
Source: Pixabay
A Trend Micro investigation revealed that the “port forwarding” feature within GitHub Codespaces could allow cybercriminals to host and deliver malware. The researchers found that it’s possible to exploit the public sharing of forward ports to create a malware server. To do this, threat actors need a legitimate GitHub account to avoid getting flagged as suspicious. However, no incident exploiting the security vulnerability has occurred in the wild so far.
GitHub Codespaces, available since Nov. 2022, has been a popular choice among developers and large tech companies. It provides them with a container-based environment equipped with tools and dependencies for completing projects. Developers deploy Integrated Development Environment (IDE) platforms inside these virtual containers. This allows them to write, edit, and test code directly within the web browser.
GitHub Codespaces has over 94 million developer accounts and is used by large companies such as DuoLingo and Vanta. Upon registering, each developer gets to create at least two codespace instances for free.
GitHub Codespaces Public Port Vulnerability
Source: Trend Micro
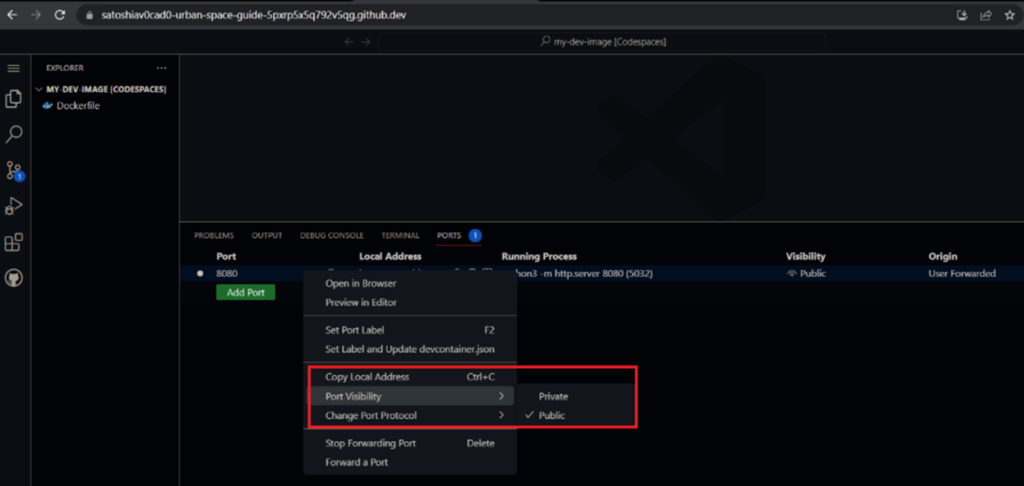
While private ports forwarding requires cookies or tokens for authentication, a public port is available to just about anybody with access to the URL. According to Trend Micro’s investigation, the trouble with GitHub Codespaces is that when it allows public port forwarding via Transmission Control Protocol (TCP) for users to view and test applications, it also allows cybercriminals a means of entry.
This enables threat actors to bypass suspicion from threat intelligence platforms. On GitHub Codespaces, ports are forwarded using HTTP. HTTP is less secure than HTTPS. With no malicious history showing, the malware flies under the radar. In Trend Micro’s simulated attack, researchers forwarded the port 8000 using forwardPorts property. Then, they ran a Python-based HTTP server on each successful container startup using the postStartCommand property.
Consequently, the researchers demonstrated how a cybercriminal could run a Python web server, upload malicious scripts to Codespace, and open a public web server port. After that, they used the URL to distribute malware to end users. Throughout the process, GitHub Codespaces didn’t start any authentication procedures.
This process is similar to how cybercriminals distribute malware on other reputable services, such as Microsoft Azure, Google Cloud, and Amazon AWS.
Using Dev Containers to Enhance Efficiency
Source: Trend Micro
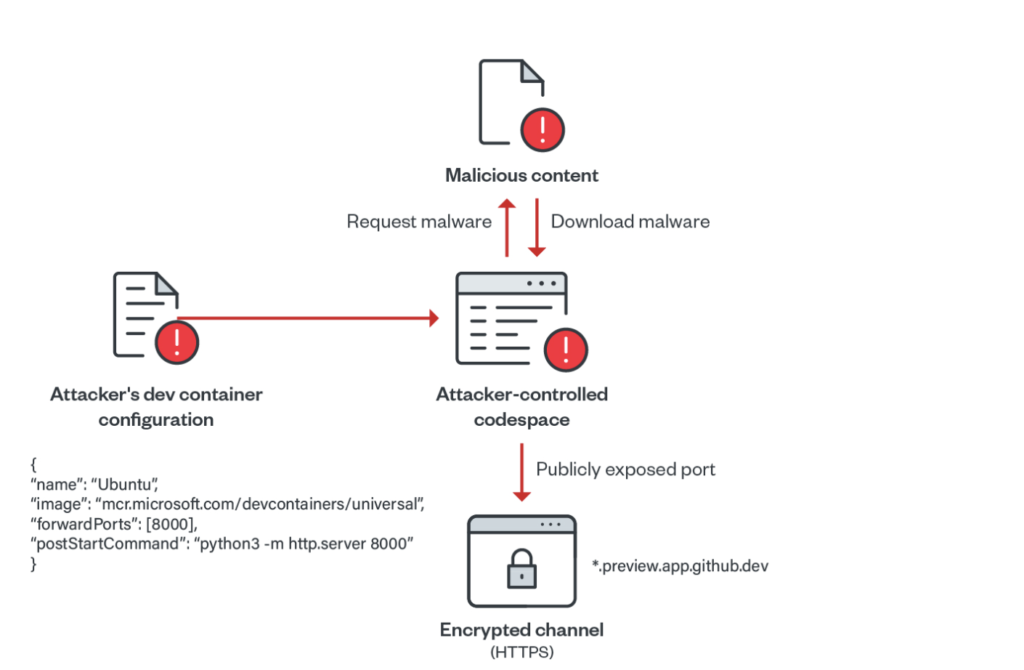
Since dev containers within GitHub have all the tools and dependencies used in projects, developers have come to rely on them for rapid deployment. But, at the same time, the same dev containers also help cybercriminals create a malicious web server on GitHub Codespaces within minutes, with zero checks.
“Using such scripts, attackers can easily abuse GitHub Codespaces in serving malicious content at a rapid rate by exposing ports publicly on their codespace environments. Since each created codespace has a unique identifier, the subdomain associated is also unique. This gives the attacker enough ground to create different instances of open directories,” read the Trend Micro report.
Usually, the platform deletes codespaces within 30 days, allowing threat actors a month to use a URL. While this particular security vulnerability hasn’t been exploited yet, cybercriminals will waste no time once they’ve figured it out. Their predilection for exploiting free services, such as Dropbox, GitHub, Azure, OneDrive, and more, is well-known and documented. Sadly, these vulnerabilities expose unsuspecting users to the possibility of downloading malware from these platforms.
GitHub Under Fire
Source: GitHub Codespaces
In recent years, GitHub has dealt with a spate of cybercrimes directed toward it. Part of this is due to its growing size and popularity, making it an attractive target for cybercriminals. In response, GitHub is upgrading its security features to deal with these threats. The latest among these actions is GitHub’s step in making 2FA and free secret scanning mandatory for all users.
As companies unwarily leave access to their code open to the public on GitHub, they’ve been left reeling from the fallout. For instance, Toyota left a publicly available access key on GitHub for 5 years. They later regretted it when cybercriminals compromised the personal information of 296,000 of its customers.
Similarly, in January 2021, Nissan North America experienced a breach where cybercriminals exposed 20 GB of sensitive information. The security breach occurred due to default access credentials on a Git server (Git is not the same as GitHub, but has similar features). Moreover, in December 2022, Okta authentication provider was targeted via GitHub repositories — but these were private, not public, repositories.
Business owners who manage software teams must secure the environment where developers contribute code. Preferably, They can do this with some form of multi-factor authentication (MFA) for all commits to restrict access. In addition, businesses must set ports to private — a practice that will reduce the variety of possible attack vectors. These are simple solutions that work like a charm against many lethal threats. Leaving an open public port is a rookie mistake, but it’s often the obvious cause of serious compromises.
Software Development Environments Need to Step Up
The lesson here is that user authentication should be paramount. It’ll help avoid the consequences emanating from a leak at the top of the software supply chain that can cascade to users and organizations all the way down the line.
Even though cookies and tokens can make it harder for cybercriminals to breach such spaces, multi-factor authentication (MFA) vastly increases web security. This shows why businesses should take pains in implementing additional security protocols. Ultimately, passkeys will have to replace clunky passwords and MFA in the software world. Nothing at the moment is as important as this shift in the industry, which can finally stem the tide of cybercrime.



