
Source: Pixabay
Cloud solutions offer convenience, allow teams to collaborate within a company, and increase employee productivity. That said, cloud service providers don’t guarantee data security. They work on a shared responsibility model—they only secure cloud infrastructure. Thus, you’re responsible for securing your applications and data from cyberattacks. That’s not easy, though! Multi-cloud and hybrid-cloud environments introduce new layers of complexity. Cloud DLP (Data Loss Prevention) can help you maintain security.
In this article, I’ll discuss what cloud DLP is, why you need it, its benefits, how it works, and its best practices. First, let’s understand the what and why behind the concept!
What Is Cloud DLP?
Data loss prevention (DLP) is the practice of securing sensitive data at rest, in transit, and in use. It includes various policies and tools to protect data from loss or theft. You can also extend data loss prevention policies and tools to prevent sensitive data loss in the cloud. In addition, cloud DLP includes practices like:
- Encrypting data for transmission
- Redacting personal information before upload
- Preventing the upload of sensitive data to unauthorized cloud services
Thus, cloud DLP practices ensure transparency and protect sensitive data during upload, download, and storage in the cloud. Now, let’s look at some benefits of cloud DLP below.
Benefits of Cloud DLP
Cloud DLP provides the following benefits to your company:
- Secure integration with cloud storage providers
- Audit uploaded data and user activities
- Discover sensitive data uploaded to the cloud
- Implement automatic security controls for sensitive data on the cloud
- Alert relevant administrators of data security risks or incidents
- Provide capabilities for visibility and control into cloud ecosystems
Thus, cloud DLP plays an important role in meeting compliance requirements for data privacy and protection regulations. Next, let’s unravel 4 challenges that DLP will help you mitigate.
Why Do You Need Cloud DLP?
Every company requires data to operate efficiently. Today, most companies use cloud-based solutions to store this data. Consequently, they have multiple cloud accounts with companies like AWS, Microsoft, and Google. These companies also have private clouds with on-prem data centers creating a hybrid cloud environment. That said, cloud adoption introduces new complexities to your network infrastructure security. That’s why you need cloud DLP to mitigate these challenges. Here are some of the challenges.

Source: now.symassets.com
1. Insecure Access Control Points
Accessing cloud components, like API endpoints, from any device, poses a security risk to the cloud infrastructure. For example, attackers can exploit a compromised API endpoint to access, alter, or steal data. Cloud DLP solutions test and monitor these endpoints to restrict unauthorized access.
2. Data Breaches
Cloud infrastructures contain many settings and resources. A misconfigured resource or setting will cause a vulnerability in cloud systems. As a result, cybercriminals can also exploit this vulnerability to steal sensitive data. DLP solutions monitor all data activity and alert your security team if they notice anything unusual. They can also autoblock suspicious activity. Thus, they can limit the impact of a data breach and sometimes even stop it altogether.
3. Data Lost from Cloud
Cloud services allow you to store large volumes of data. That said, you might lose the stored data in the cloud without proper security measures. Some of these measures are data backups, audits, and risk assessments. In some cases, cybercriminals may also restrict access to your data and demand a ransom in exchange. Cloud DLP solutions let you catalog all your data so you have a central view of all data assets. In addition, they prevent unauthorized users from accessing your data.
4. Shadow IT
Shadow IT occurs when employees perform corporate tasks using unapproved IT systems. For example, an employee uses an unregistered device to access a cloud service remotely. These actions introduce security risks into the corporate infrastructure, which cybercriminals often exploit to cause a data leak. Cloud DLP limits unauthorized access to your cloud infrastructure. Thus, employees can only use the resources they have permission for. Companies also restrict general permissions even among different team members.
Now, let’s discover how a cloud DLP solution works!
How Does DLP for Cloud Work?
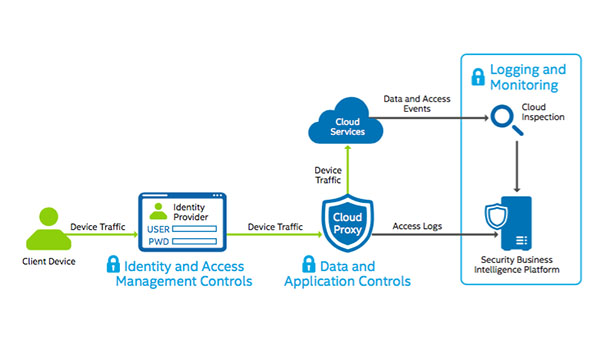
Source: connectedsocialmedia.com
Cloud DLP is a combination of technologies and best practices. These technologies typically include a central security console powered by artificial intelligence. Thus, your admins can monitor your entire cloud ecosystem from within the console. They observe your data flowing between your customers, users, and multi-cloud environments. They can also configure business rules to filter sensitive data, deploy access controls and monitor users. A cloud DLP solution has the following capabilities.
1. Data Inventory and Classification
Your DLP solution should include cloud data discovery tools with deep scanning capabilities. In essence, this helps you find critical data across all present and legacy systems. A data classification feature also lets admin users label data to determine what and where it is. Additionally, a good tool tags new data automatically to help admin users identify risks quickly.
2. Continuous Monitoring and Automated Remediation
Cloud DLP offers continuous monitoring and automated remediation. This feature lets admins know when an unauthorized person has accessed sensitive data. It can track and log all individual user activity. In addition, it includes built-in or customized policies to deal with detected security threats. Remediation capabilities come in handy to contain risks before a human response. For example, it isolates a cloud server showing malware activity.To get started with cloud DLP, you can install a solution like Proofpoint Cloud Security. That said, this isn’t enough as you have to use the technology properly for complete protection.
Let’s learn more about the 5 cloud DLP best practices below.
5 Cloud DLP Best Practices

Source: Community.broadcom.com
Cloud DLP best practices support your employees in utilizing your DLP solution correctly. Here are the 5 best practices for cloud DLP.
1. Create A Data Catalog
You can use the tool to group and categorize all your cloud data. For example, you may have customer data, employee data, product data, etc. A complete inventory of data assets on the cloud helps to save time. Thus, users can easily see the company’s data assets and where it stores them.
2. Prioritize Sensitive Content
Different data assets have varying degrees of importance. Management must set up company-wide policies to classify and prioritize data categories for security. For example, you may decide to redact all personal information from highly sensitive data before uploading it to the cloud. You may then classify customer data and employee data as highly sensitive. Thus, the tool will automatically reduce personal information from these two data sets before uploading it to the cloud. In essence, this practice ensures consistency in your data management.
3. Define User Groups
Admins should define user groups, like admin users, external conductors, etc., based on DLP policies. These user groups support security implementation. You can then configure firewalls and restrict file-sharing and email forwarding according to group levels. For example, admin users can share files, but external contractors can’t.
4. Apply Zero-Trust Encryption
Zero-trust encryption is a feature you can enable for specific data sets. Essentially, it prevents unauthorized parties from accessing sensitive content over the network. It also scrambles data on the network so no one can spy on the data during transit. In addition, this practice is very handy in preventing man-in-the-middle attacks.
5. Monitor User and Application Behaviors
Companies must use advanced detection engines like User and Entity Behavior Analytics (UEBA). UEBA monitors user, device, and application behavior. It also identifies suspicious user activity and prevents access to compromised data.
Now that you’ve learned about cloud DLP and the best practices for implementing it, let’s wrap up.
Final Words
Companies relying on the cloud must use cloud DLP to ensure data security. Otherwise, they’ll face significant risks like data theft, malware from Shadow IT, and data loss. Cloud DLP enables visibility and helps your company meet compliance with data security regulations.
That said, installing the technologies isn’t enough on its own. You must also follow cloud DLP best practices to utilize the solution comprehensively. Your company can then enjoy the benefits of cloud services without the associated risks!
To learn more about cloud DLP, read the FAQ and Resources sections below!
FAQ
What is cloud security?
Cloud security is a collection of methods and techniques to secure cloud infrastructure. It includes data security and privacy across cloud-based systems, apps, and infrastructure. Both cloud service providers and the clients using these services are responsible for cloud security. Additionally, cloud security helps counter companies’ internal and external risks in the cloud.
What is a cloud DLP service?
A DLP for cloud service is a managed service that helps care for your cloud DLP needs. These services also have many features that discover, classify, and protect your sensitive data on the cloud. In addition, they allow you to set policies that protect your sensitive data and your network’s health.
What problems does cloud DLP solve?
DLP for the cloud solves some problems that traditional DLP can’t. First, it simplifies DLP deployment. Cloud DLP services embed data protection into a company’s existing cloud infrastructure. It also improves accuracy. In addition, these services combine various information to help companies make informed choices. Finally, cloud DLP facilitates effective mitigation of cybersecurity risks.
Who needs cloud DLP?
You need cloud DLP if your company stores or transmits sensitive data on the cloud. Cloud DLP helps ensure this sensitive data’s safety and prevent cyber attacks. That said, cloud DLP is unnecessary if your company doesn’t work on the cloud. It’s also unnecessary if you only transmit non-sensitive information on the cloud.
What are some limitations of cloud DLP services?
Most cloud DLP solutions can work with any cloud environment and configuration. That said, they have some limitations. For example, some managed detection and response (MDR) services work only with a specific public cloud. If you store data on multiple clouds, you can’t protect all your data with a single DLP tool.
Resources
TechGenix: Newsletters
Subscribe to our newsletters for more quality content.
TechGenix: Article on Data Loss Prevention Policy
Learn how to create a data loss prevention policy for OneDrive for business.
TechGenix: Article on Cloud Security
Read about the top cloud security standards to leverage for your business.
TechGenix: Article on Cloud Data Safety
Explore some tips to ensure cloud data safety.
TechGenix: Article on Data Protection and Security
Discover how data protection and security are essential for your company.



