
Server virtualization platforms (like Microsoft’s Hyper-V) made creating new virtual machines simple. It’s important to remember the best practices you should adhere to when creating new virtual machines. This is especially true when virtualizing domain controllers.
You can create a domain controller similarly to any other virtual server. That said, Microsoft recommends creating virtual domain controllers in a way that provides higher levels of security and reliability.
In this article, I’ll share 4 common mistakes you should avoid when virtualizing domain controllers.
4 Common Mistakes to Avoid When Virtualizing Domain Controllers
Virtualizing domain controllers need configuration for extra security and reliability. That said, you may face some obstacles in the process. Here are 4 common mistakes to avoid when virtualizing domain controllers.
1. Depending Too Heavily on Virtualization
Although somewhat ironic, one of the most common mistakes with virtualized domain controllers is relying too heavily on virtualization. This increases the risk of virtualization platform malfunction. In return, a malfunction will affect all host systems using the platform.
Microsoft recommends having at least one physical domain controller for each domain. That way, a domain controller will still be functional even if the entire virtualization platform fails. You’ll also avoid unnecessary risks and reduce the impact of a huge failure.
2. Forgetting about Trust Boundaries
In a large company, it’s extremely rare for a single administrator to oversee everything. Instead, admins are generally responsible for one particular aspect of the company’s infrastructure. For example, you’ll have virtualization admins and storage admins oversee their areas of responsibility.
This model somewhat breaks down after virtualizing domain controllers. According to Microsoft, “The administrator on the host computer has the same access as a domain administrator on the writable domain controller guest and must be treated as such.”
This and other similar trust issues have led some companies to deploy dedicated Hyper-V clusters. Such clusters only run domain controllers and other tier 1 assets. The Active Directory team also manages them instead of the virtualization team.
3. Using the Wrong Type of Disk
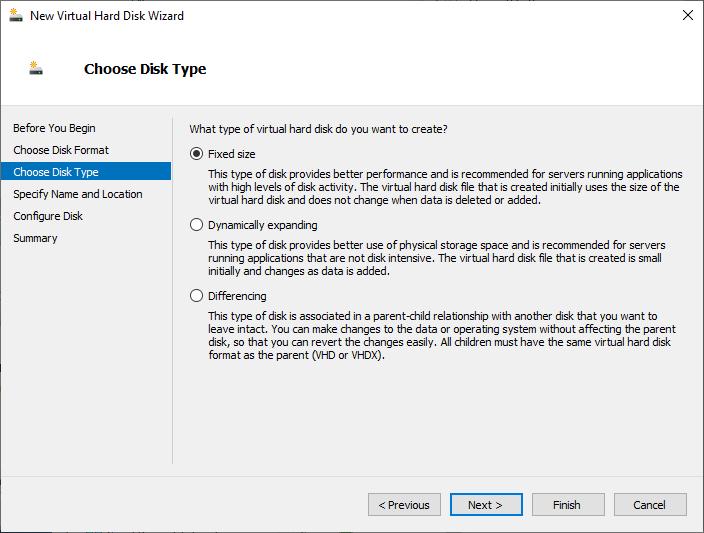
When setting up a virtualized domain controller, it’s essential to consider the virtual hard disk configuration. One of Microsoft’s best practices is to avoid using differencing disks.
Differencing disks, like dynamically expanding virtual hard disks, can sometimes experience performance issues. More importantly, differencing disks also make it easy to roll the VM back to a previous state accidentally.
When virtualizing domain controllers, you should create fixed-size virtual hard disks. Although such disks initially consume more space than dynamically expanding disks, they offer better overall performance.
Microsoft also recommends using virtual SCSI disks rather than IDE disks. This means you should create domain controllers as Generation 2 VMs.
4. Avoiding Cloning and Rollbacks
Virtualization platforms like Hyper-V facilitate cloning a virtual machine. They also facilitate using snapshots and other mechanisms to roll a VM back to an earlier state without restoring a backup. That said, this can cause severe problems for virtualized domain controllers.
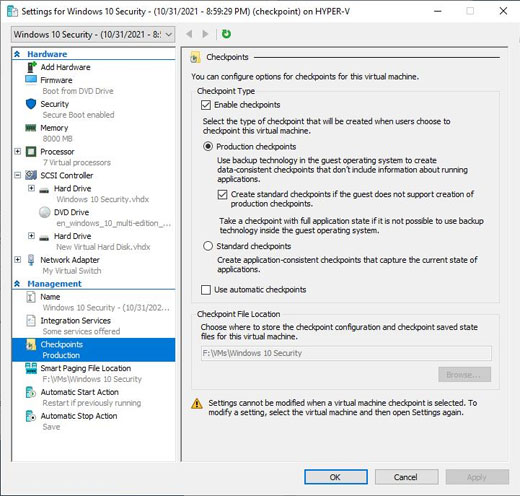
As a general rule, you should never take a checkpoint of a virtualized domain controller. You also shouldn’t export a domain controller or attempt to clone or copy the VM. Similarly, you should never pause a virtual domain controller for longer than its tombstone TTL value.
These actions can potentially lead to a situation that would cause a rollback to occur. A rollback causes domain controllers to fall out of sync, eventually causing Active Directory replication to fail.
The Bottom Line
When it comes to virtualizing domain controllers, it’s essential to configure them for security and reliability. You must also take steps to prevent a rollback from occurring since such an event could break AD replication. This will ensure a successful virtualization process.
In this article, I explained four of the most common mistakes you might face when virtualizing domain controllers. I also provided tips on how to avoid each of these mistakes.
Got more questions about virtualizing domain controllers? Check out the FAQ and Resources sections below.
FAQ
What is a USN rollback?
A USN rollback is a condition that can occur when you revert a domain controller to a previous state through any method other than a supported backup restoration. In return, this will also stop replication or cause many errors. Read here to learn more about how to detect USN rollback.
What Active Directory infrastructure components require special care when virtualized?
You need to configure domain controllers in a way that gives them more security and reliability than most other virtual servers. That said, domain controllers can’t function without DNS, so you should give special care to DNS servers. Similarly, Azure AD Connect servers should also receive the same care as domain controllers.
What are the best practices for the virtual domain controller clocks?
Virtual servers mostly synchronize their clocks to the Hyper-V host. That said, hosts can have their clocks set differently from one another. The Active Directory depends on accurate time, so you should disable the Time Synchronization integration service. You should also synchronize domain controllers to an NTP server instead.
Can I fix the USN rollback of a domain controller if it occurs?
Yes, you can. The process involves transferring FSMO roles (if necessary), demoting the domain controller, and re-promoting it. This is also one of the many reasons why it’s so important to have multiple domain controllers for each domain.
Can the Hyper-V shield VM feature help with domain controller security?
The Hyper-V shielded VM feature makes virtual machines authorized to run on certain hosts only. If you move a virtual hard disk elsewhere, it’ll be encrypted and can’t be read or mounted. This feature can also help with domain controller security. That said, you should implement it in a way that avoids single points of failure.
Resources
TechGenix: Article on Virtual Domain Controllers
Learn how to prevent a virtual domain controller from syncing its time against a host here.
TechGenix: Article on Keeping Your Domain Controllers Up-To-Date
Read more on how to keep your domain controllers up to date here.
TechGenix: Article on Virtualized Domain Controllers in a Hyper-V Replica Environment
Find out about virtualized domain controllers in a Hyper-V replica environment here.
Microsoft: Article on Virtualizing Domain Controllers on Hyper-V
Read Microsoft’s best practices for virtualizing domain controllers on Hyper-V here.
Microsoft: Article on Techniques for Troubleshooting Virtualized Domain Controllers
Discover techniques for troubleshooting virtualized domain controllers here.



