Cyberattacks are increasing as networks become more complex through technology integration. Consequently, attackers can exploit more security gaps than ever before. This is where network vulnerability scanners come in!
Network vulnerability scanners (NVS) enable you to scan your existing infrastructure and identify security flaws. An NVS should be part of any administrator’s toolkit to help ensure you haven’t missed any security gaps.
In this article, you’ll learn how to use an NVS to secure your network. We’ll then look at the top 5 NVS solutions on the market in 2022. But first, let’s go through what NVS is!
What Are Network Vulnerability Scanners?
An NVS is a network analytical solution that maps the network you deploy it in. You can then use it to identify known weaknesses using a list of known threats the vendor has populated. To get your head around how the list works, consider the 2 main types of vulnerabilities; internal and external.
NVS solutions identify internal vulnerabilities based on access control levels (ACLs), network topography, and software types. In the case of external threats, the scanner checks port blocking, firewalls, and filter lists to stop nefarious actors from gaining access to your network.
For example, a database running on a separate server will need a connection to the application software with known ports, ACLs, and defined users. The database server won’t need its FTP port open. It also won’t need other users except the database user to have connectivity. NVS solutions will know this based on their vulnerability list and look for similar exploits.
The vulnerability lists include all the necessary metrics for the NVS to scan and classify a vulnerability’s impact as the vendor has determined. You’ll then get a report and some guidance to administrators to resolve the issue.
Types of Network Vulnerability Scanners
NVS work using intrusive or non-intrusive assessment methods. Essentially, intrusive scanning tools will give you more useful information about each vulnerability, even though they disrupt the network. Unintrusive scanners can still identify issues but may not capture the full extent of the vulnerability.
You’ll often find NVS divided into the following 3 types based on their deployment type:
- Network-based vulnerability scanners; work inside the network for internal vulnerabilities but use network resources. Great for highly secure closed networks and siloed operation environments.
- Agent-based vulnerability scanners; utilize a remote worker agent to implement scanning to reduce the impact on resources in production environments. It needs dedicated infrastructure to support it.
- Web application vulnerability scanners; are a cloud-based working similar to an agent-based scanner to reduce the impact on resources in production environments. Often low-cost Sales-as-a-Service solutions don’t require infrastructure expenditure.
In addition to intrusive and non-intrusive classification, you can also further categorize NVS solutions depending on the network parts that they assess. This is important to know when selecting your NVS solution.
NVS Categories
Check the following comparative table to assess which scanner category may fit for your firm’s security needs.
| External Scanners | Internal Scanners | Environmental Scanners | |
| Target | Internet or public facing parts of the network environment | Internal network software | Whole network environment and are designed specifically for the network they’re on |
| Vulnerability Types | Are great if you’re only worried about external threats. E.g., web hosting. | Stop threats that have reached sensitive parts of the business from causing problems | Are good for internal and external vulnerability assessment |
| Use Cases | Exploit surface protection | Business-critical data | Multiple technologies including IoT devices, websites, cloud-based services, and mobile devices |
| Assessment | Perimeter vulnerabilities for: Applications Websites Ports Services Networks and systems that external users access | Sensitive business parts, internal vulnerabilities like: Hosted websites Applications Services Networks and systems that internal users access | Perimeter and internal network vulnerabilities |
As shown above, you’ll find many network vulnerability scanner types suitable for many use cases. Let’s dig deeper into their key features to help you narrow down your selection.
The Key Features of a Network Vulnerability Scanner
NVS solutions vary extensively depending on their use case. That said, you can expect a good NVS to have a comprehensive list of vulnerabilities. For all-in-one solutions, you’ll need an NVS that can find network perimeter attack surfaces, internal software, and platform vulnerabilities. Don’t purchase a perimeter NVS expecting internal scanning and vice-versa. To this end, ensure that your NVS solution can also scan while looking at the list of vulnerabilities it checks.
You’ll often find that NVS solutions are integrated with other security solutions. Thus, vulnerability scanning and security hardening can happen at the same time. Most next-generation firewall solutions or antivirus software will also offer some form of NVS. To achieve administration synergy, try to opt for an all-in-one solution.
Ensure any solution you choose can also provide automated network detection, operate cross-platform (if required), and create security audits. In addition, ensure your solution can check for injection-based vulnerabilities, even for database servers.
Since you have many features to check for, I’ve narrowed the search down to the top 5. Go through the list and check which NVS will suit your business.
The Top 5 Network Vulnerability Scanners
Below, we’ll look at the top 5 NVS solutions available on the market.
1. GFI LanGuard
GFI LanGuard provides you with a virtual all-in-one software package. Here are some of its features:
- In-depth reporting through risk analysis
- Audit compliance; PCI DSS, HIPAA, and SOX
- Agentless or agent-based scans
- Assessments for everything from servers to mobile devices and printers
- Language detection for all vulnerabilities, including injection-based attack surfaces
- Patch-cross platform operating systems
- Script implementation, making it an excellent choice for any network
Finally, GFI LanGuard is available at different price points and offerings. This gives you a tailored introduction to this all-in-one network security solution. GFI understands it’s far better to support your business needs and make the solution easy to implement without denting your budget. 30,000+ systems currently run GFI solutions and have gained trust across many diverse sectors.
2. beSECURE

Beyond Security’s beSECURE is a cloud-based vulnerability assessment and management solution. It offers real-time threat assessment in any type of cloud solution. beSECURE gives you the most effective network security possible with minimal administrative interaction. Its features include:
- Network and application vulnerabilities scanning
- Daily updates and specialized testing methodologies to find security threats
- 99.99% of known vulnerabilities detection
- Boot up to scanning time of fewer than 5 minutes
- Support for both cloud and hybrid infrastructure solutions
- Bug-bounty programs for anyone who discovers a proven false positive
- Real-time penetration testing without the need for security consultants
- 24/7 service configuration and monitoring
All these features make beSECURE popular with administrators.
3. OpenVAS
Greenbone Network’s OpenVAS is an open-source, all-in-one network vulnerability scanner. Here’s what it does
- Offers unauthenticated and authenticated testing
- Performs security checking to ensure high-level and low-level internet and industrial protocols are met
- Obtains the tests for detecting vulnerabilities from an established feed that has been around for years and runs daily updates
The OpenVAS scanner is also part of the Greenbone Community Edition Package and works together with other open-source modules.
4. Qualys Web Application Scanner
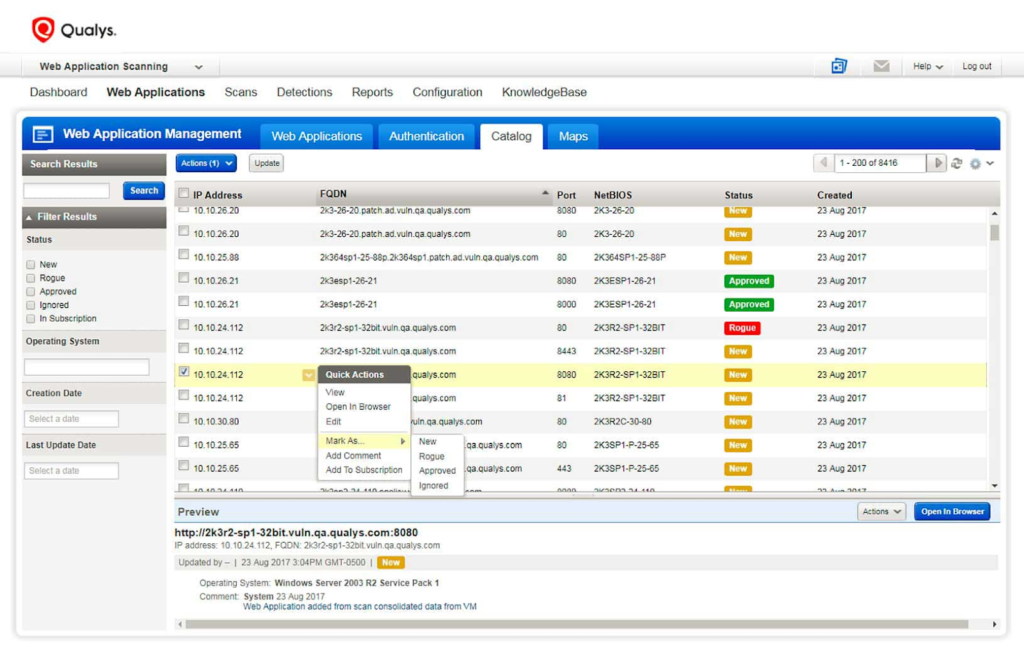
Qualys Web Application Scanner (WAS) is, as the name implies, a web application scanner. It doesn’t have all the features of the solutions above but is nonetheless a useful NVS solution.
Web applications are often plagued by vulnerabilities and misconfigurations resulting from either poor coding or poor hardening practices. One misconfigured or badly-written application can put your whole company in trouble. Large companies, however, have hundreds, even thousands of applications. Qualys WAS solution gives you visibility over all of them and also enables you to manage them effectively. Here are some of this app’s functions:
- Finds approved and unapproved web apps in your network with WAS’s continuous cataloging system used for identification
- Organizes your data and reports through completely customizable web application asset tagging
- Identifies apps that need patching or are a risk to the network
- Includes system hardening to meet the needs of the software
Although not an all-in-one NVS solution, WAS is a pragmatic option for web application vulnerability identification and system hardening.
5. InsightVM
Rapid7’s InsightVM is another NVS that positions itself as a live vulnerability and endpoint analytics solution to enable you to fix vulnerabilities faster. It automatically collects data from all your endpoints. This includes the data from remote workers as well. You can also use it on mission-critical assets that you can’t actively scan or are often air-gapped from the network for safety. Here’s why you need it:
- Provides risk scores that are quickly calculated for thousands of vulnerabilities and used to provide you prioritized tasks to harden the network
- Gives a real-time remediation tracker to keep all your teams in the loop of what needs to be done and by whom
- Reduces cold reports and spreadsheet tracking
- Integrates InsightVM directly into your IT ticketing system
Networks and infrastructure are constantly in flux, and InsightVM can handle the associated vulnerabilities with ease. InsightVM also integrates with cloud services and virtual infrastructure to ensure the effective hardening of your system. You get a top-level approach to vulnerability risk across your entire physical, virtual, or cloud hybrid infrastructure.
Now let’s recap!
Final Thoughts
Every network needs an NVS tool that covers scanning. Even small businesses with minimal infrastructure should still consider an NVS. This is because today’s modern networks have many diverse attack surfaces.
The proportion of lightweight applications and third-party vendor solutions also make NVS arguably more useful in smaller business environments. Still, this doesn’t mean large firms don’t benefit from NVS. The rapid scaling of larger businesses with highly integrated technologies also yields many security vulnerabilities. These businesses include operations technology (OT) and the internet of things (IoT) with its IT infrastructure.
Have more questions about network vulnerability scanners? Check out the FAQ and Resources sections below.
FAQs
What are network vulnerability scanners?
Network vulnerability scanners (NVS) look for exposed attack surfaces based on a database of known exploits. NVS do this through using invasive or non-invasive testing. Once it finds a flaw, the NVS reports it to the administrator. Some NVS also have automatic patching to help ensure software-based vulnerabilities are fixed quickly.
What’s the difference between internal and external NVS?
Network vulnerability scanners (NVS) come in 3 flavors. First, you have internal scanners that look at internal network vulnerabilities like applications. These scanners are useful in application-heavy environments. External scanners assess network perimeter vulnerabilities and protect networks with dynamic, connected device connections. Finally, environmental scanning assesses every part of the network but requires more resources to run.
When should I use a Web Application Scanner?
Web Application Scanners (WAS) are Network Vulnerability Scanners (NVS) that assess web applications hosted within a network. WAS specialization is finding vulnerabilities related to third-party code, finding patches for this code, and hardening the network around web applications hosted on the infrastructure. Activities reported and sometimes automated by the solution can include port blocking and data encryption.
Does an SME need a Network Vulnerability Scanner?
Yes, all networks need a network vulnerability scanner (NVS) to help administrators find potential attack vectors and secure them. Modern networks are complex, and it’s easy to miss something like keeping your FTP port open or allowing unencrypted traffic in some areas of the network.
How is a Network Vulnerability Scanner different from a firewall?
Fundamentally, a network vulnerability scanner (NVS) solution isn’t designed to sniff packets received on a network to find malware like a firewall. Instead, an NVS helps identify network vulnerabilities in need of patching or server-hardening activities. The idea is to also ensure that it doesn’t become compromised if a network undergoes an attack.
Resources
TechGenix: Article on Cloud Network Security
Learn how to improve your cloud network security.
TechGenix: Article on Network Automation
Learn everything you need to know about network automation.
TechGenix: Article on Network Protocols
Discover the best network protocols you’ll need for your business.
TechGenix: Article on Application Security Tools
Get better acquainted with 5 types of application security tools that can harden your system from attackers.
TechGenix: Article on Cyber-Attack Vectors
Learn more about how cybercriminals work and what attack vectors they use to exploit your system.



