
Source: Unsplash
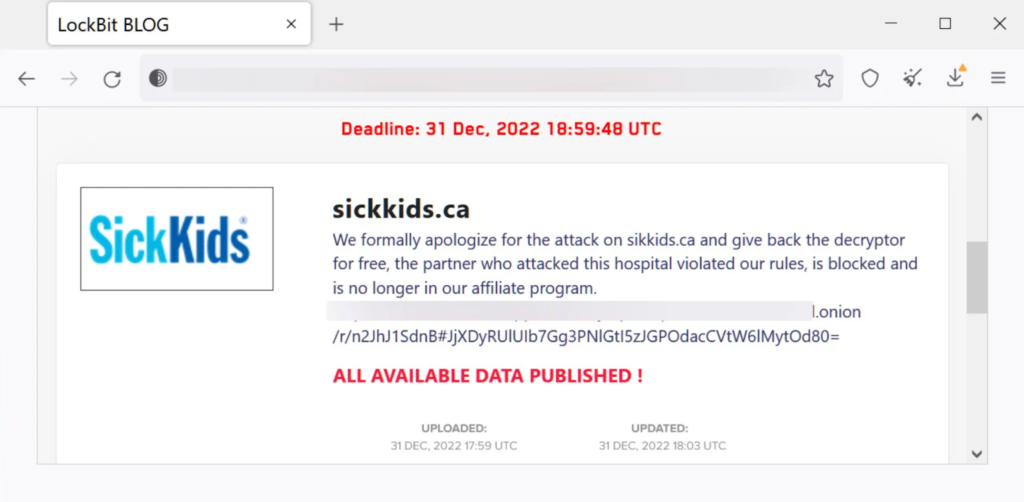
After LockBit encrypted information in an attack on the Hospital for Sick Children (SickKids) in Toronto on Dec.18, it has tendered an apology and a free decryptor to the hospital. LockBit has come out against the attack, calling it a violation of its terms of service by an affiliate, and said it doesn’t target institutions where a compromise “could lead to death.” By Jan. 1, SickKids had restored 60% of its operations.
The hospital was forced to declare “System Failure” under its code “Grey”. Despite disrupting hospital phone lines and web pages, the breach didn’t affect patient care. Attempting to ease privacy concerns from such attacks, the hospital claimed the cybercriminals didn’t steal any sensitive patient information — a rarity in such cases.
The decryptor, which includes Linux/VMware ESXi, suggests that the attack could only encrypt virtual machines on the hospital’s network, and no Windows machines were compromised.
LockBit’s Ransomware-as-a-Service Model
Source: Bleeping Computer
LockBit operates a ransomware-as-a-Service (Raas) model. This enables it to lend the software to affiliates whose job is to use the software to penetrate networks and perform operations. At the same time, LockBit itself only has to maintain the encryptors, decryptors, and websites. These affiliates pocket 20-25% of the profits on each extortion.
Once the cybercriminals encrypt a server, they hold it for ransom, refusing to decrypt it unless the victims make the payment. Mostly, a payment results in server and file decryption. Cybercrime groups run on commercial principles, so they have to keep up their end of the bargain.
LockBit, under its terms, forbids encrypting medical data. Nonetheless, it delayed the release of the decryptor in this case. Yet, the same terms and conditions haven’t stopped its affiliates from breaching hospitals in the past. In August, LockBit affiliates compromised the Center Hospitalier Sud Francilien (CHSF) in France and demanded $10 million in ransom. The group leaked staff and patient data online when the hospital failed to meet its demands.
It seems as if these terms and conditions allow LockBit to keep its distance from affiliates in case its vigilante reputation is at stake. It could plead deniability and sever relations with the affiliate if the attack doesn’t go down well. By lending its ransomware, it can just stay back and lurk in the shadows.
The ransomware it has developed is automated and easy to use. Once it infects a single host on a network, the virus spreads to other hosts on autopilot. It also automatically completes post-exploitation procedures, such as the escalation of privileges.
LockBit Protection — Staying Safe in the World of Ransomware

Source: Unsplash
According to Blackberry, LockBit is one of the most active ransomware strains worldwide. With its ransom demands averaging at about $85,000 per victim, it’s safe to assume that the group mainly targets small to medium-sized enterprises. However, it has also compromised large federal and commercial organizations, demanding ransoms in the millions of dollars.
Blackberry research explained how LockBit works: “LockBit seeks initial access to target networks primarily through purchased access, unpatched vulnerabilities, insider access, and zero-day exploits. Second-stage LockBit establishes control of a victim’s system, collects network information, and achieves primary goals such as stealing and encrypting data.”
Knowing these patterns, network administrators can devise their defense mechanisms. Above all, a well-rounded cybersecurity strategy that offers robust protection can thwart any cybercrime group, including LockBit. Networks need high-quality antivirus protection as well as sensitive malware detection systems. Bear in mind that not every security product is made equal — some are far better than others at detecting and preventing infections.
Better still, network administrators should encourage the use of multifactor authentication across as many services as possible. These vastly reduce the risks of network penetration. For employees, administrators should lay down clear guidelines for changing passwords. Further, they should use automatic patch management that can routinely identify and patch vulnerabilities as they arise. Lastly, reduce user privileges on the network to a functional bare minimum.
The Continual Critical Infrastructure Threat
Source: The Bleeping Computer
As highlighted earlier, hospitals continue to be soft targets for cybercriminals. On Christmas, cyberattacks hit the administrative registrars of six counties in North Carolina. As a result of the attack, processing and access to wills, birth certificates, death certificates, marriage licenses, and other governmental procedures have slowed down or halted completely. Local governments have been reduced to using pen and paper, causing operational efficiency to nosedive.
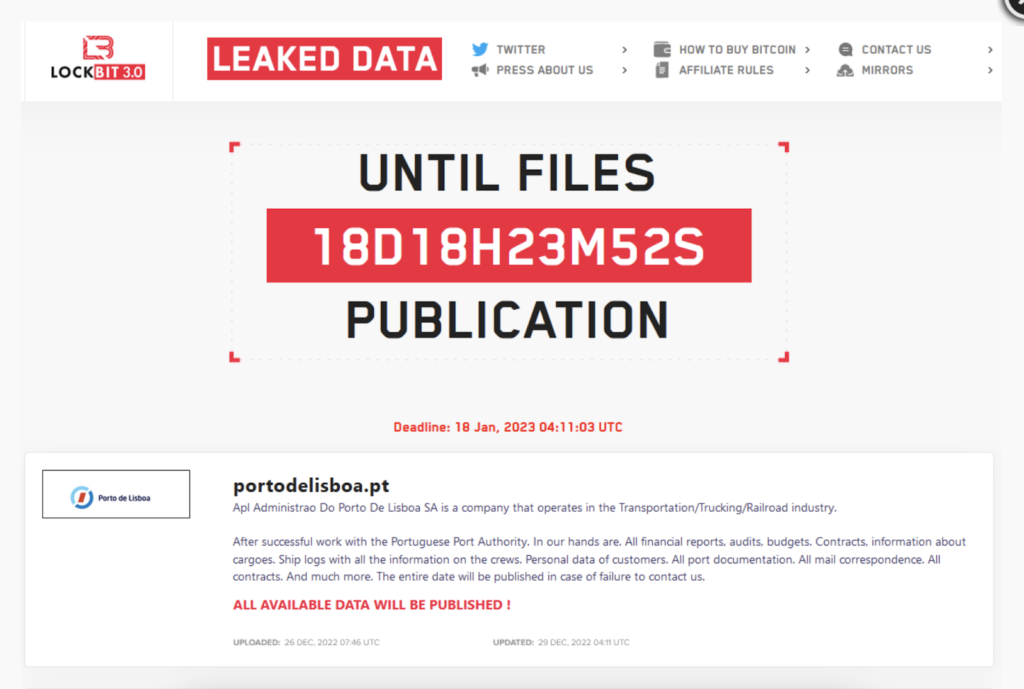
LockBit was also busy on Christmas launching an attack on the Port of Lisbon Administration (APL). The Port of Lisbon is a key European port, serving a variety of ships from various countries arriving at its harbors. Currently, the APL website (http://portodelisboa.pt) is offline. LockBit added the APL to its ransomware website on Dec. 29. While the port is operational, the cybercrime gang claims to have accessed financial reports, audits, budgets, contracts, cargo information, ship logs, crew details, customer PII (personally identifiable information), port documentation, email correspondence, and more.
In Canada, a cyberattack on Dec. 27 shut down the Canadian Copper Mountain Mining Corporation (CMMC) in British Columbia, though no details have been disclosed yet. CMMC is an 18,000-acre estate, producing 100 million pounds of copper on average per year.
Hospitals Are an Ongoing Target for Ransomware Operations
Despite the odd compassionate turn in tendering an apology and offering decryption, LockBit and other cybercrime groups like it continue to target hospitals. Recently, a Hive ransomware attack exposed 270,000 patient records at Lake Charles Memorial Hospital.
In another incident, an attack on CommonSpirit Health — a chain of over 150 hospitals — exposed over 600,000 patients’ data. Hospitals are easy targets and contain vast repositories of patient information. From 24 healthcare exploits in 2022, cybercriminals obtained Protected Health Information (PHI) in over 71% of the cases. Poor data protection procedures coupled with sensitive data and many avenues for exploitation make healthcare systems extremely vulnerable and sensitive targets.



