It’s often a question that IT admins ask Microsoft: how do we maintain cloud app security without violating user privacy? And that’s a darn good question — with an answer directly from Microsoft.
It’s a similar answer to how we search, how we browse the Internet (from an outsider’s perspective), and then some: you will be able to view the data in the management portal, of course, but the information would be anonymized and not associated with any single individual.

This, according to Microsoft, is a win-win for both the tech conglomerate and the end user. See data without knowing who is doing what. IT admins win by learning how the cloud is being utilized and quantifying risk, but the user data is preserved and unknown to the IT admins. With that, SaaS applications can be sanctioned for visibility, data control, and threat protection — without threatening the user.
How to anonymize data on the Microsoft cloud
Cloud data is collected through the simple use of logs used by your infrastructure’s firewalls or proxies. You will have to upload the log, and when you do so, check “Anonymize private information” when adding a new data source or creating a new snapshot in the portal. Uploads are encrypted by AES 128 and a dedicated key.
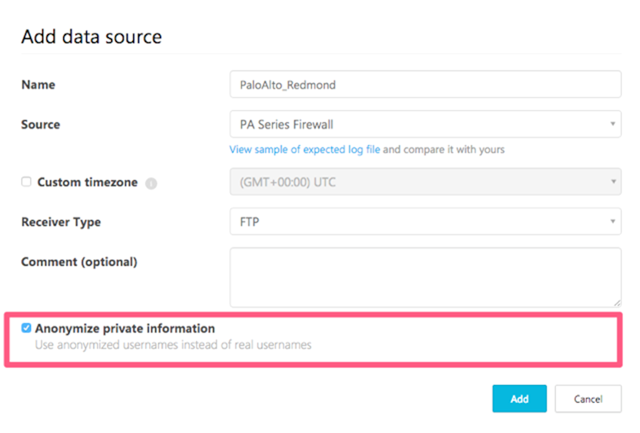
Why is this optional? Good question. Microsoft says that there could be a legitimate breach or security information that warrants the discovery of the “culprit,” the username behind the security hole. Cloud App Security, therefore, allows IT admins to decrypt the username with a valid justification–but just a note, there’s an audit process that goes into this as well in the Cloud App Security console.
Cloud App Security risk assessments
Once you’ve got the data uploaded and parsed, you’ll be given a plethora of information about cloud app usage within your organization. Over 13,000 cloud applications in the network are identified to date from all devices, and they are scored in terms of risk and analyzed. Click to dive deeper to learn about usage, most used app categories, and top users (from an IP address perspective).
With risk assessment scoring, you’ll learn if a cloud app is dangerous which gives you the choice to sanction or to block it. An example provided by Microsoft indicates where this could be useful: a download and upload of terabytes of data within a couple of transaction may be indicative of some malicious goings-on. An alert will pop up and give administrators the information they need to take further action.
Sanctioning and blocking apps with Cloud App Security
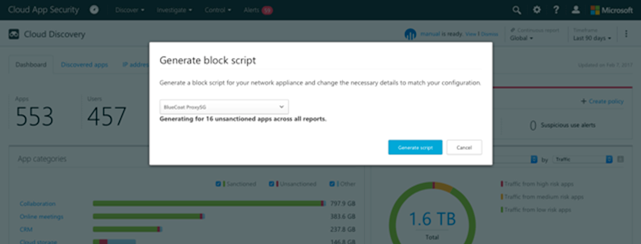
The next step after you know the risk assessment is to sanction or block the app. A block script can be generated to unsanction apps that is easy to use and utilizes on-premises security appliances.
Learn more about Cloud App Security here.
Photo Credit: Microsoft, Shutterstock



