
Manufacturers and plants use economies of scale and integrated control systems (ICS) to help streamline production and reduce unit costs. This could be the cost per electric vehicle in a manufacturing 3.0 or above automated plant. It could also be the cost per unit of energy that a nuclear power station produces. Highly integrated and automated businesses leverage information technology (IT), internet of things (IoT), and operations technology (OT) to streamline production. You also can use the Purdue model to help show the relationship between each technology in these highly-integrated systems. Generally, understanding these relationships and boundaries makes it far easier to secure your network.
Operational technology (OT), also called integrated control systems, are technologies used to control plant or manufacturing equipment. Originally, these ran on hardwired networks. Additionally, they aim to allow users to move data from a computer to a machine or work cell. Over time, Wi-Fi also became popular, but the underlying code design didn’t have security in mind. This is a major challenge in highly-integrated manufacturing plants working with a larger supply chain. Now, cybercriminals use ICS integration to gain access to the IT infrastructure. This is to implement ransomware attacks or damage to a nation’s infrastructure directly through OT.
In this article, I’ll discuss the Purdue model and ICS security as a whole. Firstly, let’s take a look at what the Purdue model is.
What Is the Purdue Model for ICS Security?
The Purdue model was created in the early 90s at Purdue University to define the relationship between industrial control systems and business networks. The terms OT and IT are also used interchangeably.
The Purdue Reference Model attempts to define ICS in six levels related to the amount of automation utilized. This is to help logically define boundaries between OT and IT networks. It also creates controls necessary for securing these networks.
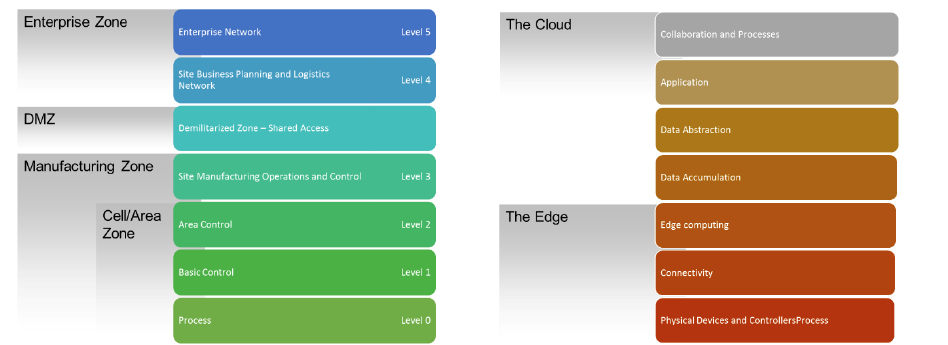
Level 0: Dumb Physical Devices
Level 0 includes hardware that builds products or is used in workflows. These devices include motors, sensors, pumps, and valves. Some of these will have some feedback to add a level of automation. For example, a valve may have a mechanical pressure release that redirect flow of a fluid in a system for safety. In this scenario, you can’t apply logic to the component. You also won’t have any discretion based on the rest of the system. Additionally, feedback will only relate to that component. The pressure release may actuate, but the route cause of the issue is still there. Thus, an eventual catastrophic failure of the system may occur. Operators also won’t realize the presence of an issue with the device.
Level 1: Devices with Feedback
Level 1 includes systems that monitor and provide some form of feedback. These can include Programmable Logic Controllers (PLCs) and Intelligent Electronic Devices (IEDs). Basic industrial control systems controlling brewing vat temperatures are also a good example of level 1 systems. If the temperature gets too high, a bimetallic strip may turn off the heat source.
Level 2: Process Management
Level 2 devices can control the overall processes within the system. Human-machine interfaces (HMAs) and SCADA software can allow plant workers to monitor and maintain a process. You can think of level 2 as having a dedicated control panel with controls and readouts for one process hosted in a control room of a plant. Level 2 process controls are often hardwired to manufacturing or plant hardware. Intelligence comes from the operator interpreting sensor readings and controlling processes manually. Additionally, experienced and well-trained operators need to make the entire operation run effectively. Failure to comprehend a potential issue could mean a catastrophic failure of the operation and loss of the plant.
Level 3: Operations Management
Level 3 supports production workflows including processes and operations. A good example is manufacturing operations management. This is effectively similar to level 2, but an HMA or SCADA system manages the entire operation. Operation-wide automation reduces the need for the user to pay attention to each process. This reduces the risk of a simple oversight causing catastrophic damage. OT and IT network integration is also possible at this stage. This can come about to expedite purchasing resources or cater to client needs within the supply chain by automating the push or pull of the business.
Level 4: ERP Integration
Level 4 often leverages Enterprise Resource Planning (ERP) to integrate various software solutions to streamline workflows. Databases from different software solutions often merge into the ERP solution. Email servers and other systems including logistics and manufacturing operations also merge, streamlining a company’s productivity. To achieve this substantial preparation of hardware, networks and data are required as well as workshops company-wide for personnel.
Level 5: Enterprise Integration
Level 5 is the enterprise network that collects data from ICS systems for business decisions. Integration of enough workflows and systems enables a top-down overview and control of operations based on business needs. Level 5 often integrates supply-chain push-and-pull requirements through collaboration with a business’s external parties. Automotive manufacturers may automate a pull quest of tires to be delivered exactly when the production line needs them. This ensures that the manufacturer keeps zero inventory. This happens often through service contracts specifying a service-based approach to added value to the manufacturer. Note that products are only the means to achieve the specified service level.
Now that we’ve covered the 6 levels of the Purdue model, let’s discuss how relevant this model is today.
How Relevant Is the Purdue Model Today?
The Purdue model is still relevant as it highlights where network boundaries are and what you need to secure. That said, operations change over time in a manufacturing or operational environment. To deal with constant ICS security changes as workflows are continually rejigged, you should use OT risk assessment software to highlight ICS security weaknesses.
Now we know each level of the Perdue model, let’s take a look at ICS security.
3 Strategies to Improve ICS Security
How do you protect integrated control systems? Levels 0 to 2 have effectively no integration between the OT and IT network. To protect these systems from attack is relatively simple; stop cybercriminals from gaining physical access to the locations where these systems reside. To protect companies of higher integration levels, you can use the following 3 strategies.
1. Air-Gapping
At level 3 or higher, you can use air-gapping to improve ICS security. This is where you have a physical gap between networks or devices to secure them. This also stops attacks invading one system and jumping to another, as you have no way to convey the attack. You’ll find this useful in the case of both a mix of trusted and untrusted traffic.
Cyberattacks often go through unsecured OT or IoT devices before gaining access to IT devices. Both OT and IoT devices aren’t designed for ICS security and IT integration, mainly because devices must be competitively priced in the marketplace; adding security features often doesn’t improve sales. OT communication layers also don’t use encryption or any form of security-based protocol. This makes it a major security challenge.
Pro Tip:
- OT security changes as OT workcells are repositioned for different manufacturing requirements. When changes happen, you need to conduct a risk assessment.
- You can use OT risk assessment software. This takes a copy of the production environment and runs continuous simulations of a variety of cyberattacks to ensure OT is adequately protected.
2. The Challenges of Connectivity
Both OT and IoT devices aim to increase productivity through easy connectivity, (usually through Wi-Fi). Wi-Fi helps reduce cable routing needed in an industrial environment helping to save on costs. However, this makes both technologies susceptible to man-in-the-middle (MIM) attacks. In these attacks, a bad actor adds a router as a data relay between two Wi-FI connections and monitors or adds code as if it was the user conducting the action.
One of the best, yet worst features of Wi-Fi is that it broadcasts and looks for devices to conduct a handshake with. Problems arise when manufacturers use the same firmware passwords and connection details. They’ll ask users to change the connection password during setup. This doesn’t happen often as the passwords used should be easy to remember for assembly staff. They’re also easy to find on the internet. You can simply search for a device you’re interested in and check either the installation documents or maintenance documents. You’ll often find these quickly.
Pro Tip:
- When given the option, always connect hardware OT or IoT devices to nesting networks that create the security for the OT or IoT system.
- Most OT solutions don’t have automatic updates to firmware or applications. You should schedule regular checks for updates and patches.

3. Profitability and Security
Businesses want to streamline workflows to reduce unit costs. In return, this achieves greater profits. Unfortunately, integration also helps reduce barriers for bad actors once they have access to a network.
To improve security, be careful of open ports in integrated environments. Again, OT and IoT device manufacturers often don’t care about hardening their products. Many will even have an open port somewhere. Most devices will also use freeware to create solutions to keep unit costs down. You should also expect a generic linux distribution with default credentials. To ensure your devices’ safety, try using Shodan and searching your companies IP addresses. Shodan facilitates finding open ports and even accessing cameras for non-security professionals.
From level 3 and higher, systems are more integrated and more susceptible to attack. Unfortunately, OT or IoT devices are a weakness to your security. Once your security is integrated, it provides an easy route into high-level companies. This includes oil refineries, hydroelectric power plants, and other national assets.
That said, you can use OT risk-assessment software that creates a real-time duplicate of your system. It also simulates attacks using AI and provides advice on how to better secure your OT. This is exceptionally useful for manufacturing companies where machine cells and processes change over time. As these change with no air-gapping, they open and close attack surfaces that make you prone to risks.
Pro Tip:
- You should search for maintenance manuals online for each IoT device. Use the generic credentials often used for all devices and change it yourself for the operating system and firmware as needed.
- You must use firewalls that enable you to use automatic router encryption. This is to ensure the default encryption of all connections including IoT devices. This also helps you protect mobile phones and lightweight platforms using the network.
- If you can’t block ports due to not having generic credentials from the supplier, modify the hardware to physically block easy access. You can also replace one or more generic screws in cases with security screws. This stops access to internal ports or maintenance communication connections that you can use to gain access to the firmware and operating system.
The Need for Zero Trust in ICS
As I mentioned, as soon as you integrate OT and IoT into your IT solution, you’ve created a major security risk irrespective of productivity during use. To help, you can use the zero-trust security strategy to secure your network better.
How does this strategy work? It eliminates implicit trust mechanisms in the network and requires continuous validation at every stage of a digital interaction. Although this method works better at securing your network, it’s perfect. This is because OT in particular isn’t designed to run with any security protocol. Originally, it was designed to get machine instructional code from a hardware networked computer to a computer numerated control (CNC) machine. Now, we have wireless data transfer but still no security on this layer. IoT is much more recent technology and where zero trust can be effective.
Final Thoughts
The Purdue model is a fast and effective way of assessing network boundaries and security challenges based on the level of automation utilized by a company. The challenge with the model is that it suggests that you can effectively secure a network using integrated IT, OT, and IoT. To help your business become competitive and integrate different technology networks, you must consider using an OT risk assessment software. This is to simulate attacks and define attack surfaces that need patching or protecting through nesting OT equipment. If you’re integrating IoT software, consider a zero-trust strategy at the expense of overall system performance.
Have more questions about the Purdue model? Check out the FAQ and Resources sections below.
FAQ
What is the Purdue model?
The Purdue model was created in the early 90s at Purdue University to define the relationship between industrial control systems and business networks. The model has 6 levels related to the integration of automation used by a business. The terms OT and IT are also used interchangeably. The model’s goal is to help highlight network boundaries and pin-point security requirements.
What is Operations Technology?
Operations technology (OT) is plant and manufacturing networks used to implement automated plant operations. Streamlined automotive manufacturers, for instance, use OT to automate machine cells on production lines controlled by a centralized network. This helps the manufacturer or plant change operations and production runs quickly.
Why do companies integrate OT with their IT solutions?
Operations technology (OT) is often integrated into IT solutions to streamline data analytics and operations monitoring and control. It also automates resource acquisition from suppliers upstream of the business. Likewise, you can pass client orders straight into production line queues for manufacture and shipping to automate orders. by.
Why do companies integrate IoT with their IT solutions?
Internet of Things (IoT) enables companies to use wireless and modular edge hardware in remote locations of a factory to feed data back to a centralized system. If too much scrap is produced during a manufacturing process, IoT data can help automate ordering of more material using an IT system. This is to meet the expected shortfall; saving time and money.
How do cybercriminals benefit from OT Integration?
Cybercriminals currently target companies that integrate their IT with operational technology (OT). This is due to the inherent weakness of OT since the technology doesn’t much consider security or wireless connectivity. This makes it an easy target for attackers to inject a payload that spreads to the IT system. Common attacks include ransomware or are purely destructive and orchestrated at a government level in some scenarios.
Resources
TechGenix: Operations Technology Article
Learn about OT and how to secure it.
TechGenix: IoT Cyberattacks Article
Discover what IoT cyberattacks you need to protect your company against.
TechGenix: 6 IoT Communication Protocols Article
Find out what the 6 IoT communication protocols are.
TechGenix: Industrial Cyberattacks to Watchout for Article
Discover what industrial cyberattacks you need to protect your business from.
TechGenix: AI Predictive Risk Assessment Software Article
Learn how AI predictive risk assessment can help protect your operations technology integrated network.



