
In recent years, NIST, Microsoft, and others have been recommending that you don’t force users to change their passwords periodically. Forced password rotations can actually weaken security. That’s because users have trouble remembering new passwords. As a result, they’ll often compensate by adopting risky passwords or writing their passwords down. On the flip side, a password reset is crucial if you face a data breach! In that case, everyone has to change their passwords right away.
Unfortunately, Windows doesn’t directly support bulk password resets. Still, you could do that through PowerShell. In this article, I’ll show you how to mandate a password reset across the organization. The process is divided into 3 main steps.
1. Retrieving a List of Active Directory Users
The first step in using PowerShell to force an organization-wide password reset is to get a list of all of the users in the organization. The easiest way to do this is to use the Get-ADUser cmdlet.
Unfortunately, entering Get-ADUser by itself won’t make PowerShell return a user list. The cmdlet requires you to append a filter. If you truly want the results to include all users, the easiest thing to do is to filter based on user name. Then, use an asterisk to designate a wildcard value (so that PowerShell returns all names). To do so, follow these 4 steps:
- Log in using an account that has domain admin permissions.
- Open an elevated PowerShell session.
- Make sure that PowerShell’s ActiveDirectory module is installed if you aren’t working on a domain controller. You can check the module status by using the Get-Module cmdlet. If necessary, you can install the required module with the Install-Module cmdlet.
- Enter the following command:
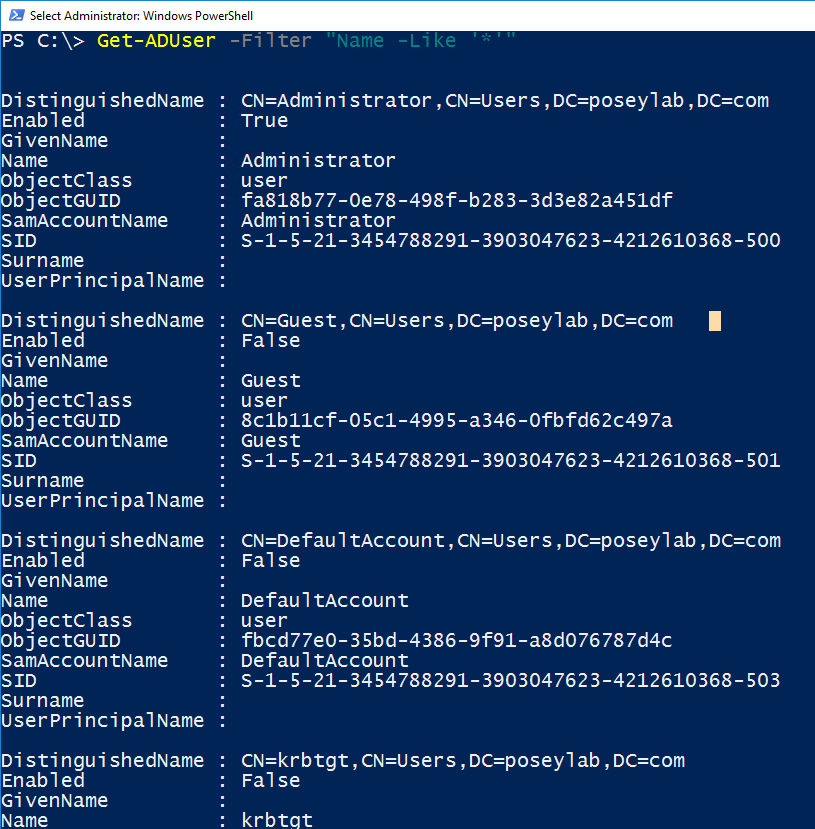
| Get-ADUser -Filter “Name -Like ‘*’” |
A Word About Filtering
The technique shown above will indeed retrieve a list of all of your Active Directory user accounts. Yet, it’s usually a bad idea to force a password reset on every account. For example, organizations often have a break-glass account. You can use this account in emergencies to regain access to the network following an accidental lockout. Forcing a password reset on a break-glass account probably isn’t necessary. In fact, these accounts usually have extremely secure passwords already and are only used in extreme emergencies. The point is that you should carefully consider if any accounts need to be excluded from a forced password reset.
Now that you have your user list, you should also consider which accounts you’ll exclude. I’ll show you how.
2. Excluding an Account
To exclude one or more accounts from a password reset, you’d use different techniques. It depends on the number and location of those accounts and other factors. Even so, I wanted to give you a brief example of how you might exclude an account.
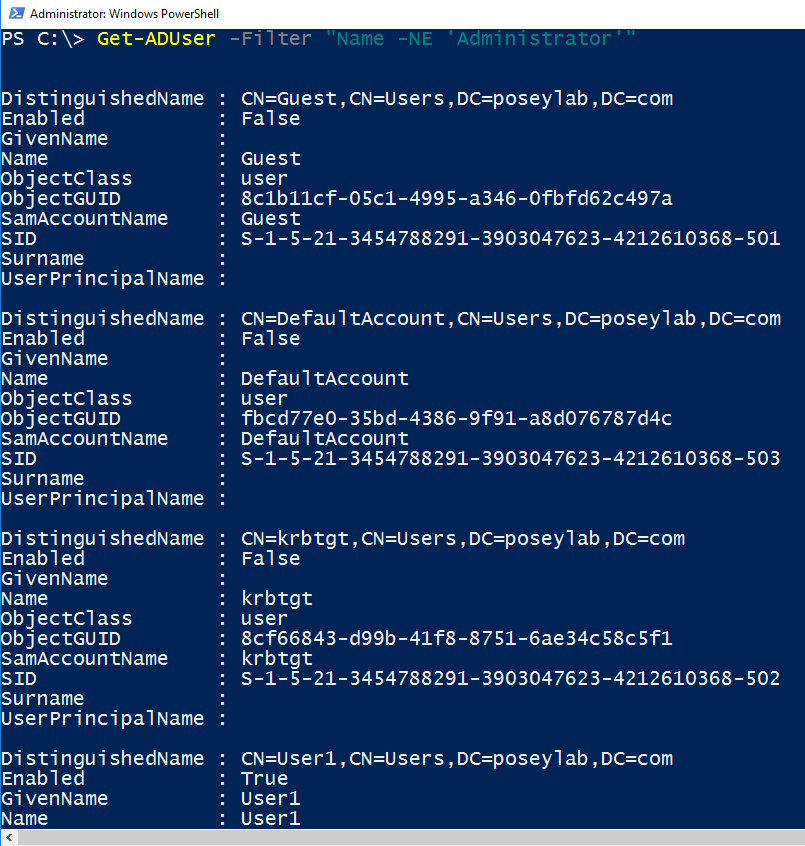
Suppose for a moment that you wanted to exclude the domain admin account from the forced password change (I’m not suggesting this, this is only an example). You could exclude the domain admin from the user list by using this command:
| Get-ADUser -Filter “Name -NE ‘Administrator’” |
Great! Now, you should have your definitive list of those involved in the password reset. Next, you’ll have to put this in motion. Let me show you how.
3. Forcing a Password Reset
Once you’ve compiled a list of user accounts, forcing a password reset is easy. Simply use the Set-ADUser cmdlet. Then, set the value of the ChangePasswordAtLogon attribute to $True for the selected accounts.
Suppose for a moment that I wanted to force a password reset for all of the user accounts whose account names begin with the word user. I could do so by using these commands:
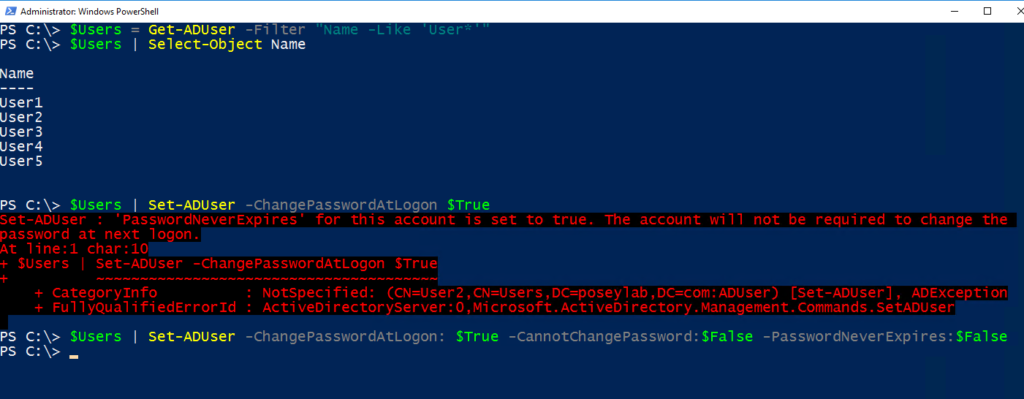
| $Users = Get-ADUser -Filter “Name -Like ‘User*’” $Users | Set-ADUser -ChangePasswordAtLogon $True |
As you look at the code above, you’ll notice that the first of the two commands assigns the user list to a variable named $Users. You don’t need to do so, but using variables can sometimes make the process a little bit easier. It’s also helpful if you need to set up multiple filtering rules.
What Went Wrong
The code shown above can sometimes produce an error. For example, some accounts are set up so their password never expires. In other cases, the user is prevented from changing passwords. You can get around these problems by appending -CannotChangePassword:$False and -PasswordNeverExpires:$False. Here’s an example:
| $Users = Get-ADUser -Filter “Name -Like ‘User*’” $Users | Set-ADUser -ChangePasswordAtLogon: $True -CannotChangePassword:$False -PasswordNeverExpires:$False |
You can see the entire command sequence in the figure below. Note that you don’t need the second line of code. I only included it so you could see the list of user accounts for which I’m forcing a password reset. Initially, I only attempted to force a password change at logon. Yet, this failed because one or more accounts were configured with passwords that never expire. To solve this problem, I set PasswordNeverExpires and CannotChangePassword to $False.
Final Thoughts
An organization-wide password reset shouldn’t be taken lightly. You also shouldn’t perform it frivolously. Even so, it can be necessary in the event of a security breach or a suspected breach. If you don’t have access to third-party password reset tools, then your best option is to use PowerShell’s Get-ADUser and Set-ADUser cmdlets.
This way, you can even exclude some accounts from the password change, and even get over other restrictions! In turn, you’ll be able to keep your company safe against attacks.
Do you have questions about AD password resets? Check out the FAQ and Resources sections below!
FAQ
When would I force an organization-wide password reset?
Forcing everyone in the organization to change their password is drastic action. You’d normally only do this in the event of a security breach or a suspected security breach. If you’re thinking about conducting this action, you should also consider your security procedures. Additionally, implement multiple authentication routes to improve security.
Should I exclude accounts from an organization-wide password reset?
Every organization’s needs are different, so no definitive answer applies to every situation. However, you should think twice before forcing a password reset on service accounts. Doing so could cause applications to stop working. You should also exclude break-glass accounts where possible.
What types of modifications might an organization need to make to a password reset script?
Besides potentially excluding certain accounts, the biggest modification that might be needed is to add support for additional domains or trusted forests. To do this, run a PowerShell script. Then, apply changes globally, assuming you’re dealing with a single domain forest. For multiple domains, you’ll need to run multiple scripts.
What are the implications of using PowerShell for password resets in SSO environments?
You can implement SSO in many different ways. If the Active Directory is acting as the primary identity provider, then you’ll first need to establish a list of users. Then, exclude accounts that should be excluded from the GUI. Otherwise, your script could break your SSO.
Can I manually force a password reset without PowerShell?
Yes. You can right-click on a user account in the Active Directory Users and Computers console. Then, select the Reset Password command from the shortcut menu. Unfortunately, this console doesn’t support bulk password resets, so you’ll have to do it one account at a time. For larger businesses, learn PowerShell. It’s also useful for other global management tasks.
Resources
TechGenix: Article on Self-Service Password Resets
Learn how to enable self-service password resets in Azure AD.
TechGenix: Article on End-User Frustration from Password Resets
Read more on how to cope with the end-user frustration associated with password resets.
Microsoft: Article on Local Password Resets in Windows 10 & 11
Find out how to reset local passwords in Windows 10 and 11.
TechGenix: Article on Passwordless Authentication
Discover why organizations will eventually adopt passwordless authentication.
Computers N Stuff: Article on Resetting a User’s Password in AD
Read more on how to reset a user’s password in Active Directory.
TechGenix: Article on Different Password Reset Methods
Discover several additional ways to reset users’ passwords.



