Introduction
Windows Terminal Servers play a special role in each environment. Technically they’re servers, but they’re used as workstations in that users log on to these machines to run end user applications. Luckily Group Policy has a feature called Loopback Policy Processing that addresses the need to apply specific settings to users based not on their user account’s location in Active Directory, but rather on the location of the Terminal Server Computer Object. This allows administrators to provide a locked down environment when users log on to these specific machines, without affecting the settings on their client machine.
Challenge
If one works for a large organization, the IT Department’s duties have likely been divided like a pie, so the people managing the terminal servers may have no access to management of Active Directory or Group Policy. If you’re lucky, the Active Directory people will concede to providing the Terminal Server Admins with an Organization Unit (OU) that they can administer. If not, you’re stuck using local policies, or getting the Active Directory People to apply the settings you want, either of which can be tricky in a large environment
Setup
To begin, we start with the Active Directory Users and Computers MMC where we want to add an OU to hold our terminal servers.
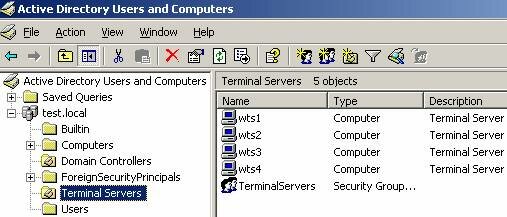
Once we’ve created our Terminal Servers OU we need to create a Group Policy Object (GPO) to manage these servers that will be placed in this OU. It’s worth reiterating that only the Terminal Server Computer Objects will be placed in this OU, as the location of the User Account Objects is irrelevant when using Loopback Policy Processing.
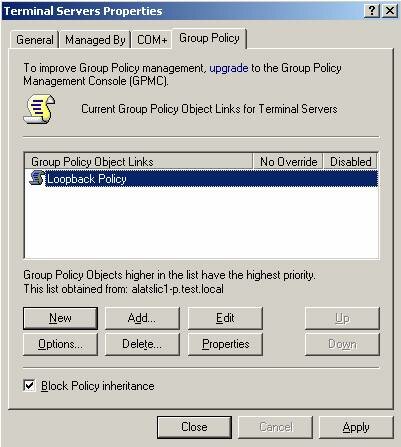
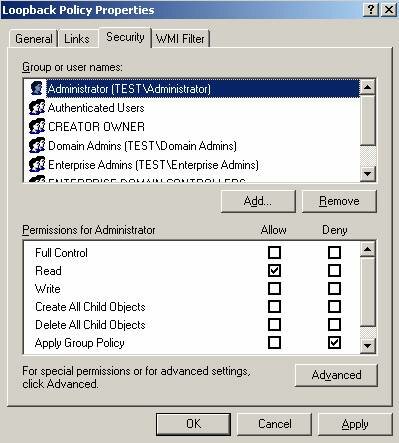
Since Loopback GPO are often created to provide a severely locked down user environment, it’s important that the account(s) used to manage the terminal servers are not affected by the policy settings. This can be accomplished by editing the security on the GPO and enabling “Deny Apply Policy” for these accounts, so when the user logs on the locked down environment will not apply. One should also enable the “Apply Group Policy” setting for the Terminal Server Computer Objects, or a security group of which they’re a member.
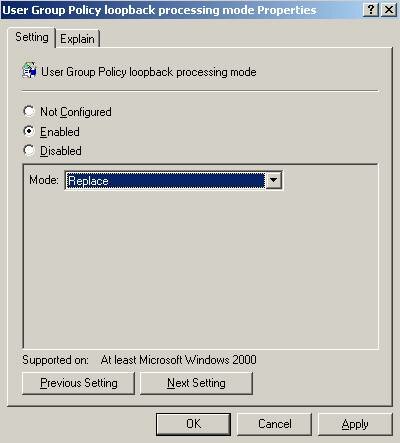
To enable Loopback Policy Processing in the GPO, navigate to “Computer Configuration -> Administrative Templates -> System -> Group Policy -> User Group Policy loopback processing mode”
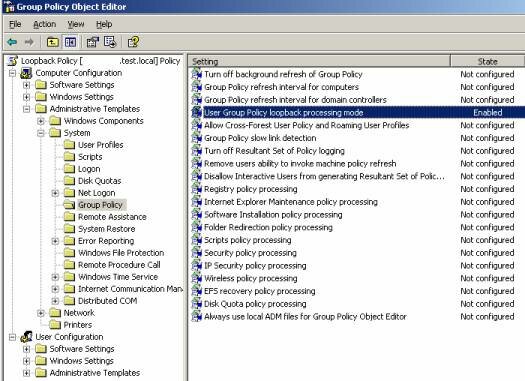
When enabling this policy setting, there are two options (Replace and Merge). If the goal is to only use the settings defined in this policy, Replace should be selected. If however the goal is to use the totality of the settings in this policy and the settings derived from the location of the User Account, select Merge.
Commonly Used Policy Settings
Now that we know how to create a GPO and enable Loopback Policy Processing, let’s discuss some commonly enabled settings for Terminal Server Environments.
- Terminal Server Roaming Profile Path – It’s of critical importance that the user’s normal roaming profile is not used when they log on to a terminal server, as this can cause profile corruption and data loss. Additionally, if user’s have a normal roaming profile, but no Terminal Server Roaming Profile is defined, the normal roaming profile will be loaded. To avoid this one can define the TS Roaming Profile Path via GPO.
When specifying the TS Profile Path enter the UNC Path to the share that will hold the user’s profiles. Do not use %UserName%, as the user’s folder will be automatically added at logon. It’s important that CREATOR OWNER has permissions to the share, or the folders will not be created when users logon.
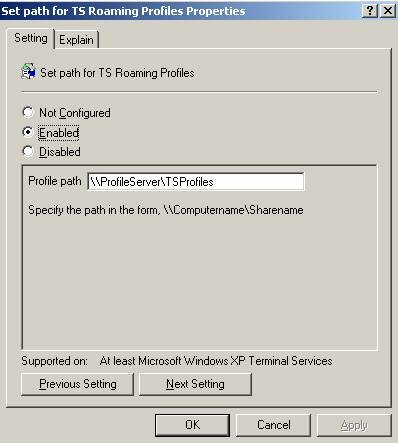
This policy setting is located at “Computer Configuration -> Administrative Templates -> Windows Components -> Terminal Services -> Set path for TS Roaming Profiles”
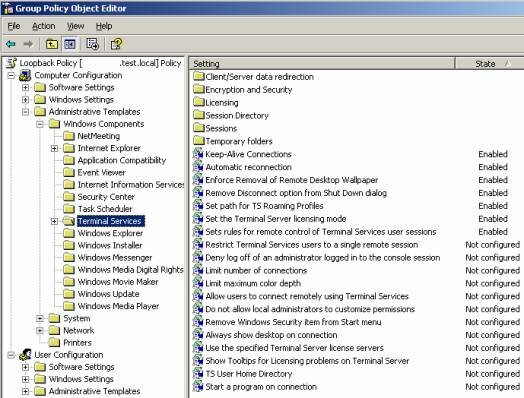
- Keep-Alive Connections – When this setting is enabled a heartbeat is used to keep a terminal services session alive when the session is idle, i.e. if the application is minimized.
- Automatic reconnection – Allows a terminal services client to reconnect to a disconnected session, instead of creating a new session on the same server. This setting does not account for the existence of multiple servers, nor does it direct users to a server with a disconnected session. These features are available via 3rd party load balancers or Terminal Server Session Directory.
- Enforce Removal of Remote Desktop Wallpaper – Allows administrators to prevent users from setting a desktop wallpaper, to reduce bandwidth requirements and improve user perceived performance.
- Remove Disconnect option from the Shut Down dialog – This option is often enabled if users logoff via the Windows GINA (ctrl+alt+delete) and user’s should logoff instead of disconnecting from their session.
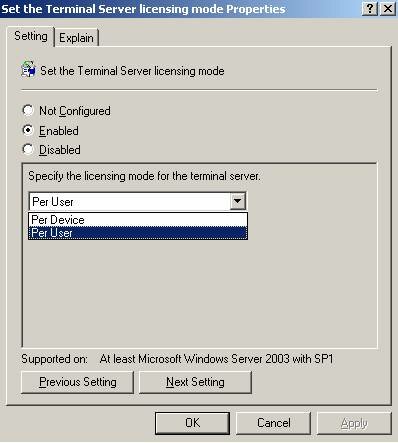
- Set the Terminal Server licensing mode – Overrides the Terminal Server Licensing Mode defined in the Terminal Server Configuration (TSCC.MSC).
- Set rules for remote control of Terminal Services user sessions – This session allows for the global configuration of Remote Control (shadow) of sessions, i.e, to set every session to Full Control without user’s permission
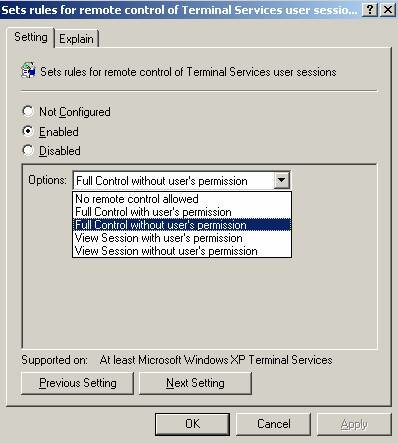
- Delete Cached Copies of Roaming Profiles – Even if TS Roaming Profiles are used, the local copy of the profile remains on the terminal server (by default). I a large environment with hundreds or thousands of potential users, leaving these on the terminal server can consume quite a bit of disk space. Enabling this setting will cause the deletion of the local profile at logoff, after it’s been successfully propagated to the TS Roaming Profile Path.
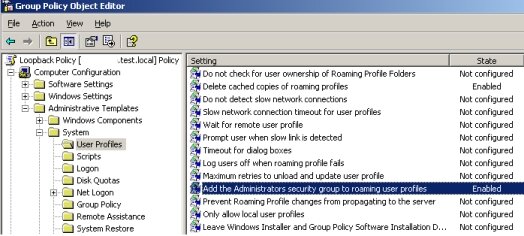
- Add the Administrators security group to roaming user profiles – By default, when user’s Roaming Profile Folders are created, only the specific user’s and the System Account have NTFS permissions to the folder. To alter this behavior, this policy setting can be enabled which will add the Administrators Security Group to new profiles. This setting does NOT affect profiles that were created before the policy was enabled.
- Terminal Server Fallback Printer Driver Behavior – This setting allows for auto-creating client printers using a generic PCL or PS driver, when the native driver is not available on the terminal server.
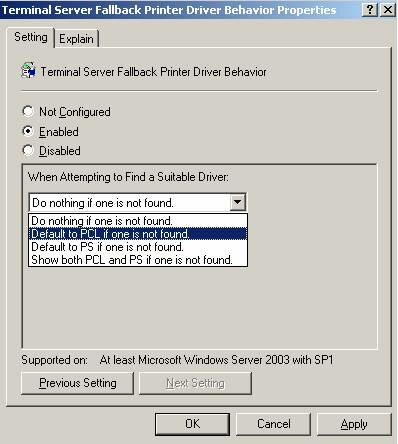
This policy setting is located at “Computer Configuration -> Administrative Templates -> Windows Components -> Terminal Services -> Client/Server Data Redirection -> Terminal Server Fallback Printer Driver Behavior”
- Folder Redirection – These settings help to decrease the amount of time needed to log on, by redirecting portions of the user’s local profile to network shares, i.e. the user’s home directory.
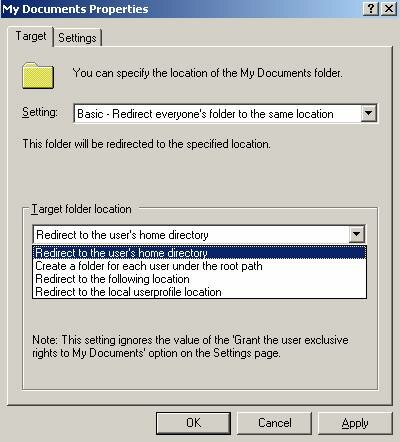
This policy setting is located at “User Configuration -> Windows Settings -> Folder Redirection -> My Documents” There are also options to redirect the Application Data, Desktop and Start Menu folders.
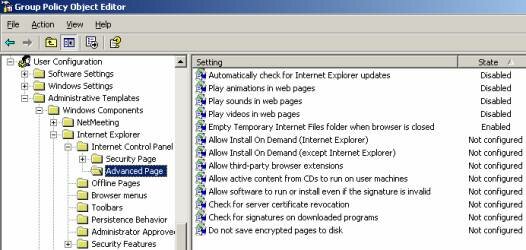
- Empty Temporary Internet Files folder when browser is closed – Enabling this setting will purge the user’s Temporary Internet Files when their Internet Browser is closed.
- Automatically check for Internet Explorer updates – Disabling this setting will prevent Internet Explorer from periodically checking for updates.
- Play animations/sounds/videos in web pages – Disabling these three settings can increase server scalability by reducing bandwidth, memory and processor usage when displaying web pages with embedded multimedia content.
Conclusion
While complete lockdown of Windows Terminal Servers is beyond the scope of this article, we’ve touched on several commonly overlooked or misunderstood settings that will enable Terminal Server Administrators to better control the end user’s environment and global terminal server settings.
References
Loopback processing of Group Policy
How to apply Group Policy objects to Terminal Services servers
