In the networking world, load balancers have been around for quite a while. There are different variants of these, for example, F5 and Kemp, but there are others. Some of them do layer 2 and others do layer 7 load balancing. Please note I am not promoting F5 or Kemp. These are the products I have worked with so I can speak from experience about them. A misconception for many people is that the F5 or Kemp is your firewall. OK, that can be debated. Yes, the load balancer is the Internet-facing device and rules can be set up to block things but remember you need to have antivirus software on your backend machines. Now in the Exchange world, specifically Exchange 2016 and Exchange 2019, you have a load balancer that will handle your protocols like Outlook on the Web (OWA), ActiveSync for mobile devices, Outlook Anywhere, or MAPI, to name a few. When you set up your DNS records you will point it to your load balancer. That is the first place clients will hit to get into their email.
Exchange load balancers: Basically, another virtual machine
Think of your load balancer as another virtual machine. Yes, these can be virtual and some admins prefer this while others prefer to have a physical device in their datacenters or at the home office.
Each of them has a different cost. Now, you want to have your load balancer be the frontman of your environment so you have to tell it what to do with traffic coming into the different ports on Exchange.
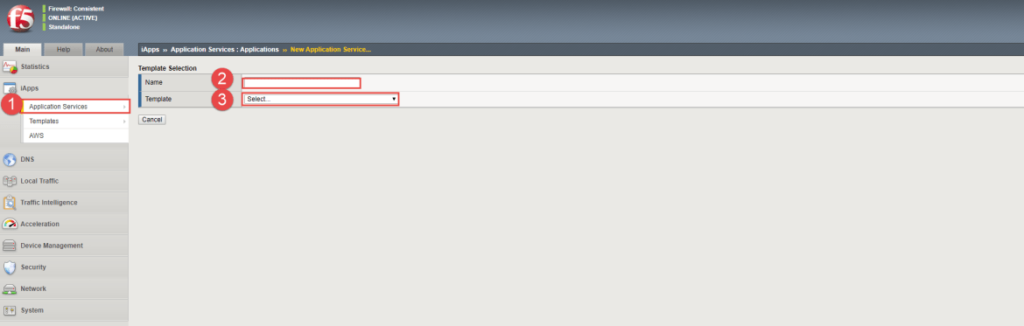
I know that on F5s you can create what they call an iRule, which is located under iApps. They have a template for Exchange 2010, Exchange 2013, Exchange 2016, and Exchange 2019. Once you have imported the template, you can go through a wizard that asks you questions that are pretty simple to understand and once done it then creates all your pools for you. Here are a few screenshots of this:
Selecting your template to use
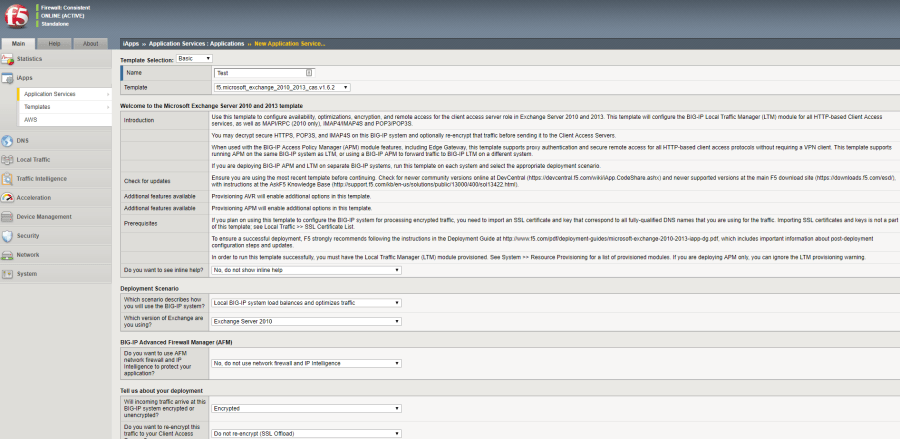
Questionnaire on configuring the iRule
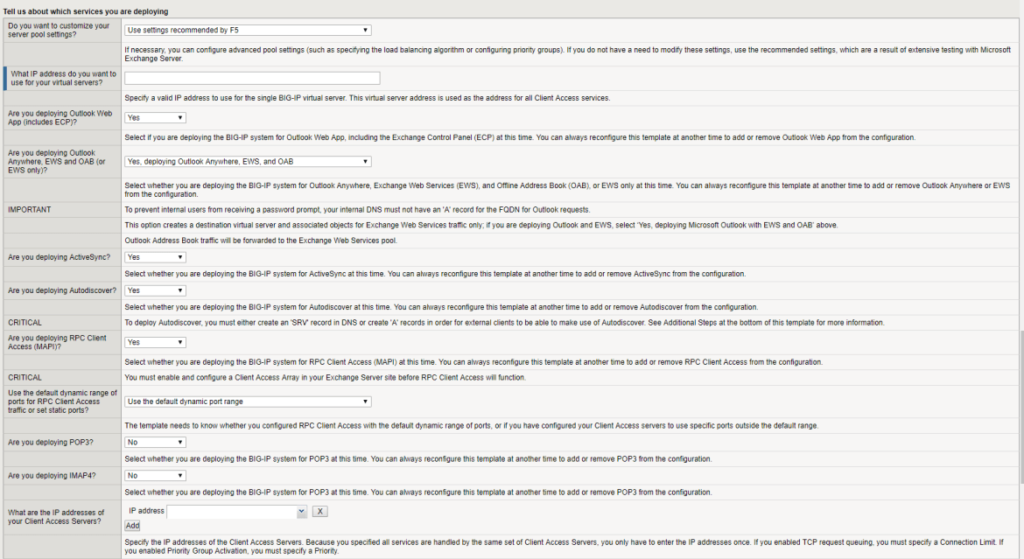
Page continued (as it is long)
Next page
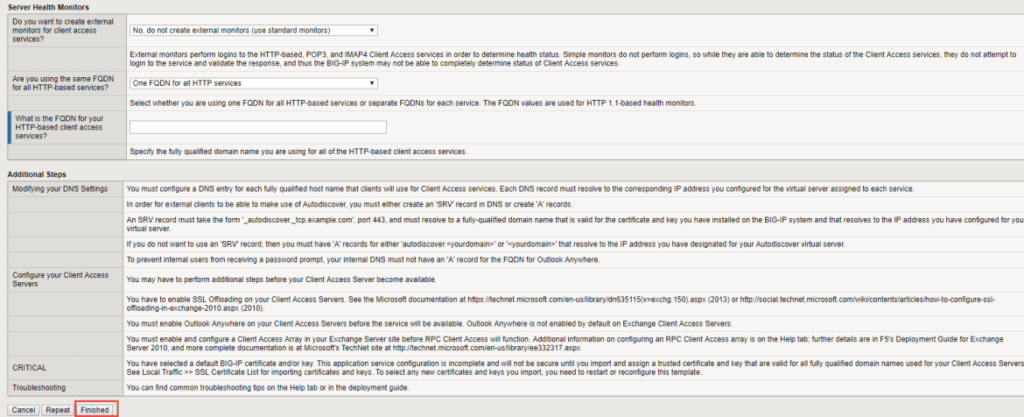
Once you have completed the questionnaire, you can click the Finished button and it will go and create everything for you.
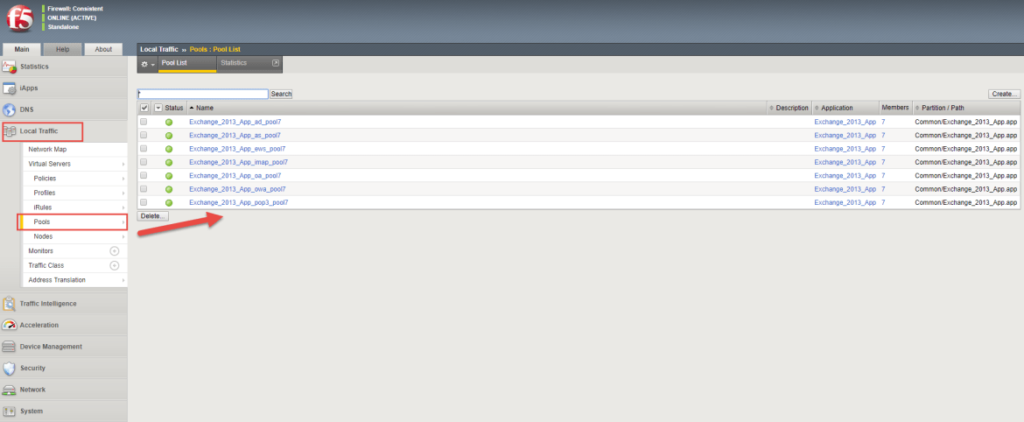
As you can see below, all the pools are showing. This example is for Exchange 2013, but for Exchange 2016 and above it is pretty much the same.
The Kemp look and feel is simpler than F5 as you can see below. (This is from the Kemp website as I don’t have an image on hand.)
If you are transitioning from F5 to Kemp, they do have a migration tool you can use.
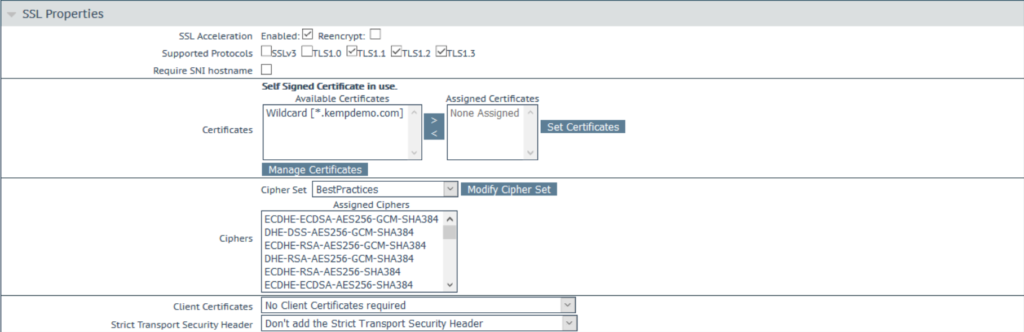
Moving forward to certificates, just like you have to import your SSL certificate you got from your provider of choice, you need to do the same on the F5 or Kemp. Remember, you cannot use internal server names on your certificates.
If you don’t import the SSL certificate, users will get the load balancer default certificate as a popup on Outlook. I know with F5 you need to import the intermediate certificate as well or it doesn’t see the certificate as valid.
The same goes for expired certificates. This is the one place many admins forget to update the SSL certificate and then clients get popups and they cannot understand why as they updated the certificate on Exchange and moved its services.
The next thing to look at is locking down your load balancer. What? Yes, you heard right. Let’s say you have an ISP that filters your mail. On the load balancer, you need to create a rule to only allow email on port 25 or 587 from their IP ranges to avoid becoming an open relay. If you have branches connected and your site is the hub, then you need to allow them to send on port 25 to your site.
The next thing you can look at is the cipher suites. Just like your Exchange Server, you can change what ciphers are allowed. I have written an article on ciphers for Exchange 2016 and Exchange 2019 that you can check out to see more of this topic.
Beware of malware
Another big thing that you need to be aware of, certainly in F5, is the fact that every VLAN can see each other from the F5 management perspective and this allows opportunistic malware to infect VLAN1, for example. But because the F5 can see all other VLANs, it can spread very easily. Be sure you lock down what can access what. Malware is evolving more and more these days.
Keep your Exchange load balancers clean
A big thing here is to regularly ensure your load balancer is kept clean. What I mean by that is that old rules are not left enabled or old ports like RDP or SMTP to a server you think is off but is left on. If that happens, that server and others will be hit with ransomware quicker than you know. If you are a new admin, then check what was left by the old admin and clean up the load balancer. Remember you are responsible now for the safety of your environment.
Remove old Exchange nodes. If you recently migrated from Exchange 2010 to Exchange 2016, then clear out the 2010 servers.
On a final note, think about using your F5 or Kemp load balancers to handle Exchange traffic alone and not SQL, Exchange, and others as you might hit that license cap with the number of connections and have users frustrated as they keep disconnecting. I have seen companies running multiple F5s, each one dedicated to a platform.
Featured image: Shutterstock




Thank you for this article. I hear the term load balancers, specifically F5 and Kemp used frequently and I have wanted to gain a better understanding of what it is and its relevancy. This article was helpful.