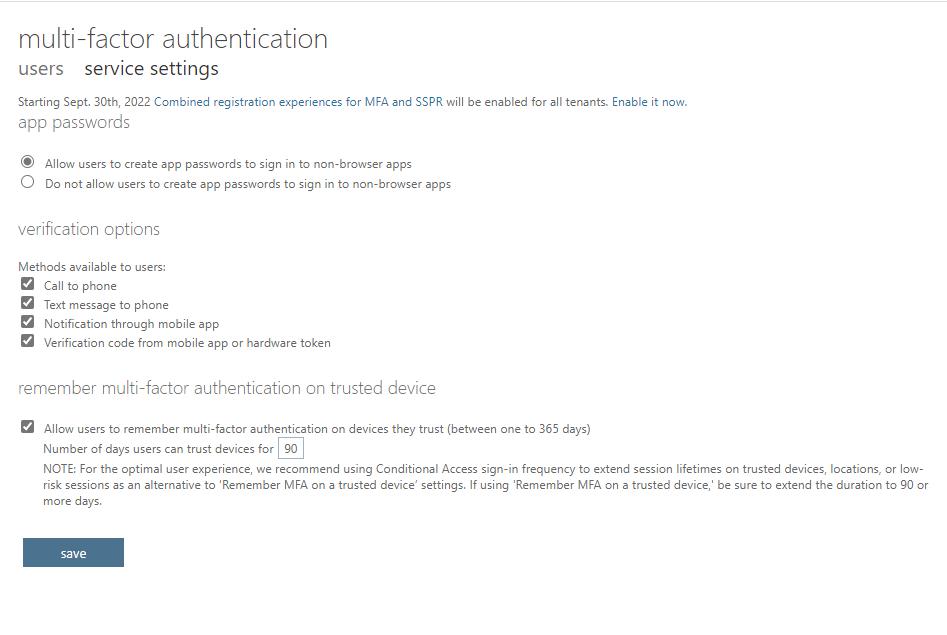
- Select the “Allow users to remember Multi-Factor Authentication on devices they trust” checkbox
- Specify the number of days to trust these devices
I’ll now show you how to disable the “Keep Me Signed In” feature in Azure AD.
How to Disable the “Keep Me Signed In” Feature
Now you’ll need to disable the Azure AD “Keep Me Signed In” feature. This feature isn’t compatible with the “Remember MFA” feature, so you have to turn it OFF. To do so:
- Log in to the Azure AD Admin Center
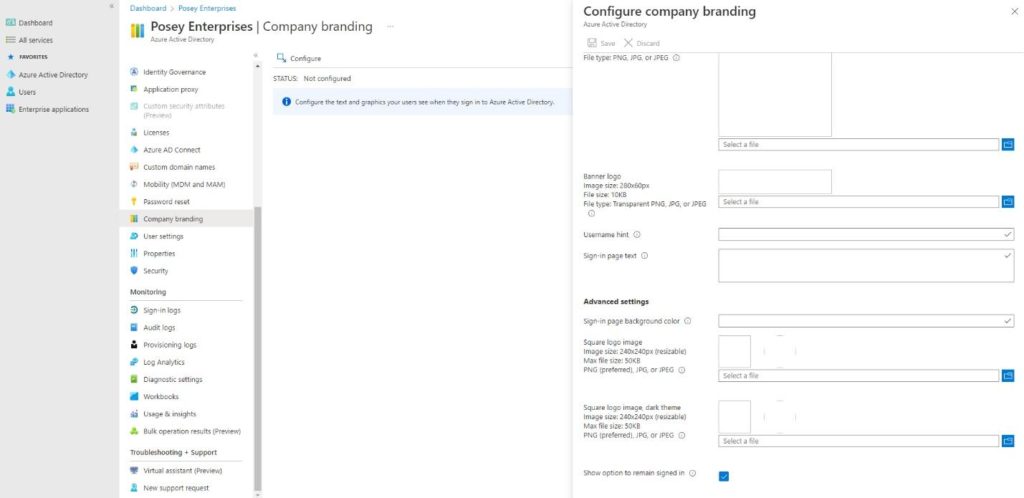
- Click the Azure Active Directory tab
- Choose Company Branding
- Click Configure
- Deselect the “Show option to remain signed in” checkbox under “remember Multi-Factor Authentication on trusted device.”
Now you have it! Overall, this is a straightforward procedure. You can now rest easy knowing you’ll no longer receive those pesky MFA prompts.
The Bottom Line
In this article, I talked about authentication prompts and how frustrating they can be to deal with. As a solution, I showed you how to enable Azure AD’s “Remember MFA” and “Keep Me Signed In” features. Hopefully, this article will help you and your organization deal with those obnoxious multi-factor authentication prompts.
If your organization requires better security, it’s essential you ensure that you don’t get constant prompts to authenticate. Excessive prompts can frustrate you and slow down your productivity.
Do you have more questions on Multi-Factor Authentication? Check out the FAQ and Resources sections below!
FAQ
Why doesn’t the Azure Active Directory Admin Center show the “Per-User MFA” setting?
The main reason the Per-User MFA setting sometimes disappears is because of inadequate display resolution. At lower resolutions, the console tends to hide this option.
How long will Microsoft allow a trusted device to remember Multi-Factor Authentication?
A trusted device can remember multi-factor authentication for as little as a single day or for as long as a year. However, Microsoft recommends that you set the number of days to a value of 90 or higher if you use this feature. The default value is 90 days.
Does the “Remember MFA” feature require Conditional Access?
The “Remember MFA” feature doesn’t require Conditional Access. It’s a feature that Microsoft provides organizations that don’t have a subscription that includes Conditional Access. Organizations with conditional access can use the “Sign in Frequency” setting instead.
Is the “Remember MFA” feature an alternative to the “Keep Me Signed In” feature?
Yes, you can use the “Keep Me Signed In” feature or the “Remember MFA” feature. You can’t use them together. Otherwise, Azure AD will create a verification loop and won’t authenticate users.
Will the “Remember MFA” feature work for non-browser-based applications?
If a user uses a browser-based application, they’ll see a “Don’t Ask Again for X Days” prompt. If the user uses a non-browser application, Windows will usually assume that the user doesn’t need any more reminders until the refresh period expires.
Resources
TechGenix: Newsletters
Subscribe to our newsletter for more quality content.
TechGenix: Article on MFA Changes and Azure Premium
Learn about the MFA-related challenges you may encounter when enabling Azure AD Premium-related features.
TechGenix: Article on MFA, Office 365, and PowerShell
Read more on how to collect users’ MFA information using PowerShell.
TechGenix: Article on Microsoft 365 Passwords and MFA Security
Find out how to ditch Microsoft 365 passwords in favor of better MFA security.
Microsoft: Guide on Setting Up MFA for Microsoft 365
Learn how to set up MFA for Microsoft 365.
Microsoft: More Information on MFA
Discover the basics of multifactor authentication.



